Generating method for secret keys with user information
A user information and key technology, which is applied in key distribution, can solve the problems of copyright protection difficulties, digital product anti-counterfeiting and traceability, and difficulty, and achieve the effects of improving copyright protection efficiency, inhibiting use and dissemination, and preventing use and dissemination
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
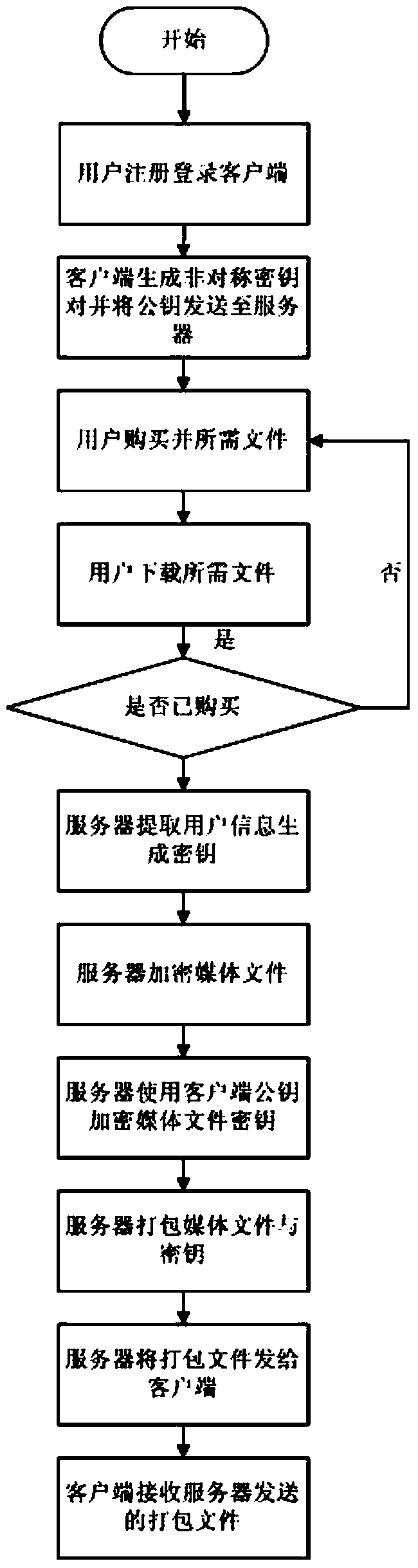
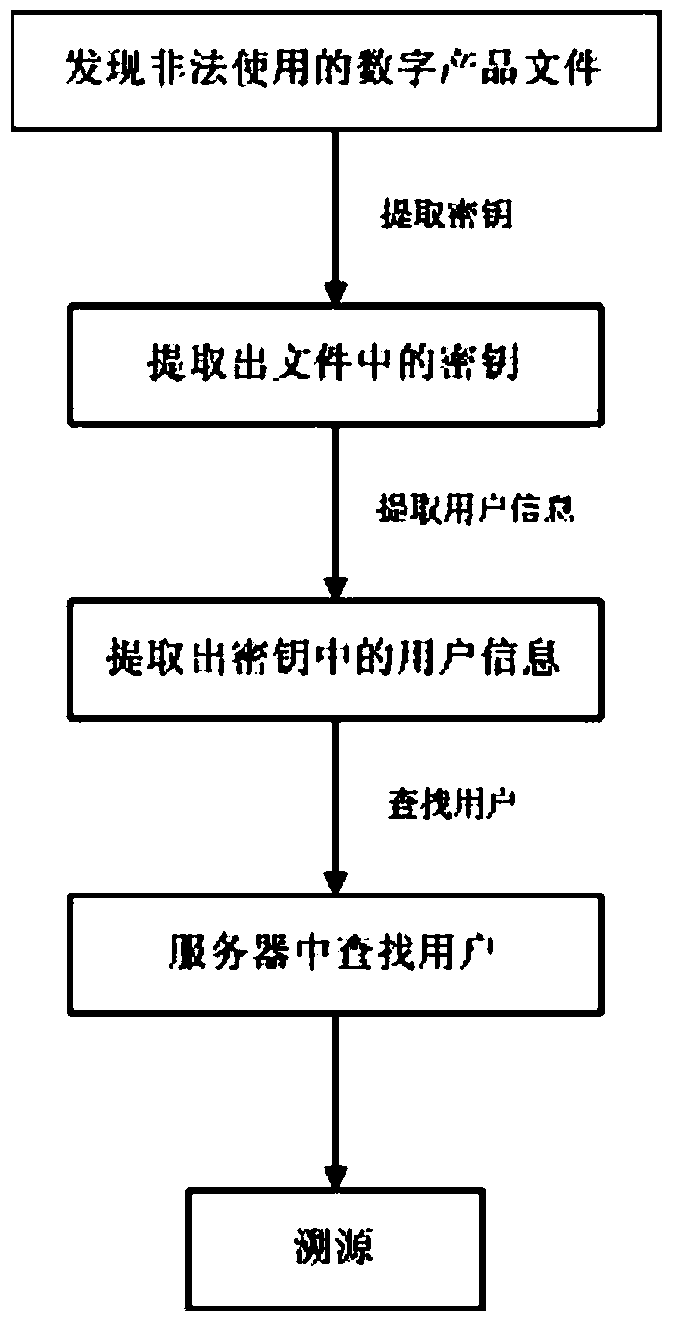
[0097] Taking the copyright management of electronic audio and video products as an example, the user registers on the server of the media file provider of the audio and video products, and logs in with the registered account. key is sent to the server. The user browses the media files on the server, pays for the required media files, and the purchased media files can be downloaded and used by the user. The user clicks the media files to download, and the media server extracts the media file ID, user ID and other information to use the media files. The ID is the seed, a random key is generated, and the MD5 information digest is calculated on it to obtain a 128-bit ciphertext, then the user information is extracted, MD5 is also calculated, and a 128-bit ciphertext is also obtained, and the two are packaged. A 256-bit ciphertext is obtained, which is the encryption key of the generated user media file, and the RC4 algorithm is used to symmetrically encrypt the media file.
[00...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com