Unlocking method and device of intelligent terminal
A smart terminal and unlocking device technology, applied in the input/output process of data processing, instruments, digital data authentication, etc., can solve the problems of damaging the smart terminal, beautiful display screen and cumbersome password input process, so as to avoid interference, Convenient unlocking and hidden action effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
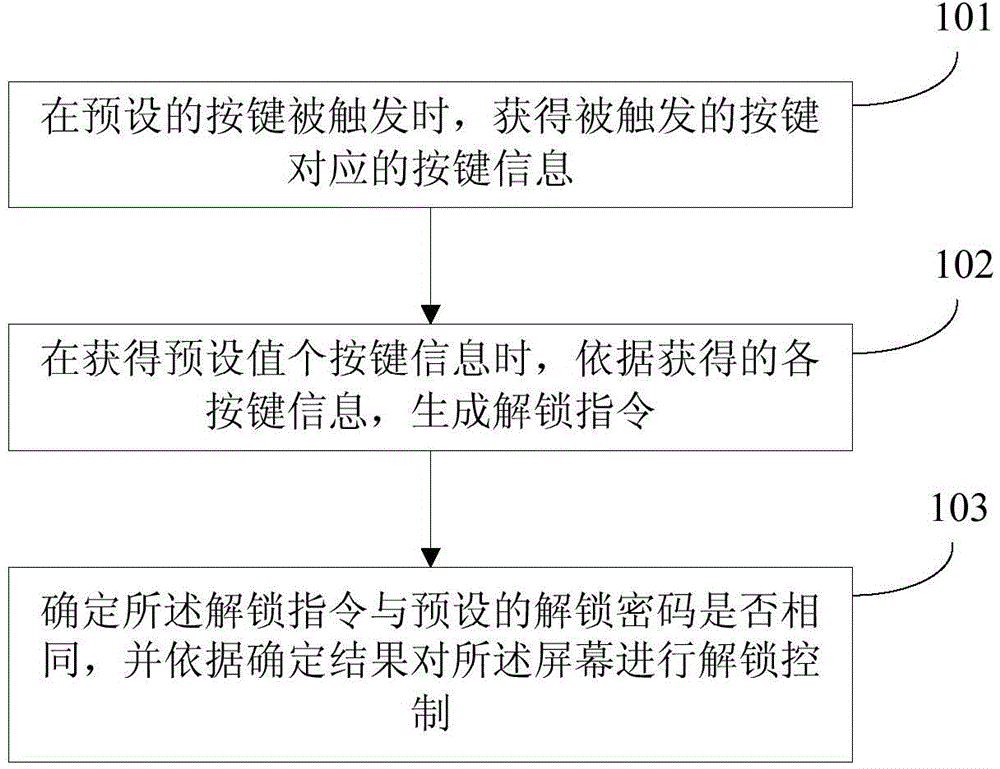
[0020] figure 1 It is a schematic flowchart of an unlocking method for a smart terminal provided in Embodiment 1 of the present invention. The method can be executed by an unlocking device for a smart terminal, wherein the device can be implemented by software and / or hardware, and can be built into the smart terminal as a part of the smart terminal middle. Such as figure 1 As shown, the method includes:
[0021] Step 101. When a preset key is triggered, obtain key information corresponding to the triggered key.
[0022] On smart terminals represented by tablet computers and smart phones, there are usually many keys, including virtual keys and physical keys. In the embodiment of the present invention, any keys on the smart terminal are used as unlocking keys, these keys are determined as preset keys, and when these keys are triggered, that is, when a virtual key is clicked or a physical key is pressed, the corresponding The key information unlocks the smart terminal, and wh...
Embodiment 2
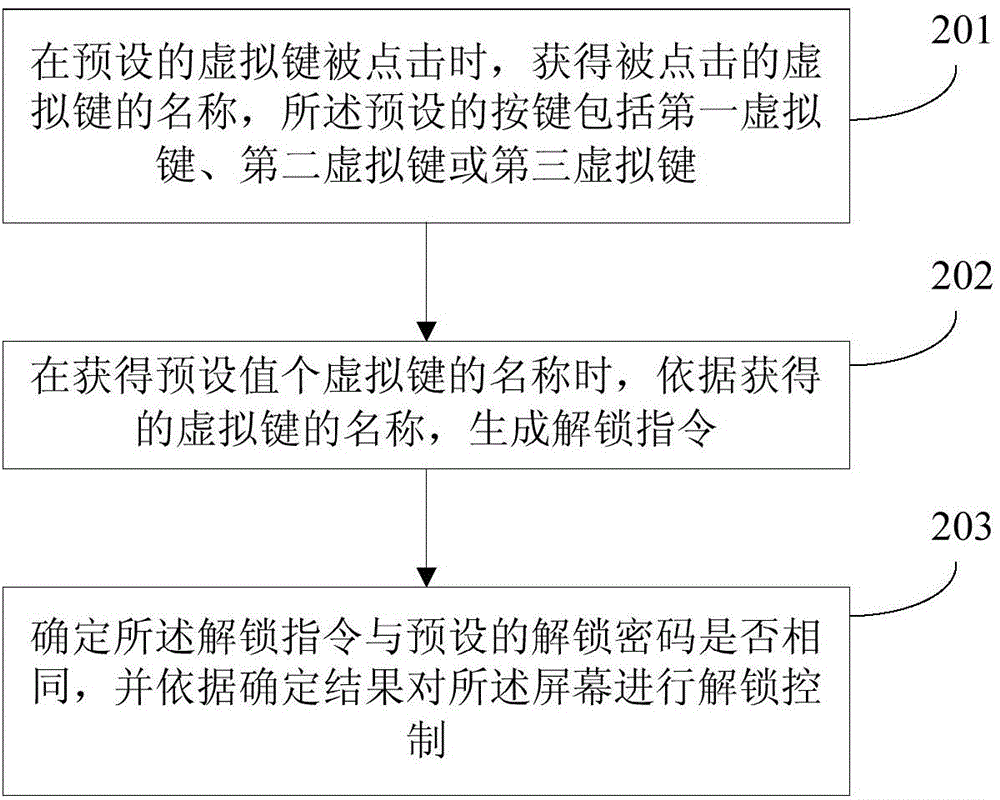
[0033] figure 2 It is a schematic flowchart of an unlocking method for a smart terminal provided in Embodiment 2 of the present invention. The method can be executed by an unlocking device for a smart terminal, wherein the device can be implemented by software and / or hardware, and can be built into the smart terminal as a part of the smart terminal middle. Such as figure 2 As shown, the method includes:
[0034] Step 201. Obtain the name of the clicked virtual key when a preset virtual key is clicked, and the preset key includes a first virtual key, a second virtual key or a third virtual key.
