Protecting method of client procedure and service platform
A client program and service platform technology, which is applied in the protection method and service platform field of client programs, can solve problems such as inconvenient, inability to activate on other devices, invalidation of activation codes, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
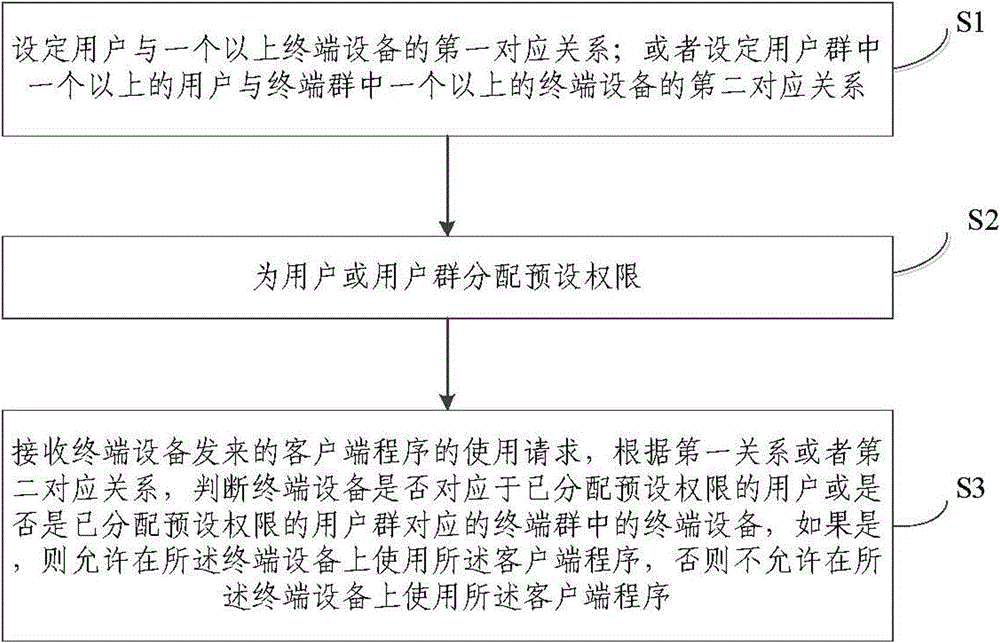
[0038] This embodiment provides a client program protection method, the steps are as follows figure 1 As shown, it specifically includes the following steps:
[0039]Step S1, setting a first corresponding relationship between a user and more than one terminal device; or setting a second corresponding relationship between more than one user in the user group and more than one terminal device in the terminal group.
[0040] Step S2, assigning preset permissions to users or user groups.
[0041] Step S3, receiving the request for using the client program sent by the terminal device, and judging whether the terminal device corresponds to a user who has been assigned a preset authority or whether it is a user group who has been assigned a preset authority according to the first relationship or the second correspondence If yes, the terminal device in the corresponding terminal group is allowed to use the client program on the terminal device, otherwise the client program is not all...
Embodiment 2
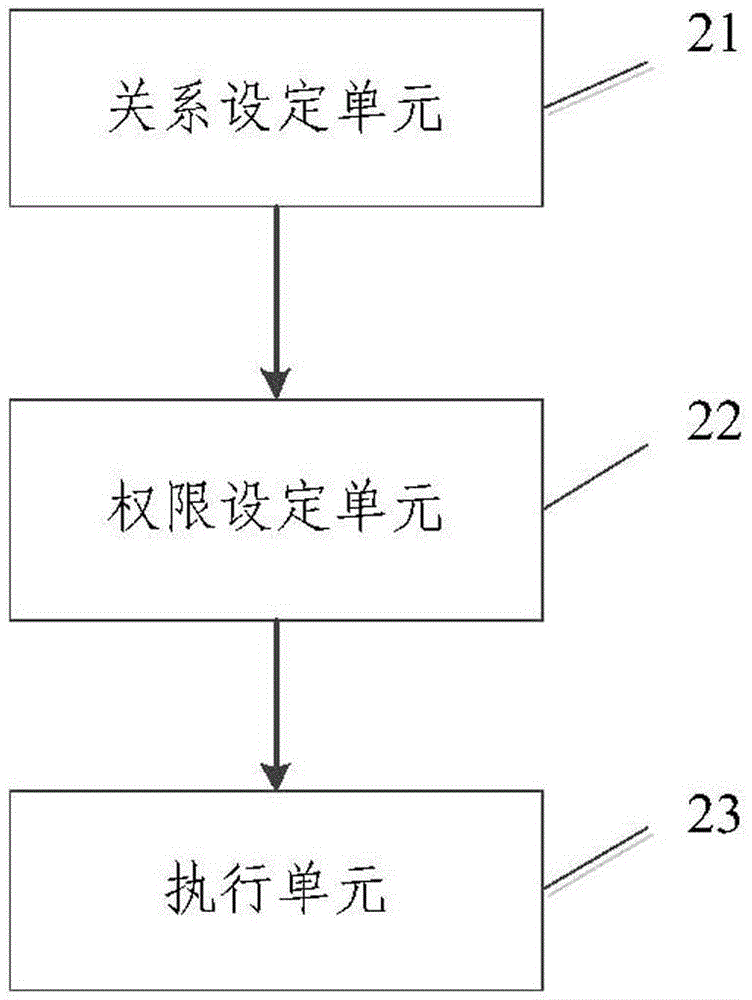
[0068] This embodiment also provides a service platform for protecting client programs, the schematic diagram of which is shown in figure 2 As shown, it includes: a relationship setting unit 21 , an authority setting unit 22 and an execution unit 23 .
[0069] The relationship setting unit 21 is used to set a first corresponding relationship between a user and more than one terminal device; or set a second corresponding relationship between more than one user in the user group and more than one terminal device in the terminal group.
[0070] The authority setting unit 22 is used for assigning preset authority to users or user groups.
[0071] Execution unit 23 is used to receive the use request of the client program sent by the terminal device, and judge whether the terminal device corresponds to a user who has been assigned a preset permission or whether it is a user who has been assigned a preset permission according to the first relationship or the second correspondence re...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com