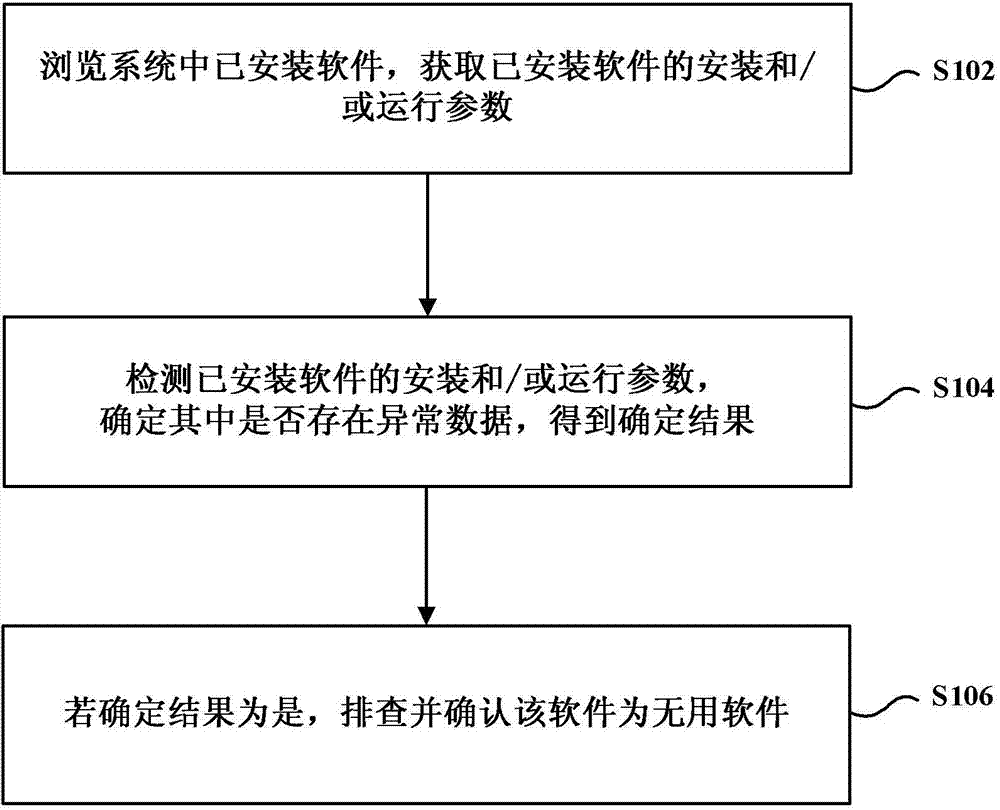
Method and device for investigating useless software
A kind of software, useless technology, applied in the computer field, can solve problems such as not providing troubleshooting useless software
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
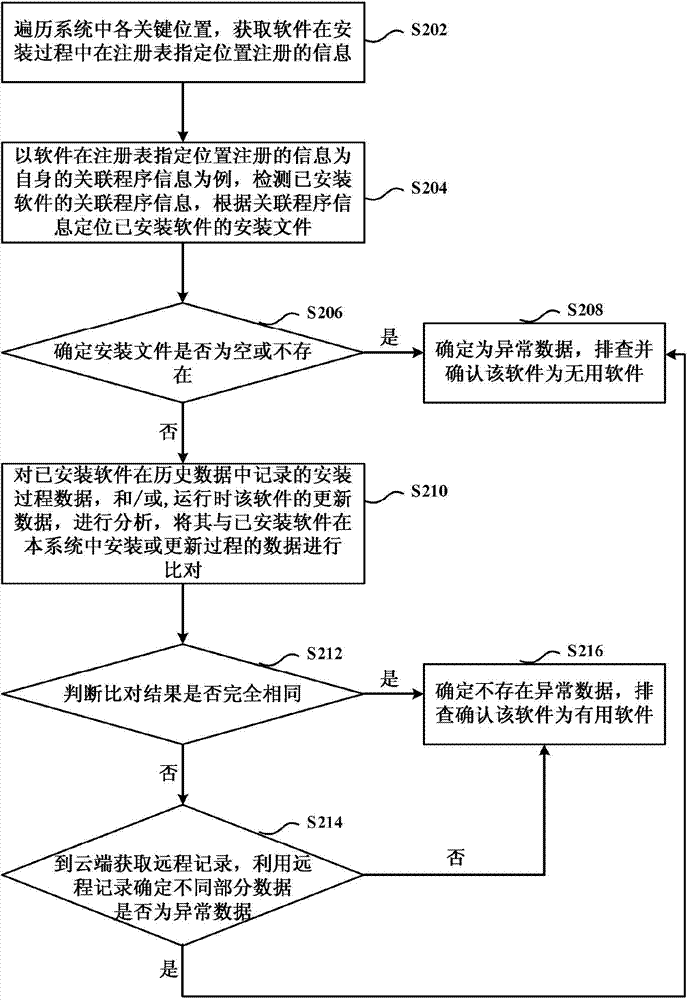
[0097] figure 2 A flowchart showing a method for troubleshooting useless software based on key locations in the system according to an embodiment of the present invention. Such as figure 2 As shown, the method includes the following steps S202 to S216.
