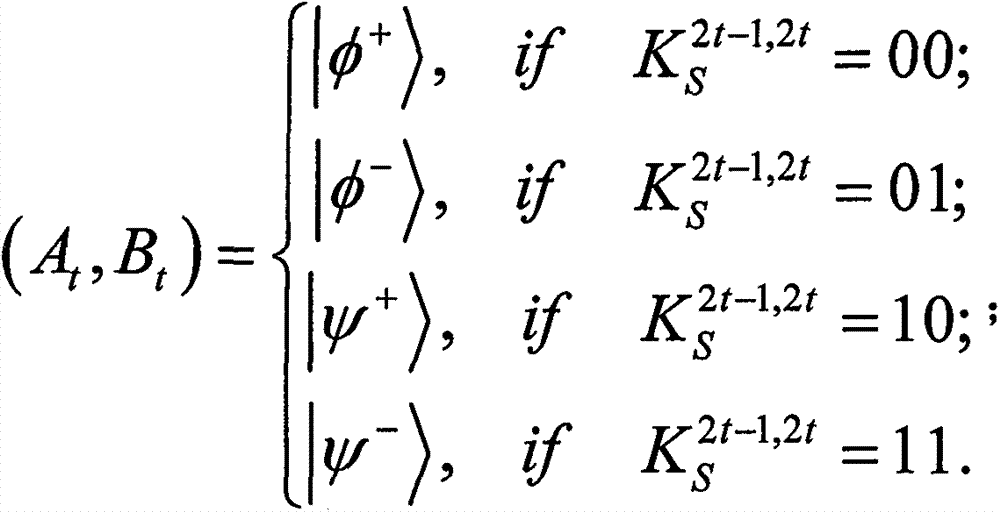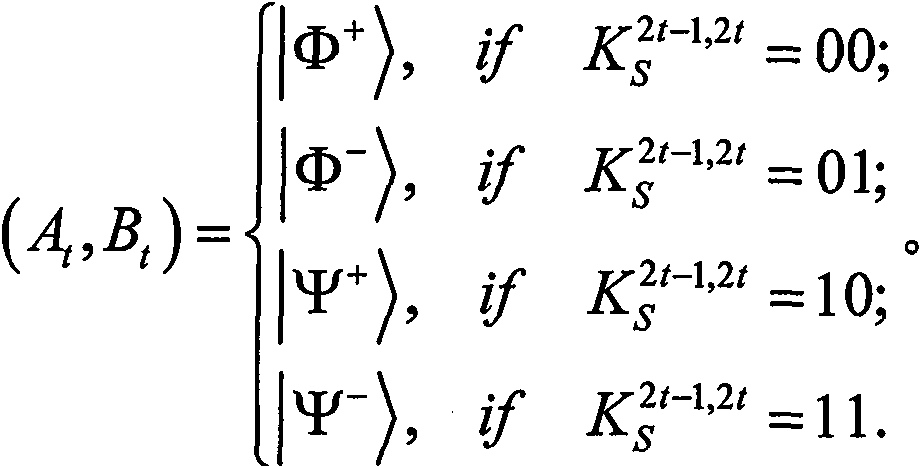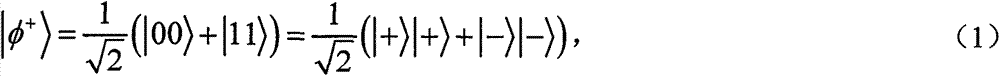Quantum authentication encryption method based on two-photon entanglement state suitable for quantum email
A technology for authenticating encryption and entangled states, applied in the field of quantum secure communication, to achieve the effect of high efficiency of information theory
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
[0099] 1. Application example of quantum authentication encryption method
[0100] With the first two-photon entangled state (A 1 , B 1 ) as a concrete example to further explain the proposed method. suppose and (i 1 , j 1 )=01. Correspondingly, (A 1 , B 1 ) is prepared by Alice at |ψ + >. Thus, in Alice's unitary operation σ x After, (A 1 , B 1 ) is changed to |φ + >. Then, after receiving it from Alice, according to Bob chooses MB 1 Measure it. Thus, according to Table 1, he can read (i 1 , j 1 )=01, because he started from and Knowing that Alice prepared (A 1 , B 1 ) initial state is |ψ + >. After decoding M', Bob compares h(m' A ) and h′(m A ) can authenticate m′ A integrity.
[0101] 2. Discussion
[0102] (1) Information theory efficiency
[0103] The information theory efficiency defined by Cabello [4] is η=n s / (q t +b t ), where b s ,q t and b t are the number of secret bits expected to be received, the number of qubits used, an...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com