An attribute-based anonymous authentication method and system
An anonymous authentication and attribute technology, applied in the field of computer technology and information security, can solve the problems of not being able to obtain other attributes, destroying the user's personal privacy, and third parties not being able to obtain the user's personal information, so as to achieve convenient expansion and improve communication efficiency.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0046] Example 1. Attribute-based anonymous authentication algorithm
specific example
[0048] Assume and is a cyclic group of prime number order with order p (t is used to denote ,illustrate and are two different groups, that is, the present invention needs to set two groups, and use subscript t to distinguish two different prime order cyclic groups), and g is generator of . for arrive bilinear map on .
[0049] A. System setup algorithm
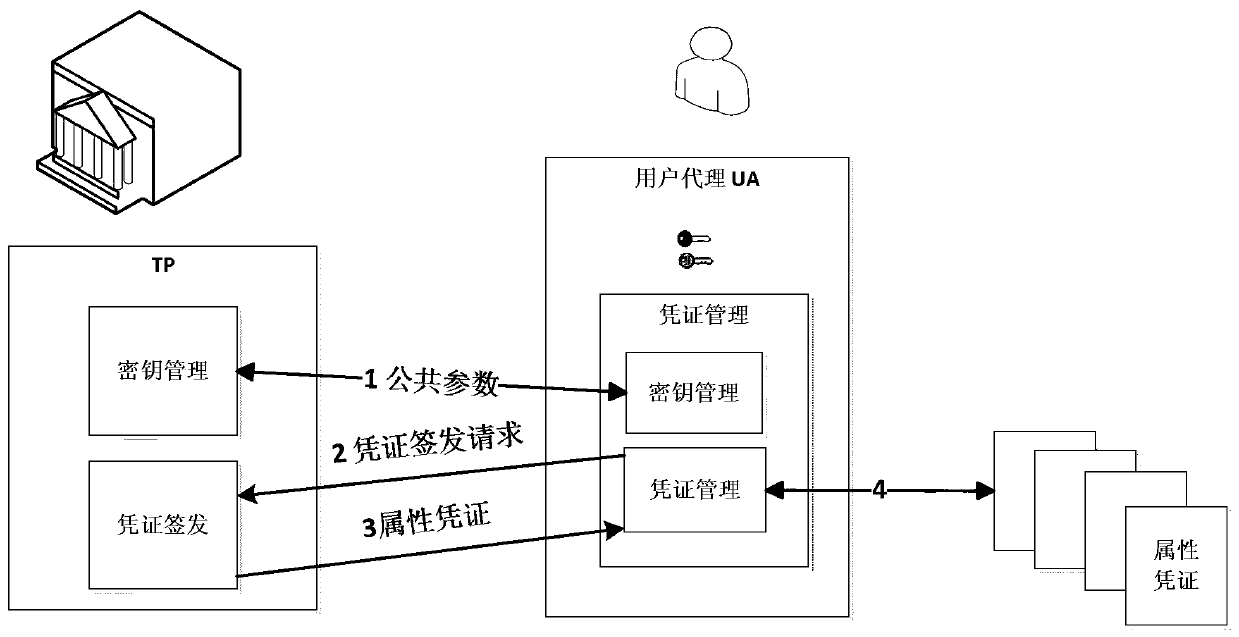
[0050] The algorithm is executed by a trusted party. First, define the maximum number of attributes n that can be included in the credential, and then assign an attribute value ω to each possible user attribute i i (according to the pre-defined allocation method), and additionally select n-1 redundant attributes d j To form a redundant attribute set D, (the distribution of redundant attributes needs to ensure that it will not be repeated with user attributes, if there are less than n user attributes in the credential to be constructed, the trusted party will choose redundant attributes to add to n), These r...
Embodiment 2
[0062] Example 2. Attribute-based anonymous authentication system
[0063] This embodiment aims to provide a specific example of the attribute-based anonymous authentication system of the present invention.