[0098] Step S202, traversing each key location in the system, and obtaining information registered at a designated location in the registry during the software installation process.
[0099] The key locations here refer to some registry entries in the registry of the system that record software installation or running information. The information registered by the software at the specified location in the registry may include its own associated program information, application path information, uninstallation item information, and so on. Since the information registered by the software in the specified location of the registry is different, the corresponding methods for determining whether there is abnormal data are also ...
Embodiment 2
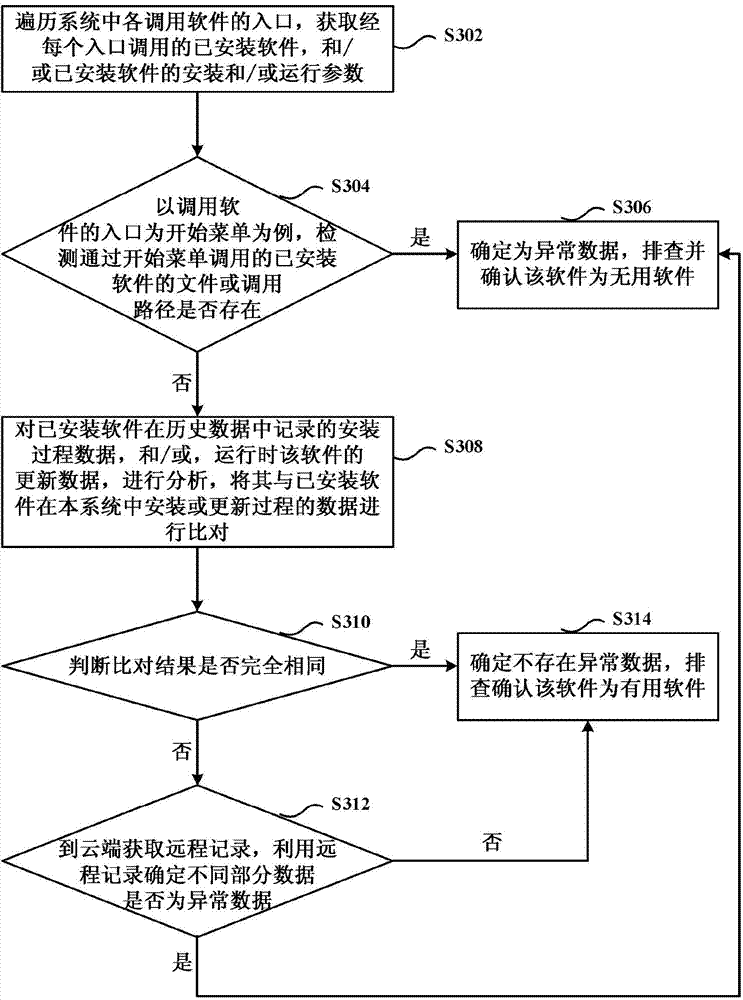
[0110] image 3 A flowchart showing a method for troubleshooting useless software based on an entry of calling software in the system according to an embodiment of the present invention. Such as image 3 As shown, the method includes the following steps S302 to S314.
[0111] Step S302, traversing the entries of each calling software in the system, and obtaining the installed software called by each entry, and / or the installation and / or operating parameters of the installed software.
[0112] Here, the entry for invoking the software may include a start menu, a start item, a desktop shortcut, a right mouse button, and the like. Since the entrances of calling software are different, the corresponding ways of determining whether abnormal data exists therein are also different.
[0113] Step S304, taking the start menu as the entry of calling software as an example, check whether the file or call path of the installed software called through the start menu exists, if yes, cont...
Embodiment 3
[0121] Figure 4 A flow chart showing a method for troubleshooting useless software combined with cloud remote recording according to an embodiment of the present invention. Such as Figure 4 As shown, the method includes the following steps S400 to S414.
[0122] Step S400, record the software installation process record by calling total uninstall, and compare it with the data installed by the software in the system, and / or call process monitor to record the software update process record, and compare it with the software in the system Compare with updated data.
[0123] Step S402, judging whether the comparison results of the two in step S400 are completely the same, if yes, proceed to step S404; otherwise, proceed to step S406.
[0124] Step S404. Determine that there is no abnormal data, check and confirm that the software is useful software, and update the corresponding non-existing information in the registry, maintain the installed software information in the system ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com