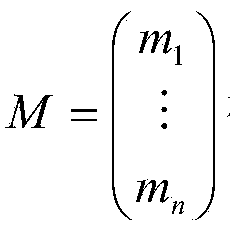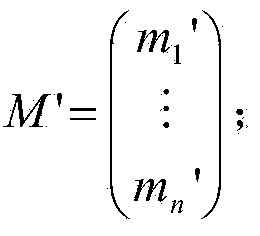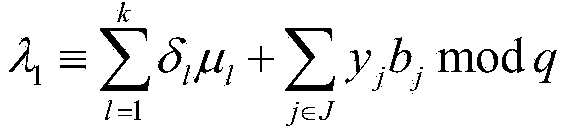Bilinear pairing-free cloud storage data security audit method
A data security, bilinear pairing technology, applied in electrical components, transmission systems, etc., can solve the problems of inability to obtain the original secret information of users and high computational cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] Step of the present invention is divided into 4 parts:
[0032] System initialization: the system divides the data file into blocks to generate a pseudo-random number generator and a pseudo-random function. The system then selects a lightweight symmetric cryptographic algorithm and a secure hash function.
[0033]Signature steps: the user first calls the pseudo-random number generator and the pseudo-random function to generate the matching coefficient used to generate the homomorphic message authentication code of the data block, uses the Schnorr variant signature algorithm to sign it, and then calls a lightweight symmetric cryptographic algorithm to Each data block is cryptographically blinded. Finally, the signature set of the homomorphic message authentication code and the blinded data file are sent to the cloud server, and the signature set and the original data file are deleted on the client side.
[0034] Audit proof generation steps: When the user sends audit r...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com