Key distribution and reconstruction method and device based on mobile internet
A technology for key distribution and mobile interconnection, which is applied in security devices, electrical components, wireless communication, etc., and can solve problems such as implementation in an interconnected environment.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0090] The principle of the present invention is as follows,
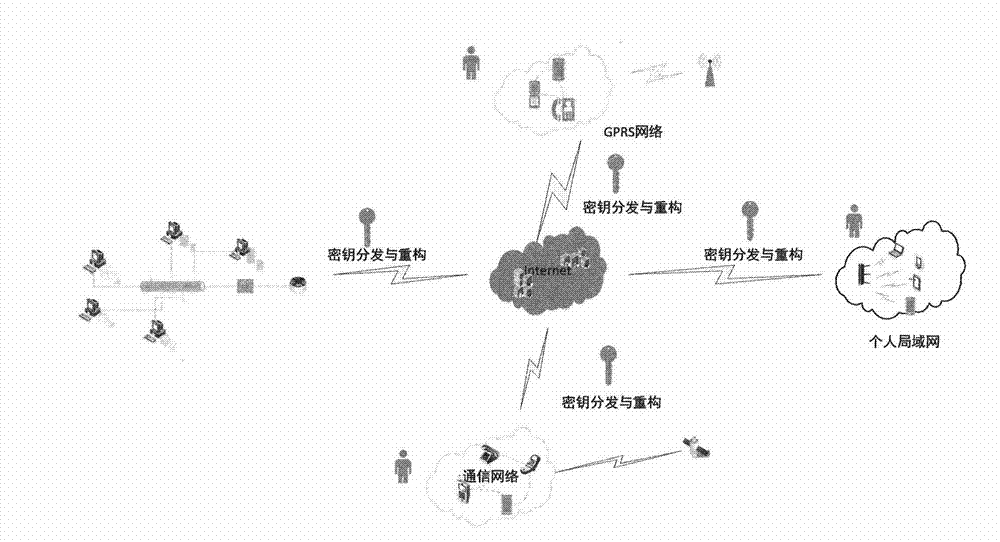
[0091]With the increasing proportion of the application of mobile Internet and cryptographic protocols in national production and life, the research of this program will greatly improve the security and usability of mobile Internet, which can be used to solve the problem of encryption in the mobile Internet environment. It provides a new solution to the key sharing problem, provides a theoretical and technical basis for enriching and improving rational cryptographic protocols, and has a far-reaching impact on national economic and social development. The network topology of the rational key sharing scheme in the mobile Internet environment is as follows: figure 1 shown.
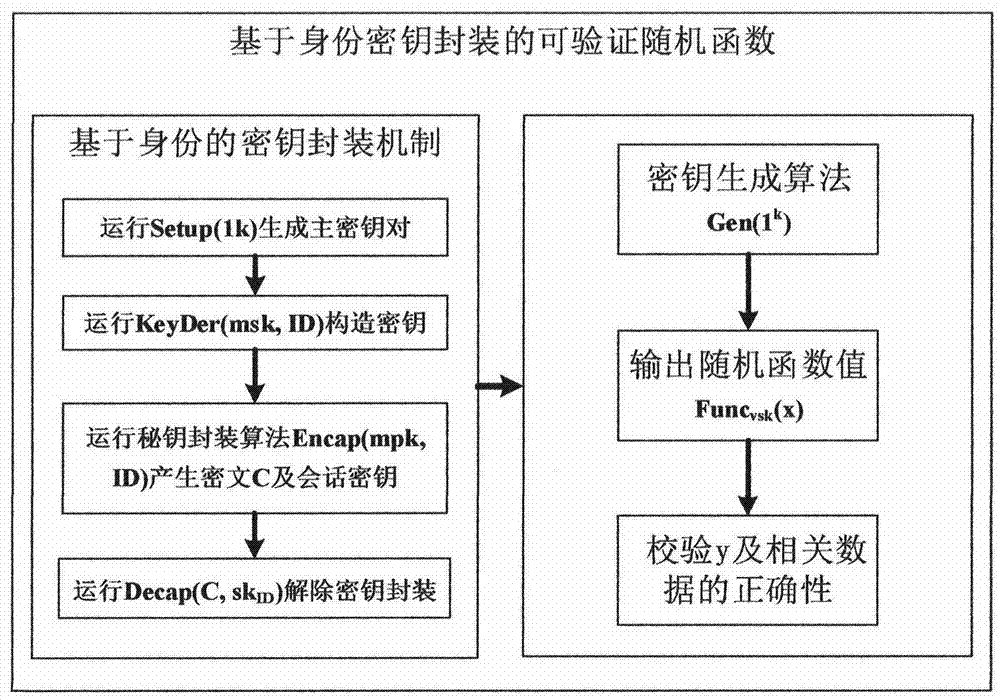
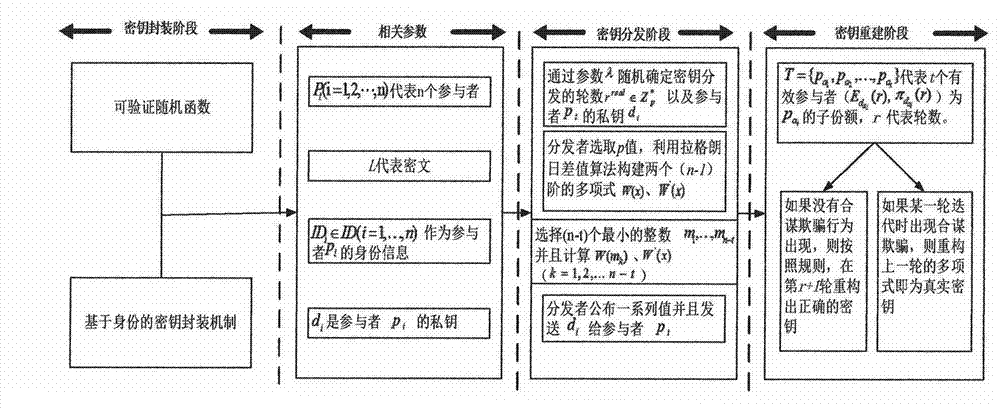
[0092] This patent first studies the identity-based key encapsulation mechanism suitable for verifiable random functions, and designs a rational key sharing protocol that does not require public key infrastructure, so that the technical solution ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com