[0035] Smart terminals are generally equipped with virtual keys. Taking a smart phone with an Android system installed as an example, there are generally virtual keys at the bottom of the display screen, which can be a virtual return key, a virtual home key or a virtual menu key. It should be noted that different smartphones have different specific key designs, and some smartphone...
Embodiment 3
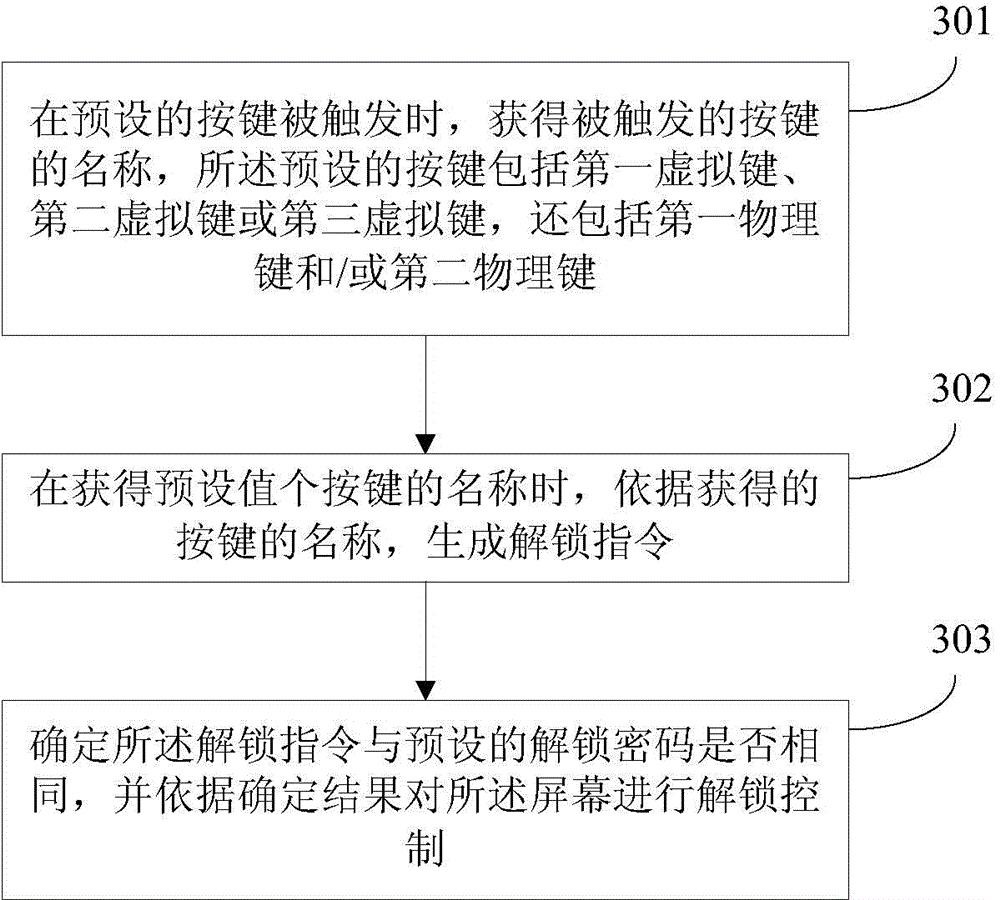
[0048] image 3 It is a schematic flowchart of an unlocking method for a smart terminal provided in Embodiment 3 of the present invention. The method can be executed by an unlocking device for a smart terminal, wherein the device can be implemented by software and / or hardware, and can be built into the smart terminal as a part of the smart terminal middle. Such as image 3 As shown, the method includes:
[0049] Step 301. Obtain the name of the triggered key when the preset key is triggered, the preset key includes the first virtual key, the second virtual key or the third virtual key, and also includes the first physical key and / or or a second physical key.
[0050] Smart terminals generally have virtual keys and physical keys at the same time. Taking a smartphone installed with the Android system as an example, there are generally virtual keys at the bottom of the display screen, specifically, virtual return keys, virtual home keys, and virtual menu keys, etc.; and physi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com