Method and device for evaluating system security based on correlation analysis
A technology of system security and correlation analysis, applied in the field of network security assessment, can solve problems such as rising network security costs and ignoring network risk sources, and achieve the effect of facilitating network security protection, efficient network security assessment, and improving work efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
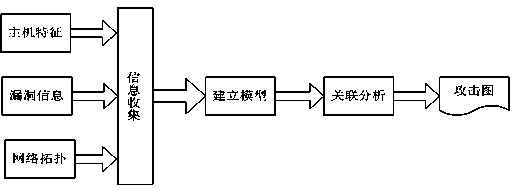
[0030] The system security assessment method based on correlation analysis is characterized in that it is carried out according to the following steps:
[0031] a. OVAL-based vulnerability detection collects network host configuration information and topology information;
[0032] b. Organize and analyze the collected network information, obtain network security elements, which constitute the initial state of the network, and put the initial state into the security state queue;
[0033] c. Collect network vulnerability information, analyze and establish conversion rules through the vulnerability information database, and convert vulnerability information into attack status queues;
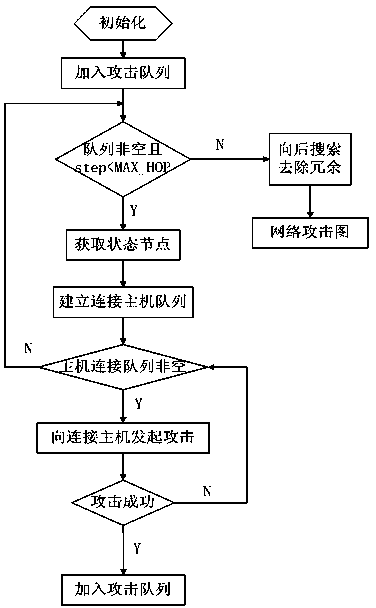
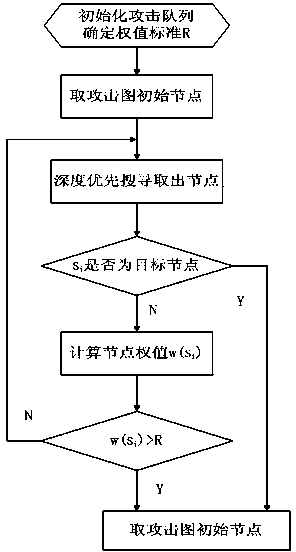
[0034] d. The attack graph generation algorithm through the forward and backward search traverses the attack state node queue, and a complete network attack graph will be generated after the forward search, and the attack sequence and redundant sequence of the unreachable target state nodes in ...
Embodiment 2
[0038] On the basis of Embodiment 1, there are two establishment methods for the conversion rules established by the vulnerability information base in step c:
[0039] (1) Establish vulnerability rules based on prior knowledge by analyzing known attack methods;
[0040] (2) Using the privilege escalation method, analyze the vulnerability privilege escalation ability and establish the rules for exploiting the vulnerability.
Embodiment 3
[0042] On the basis of Embodiment 1, the attack graph generation algorithm of the forward and backward search in the described step d sets the maximum number of hops, and uses the forward search to perform a breadth-first search traversal from the initial state node. If the forward search extends the path If the maximum number of hops is exceeded, the target is considered unreachable and the attack sequence is abandoned; then the backward search algorithm is used to set the set of target state nodes concerned, and the backward search is performed sequentially to exclude the attack of the unreachable target state nodes in the attack graph Sequential and redundant sequences, simplifying the network attack graph as a specified target attack graph.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com