A security optimization method for multi-cluster hadoop system based on public key algorithm and ssl protocol
A technology of public key algorithm and optimization method, which is applied in the field of optimization and can solve problems such as reducing efficiency and tediousness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
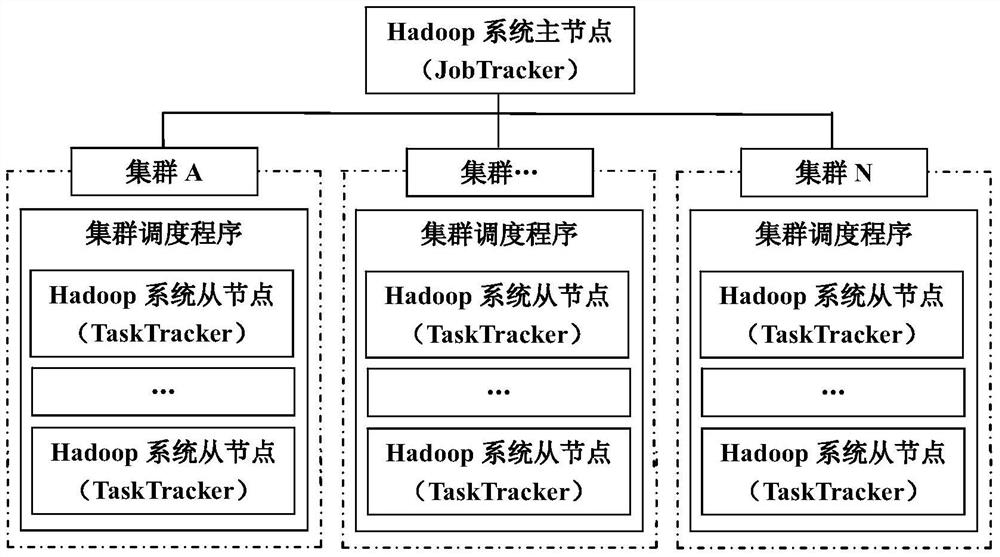
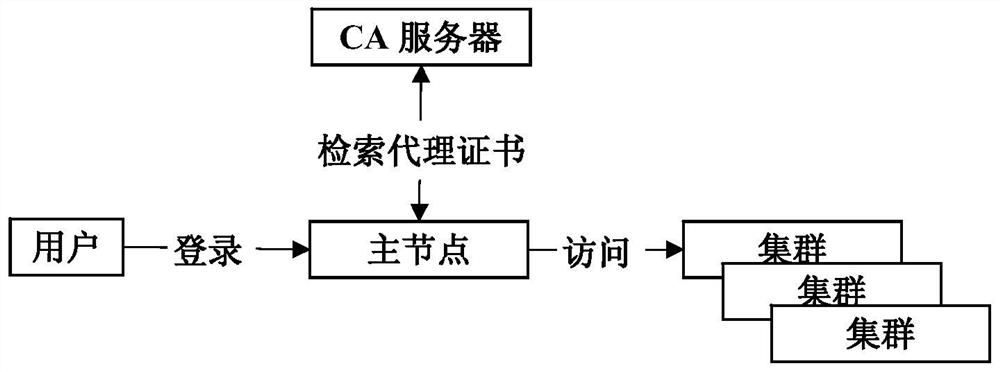
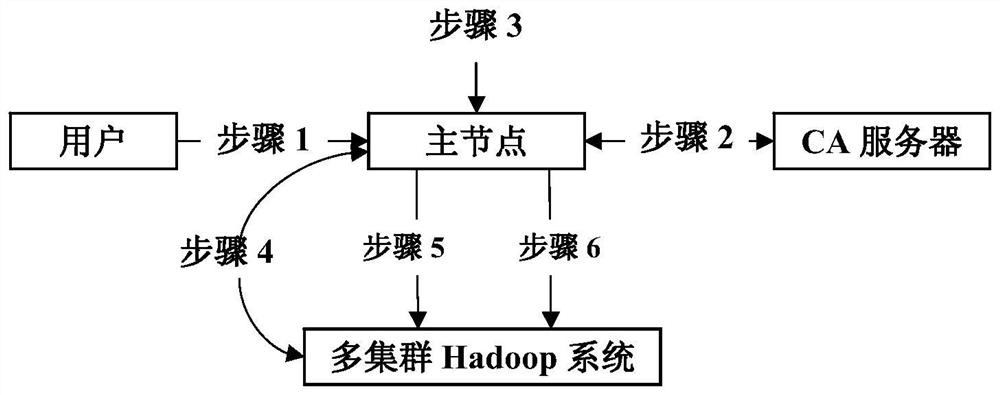
[0142] The security optimization method proposed by the present invention is implemented as a single plug-in in a multi-cluster Hadoop system in a single-sign-on manner, and can be started by a SHELL device of the multi-cluster Hadoop system. The developed prototype system can be flexibly integrated into or offloaded from the multi-cluster Hadoop system according to the needs of users. The prototype system of the safety optimization method proposed by the present invention includes six main modules: a general module, a security module, a user management module, a CA node module, a master node module and a slave node module. Figure 5 The interaction between the various modules is shown. Each module provides specific functionality, among them:
[0143] (1) The general module is the function library of the security optimization method, which provides the required basic interfaces for other modules, including event listeners, event processors and random message generators, etc.;...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com