Method and device for system penetration testing
A penetration testing and system technology, applied in the field of system penetration testing, can solve the problems of network paralysis, harmful network security, unhelpful computer technology development, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] The present invention can be further understood through the specific examples of the present invention given below, but they are not intended to limit the present invention. Some non-essential improvements and adjustments made by those skilled in the art based on the above content of the invention are also deemed to fall within the protection scope of the present invention.
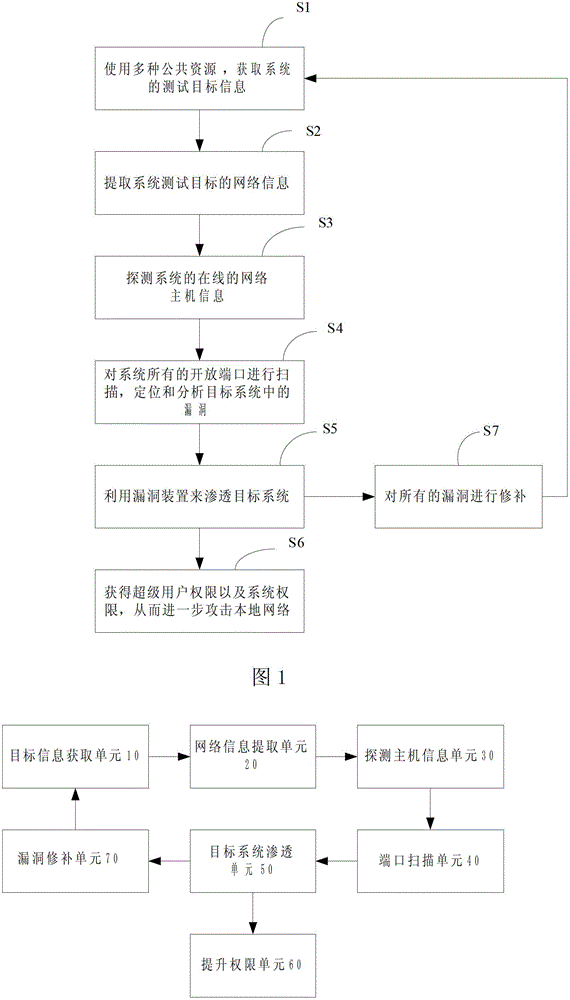
[0029] Please refer to Fig. 1, embodiment of the present invention, a kind of method for system penetration test, comprises:
[0030] S1. Use a variety of public resources to obtain system test target information;
[0031] After delineating the scope of the test, an information reconnaissance phase is required. At this stage, penetration testers need to use various public resources to obtain more information about the test target, which can be gleaned from the Internet, such as forums, blogs, social networks, and other commercial or non-commercial websites.
[0032] In addition, relevant data can...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com