A method and system for protecting private information input by users
A technology for private information and encrypted information, which is applied in the field of information security and can solve problems such as the inability to guarantee the security of private information
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0037] The principles and features of the present invention are described below in conjunction with the accompanying drawings, and the examples given are only used to explain the present invention, and are not intended to limit the scope of the present invention.
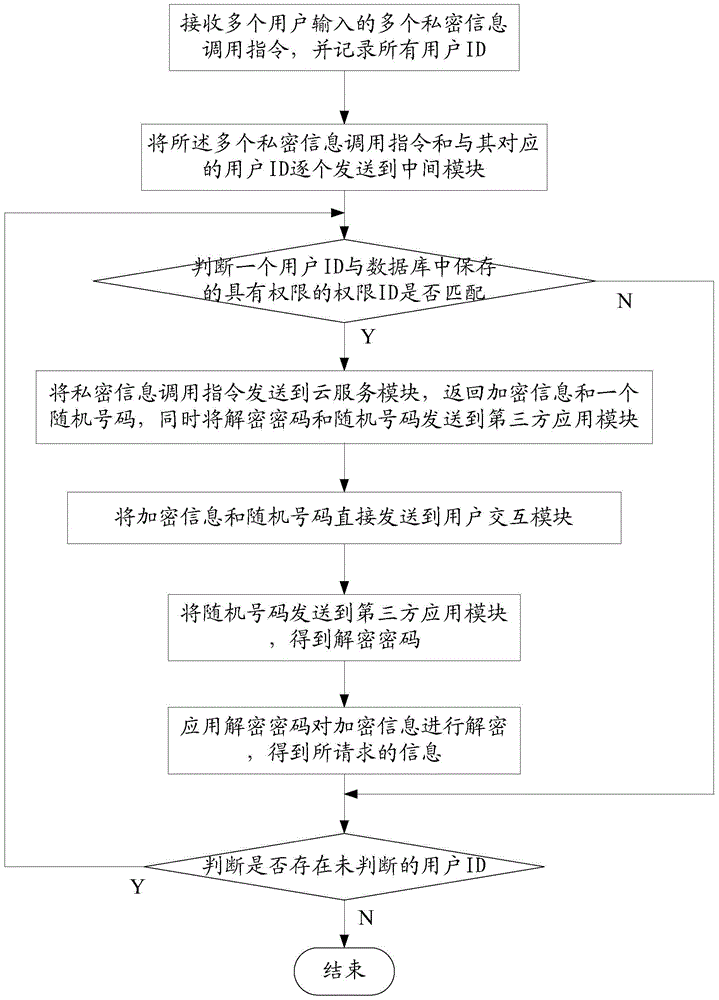
[0038] Such as figure 1 As shown, it is a method for protecting the private information input by the user according to the present invention, which specifically includes the following steps:
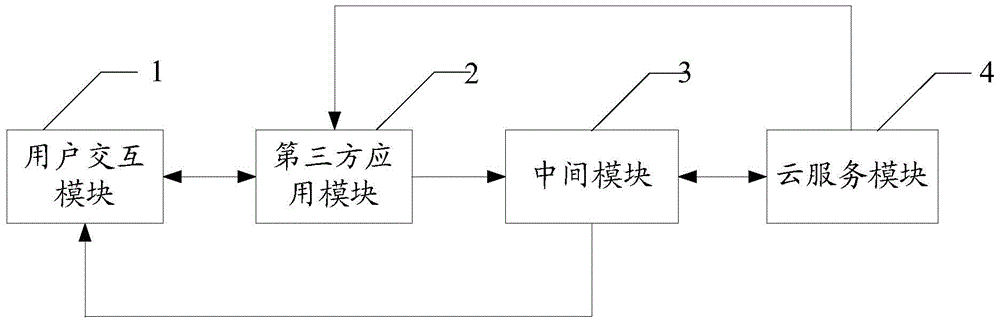
[0039] Step 1: the user interaction module receives multiple private information call instructions input by multiple users, and records all user IDs;
[0040] Step 2: The third-party application module sends the plurality of private information calling instructions and the corresponding user IDs to the intermediate module one by one;
[0041] Step 3: The intermediate module judges whether a user ID matches the authorization ID stored in the database, if yes, execute step 4; otherwise, return a warning message to the user inte...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com