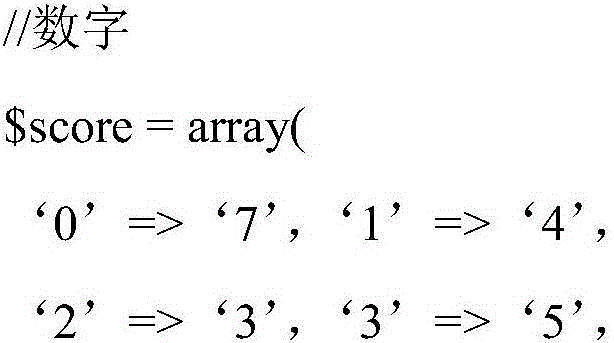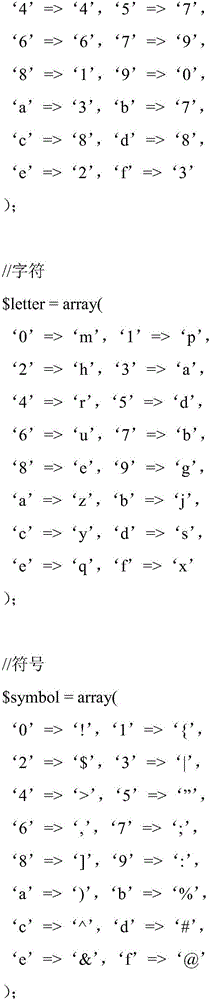A non-storage password management algorithm
A password management and non-storage technology, which is applied in the direction of encryption devices with shift registers/memory, etc., to reduce the risk of password deciphering, reduce the risk, and reduce the risk of leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] The "seasoning" of salt is a random number added when hashing (hash algorithm) the password. The basic idea is this: when a user provides a password for the first time (usually when registering), the system automatically sprinkles some "seasoning" into this password, and then hashes it. When the user logs in, the system sprinkles the same "seasoning" on the code provided by the user, then hashes it, and compares the hashed values to determine whether the password is correct. Because the salt value is randomly generated by the system, even if two users use the same password, their hash values are different, and the chance of hackers finding out the password is greatly reduced (the password and the hash value generated by themselves must be the same The same user, this probability is very low). The technical solution of the present invention will be further described below in conjunction with the accompanying drawings and specific embodiments, but the protected conte...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com