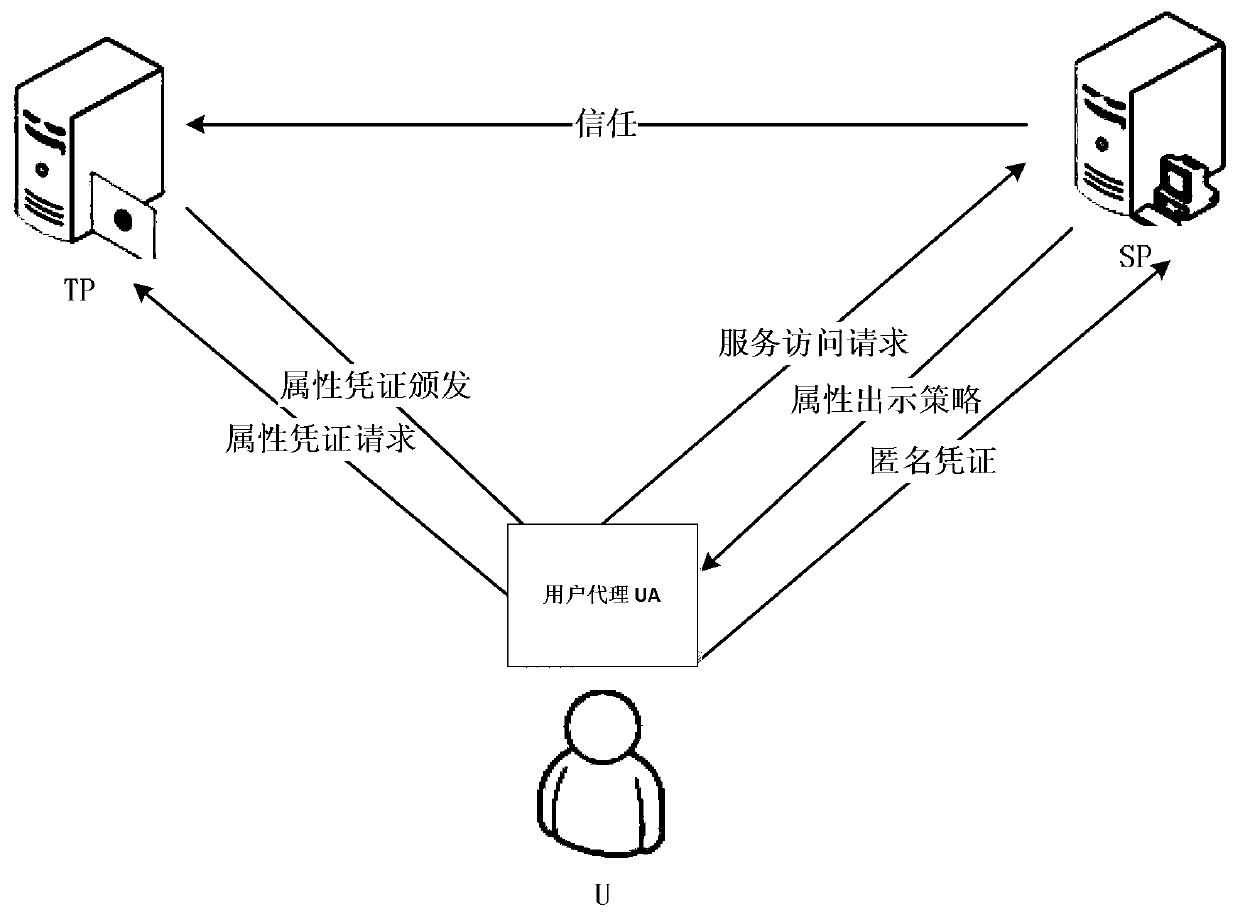
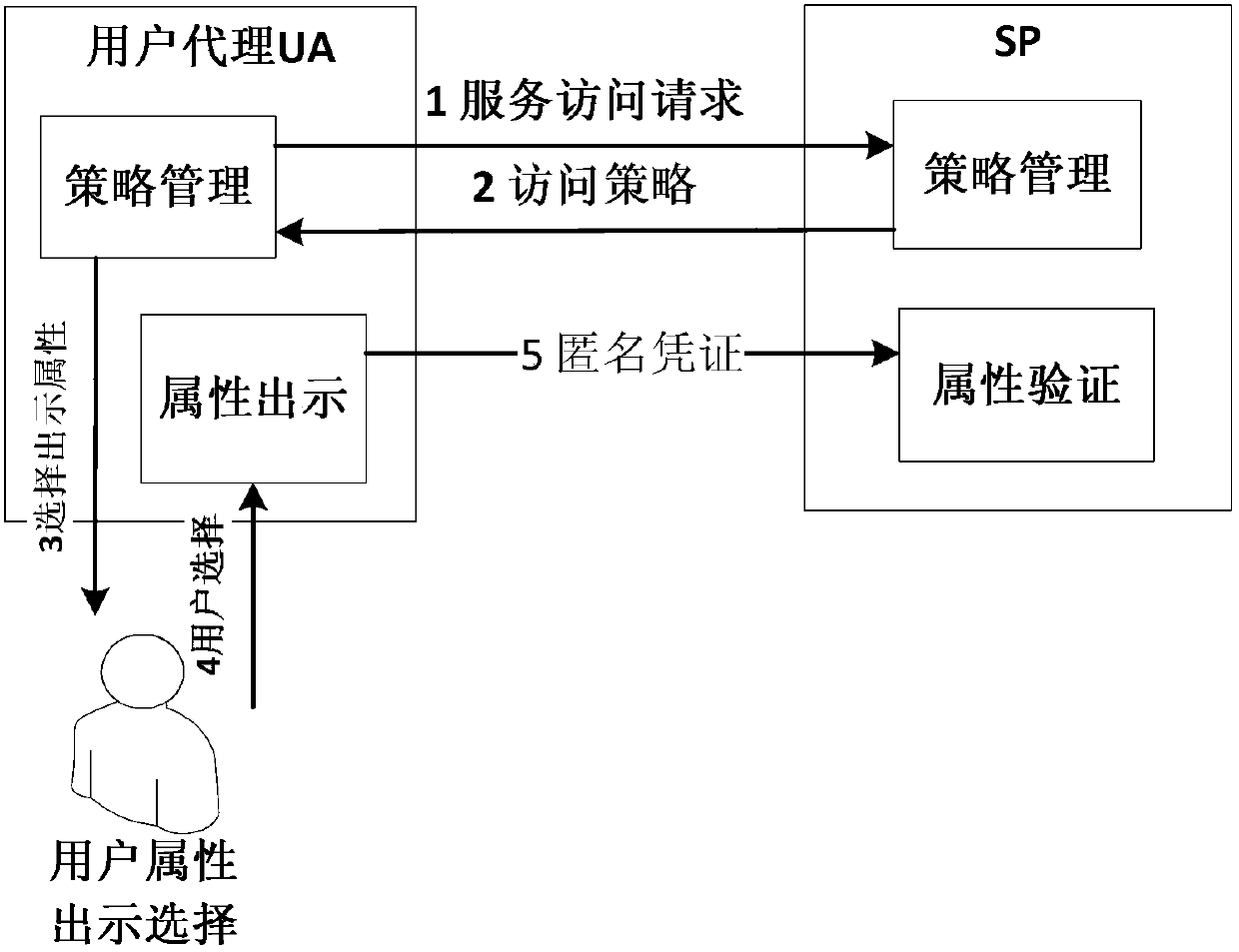
[0064] The system consists of three main bodies: trusted party (Trust Provider, TP), user agent (User Agent, UA), and service provider (Service Provider, SP). The three parts are connected through the network, and the trusted party is responsible for authenticating users and issuing attribute certificates for users. The main work of the user side is completed by the user agent, mainly receiving, storing, querying attribute credentials, and generating verification assertions to assist in the verification of the application service provider. Before requesting services, users need to apply for attribute certificates from trusted parties. When requesting services, they only need to show the attributes that the application service provider needs to be authenticated. For examp...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com