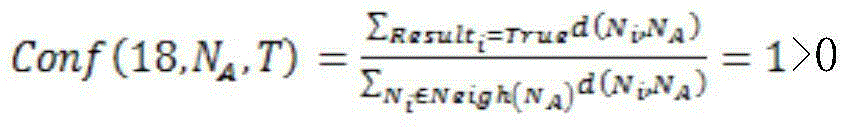Internet-of-things tampering invasion detection method in combination with abnormal monitoring
An intrusion detection and anomaly monitoring technology, applied in data exchange networks, digital transmission systems, electrical components, etc., can solve problems such as tampering with perceived data and destroying data credibility.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] The invention includes local anomaly monitoring, neighbor intrusion detection and global intrusion detection, and the three are combined to realize alarming and positioning of abnormal events, as well as tampering intrusion detection.
[0036]In order to achieve the above purpose, the present invention proposes a three-dimensional, time-space and data-based intrusion detection method for the Internet of Things. Nodes in the network are both sensing nodes and detection nodes. The intrusion detection module is deployed on consoles and nodes, and both include two functions: passive intrusion detection and active intrusion detection. Consider the scenario of periodic environmental monitoring of the Internet of Things. Nodes monitor the environment in a certain period and send monitoring data to the only base station Sink in the network. The disclosure of monitoring data does not need to protect privacy. There are malicious nodes in the network. This patent focuses on the d...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com