Information push method and device
A technology of information push and event information, which is applied in the field of computer networks, can solve the problems of user information harassment and low accuracy of information push, and achieve the effect of avoiding information harassment and improving accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
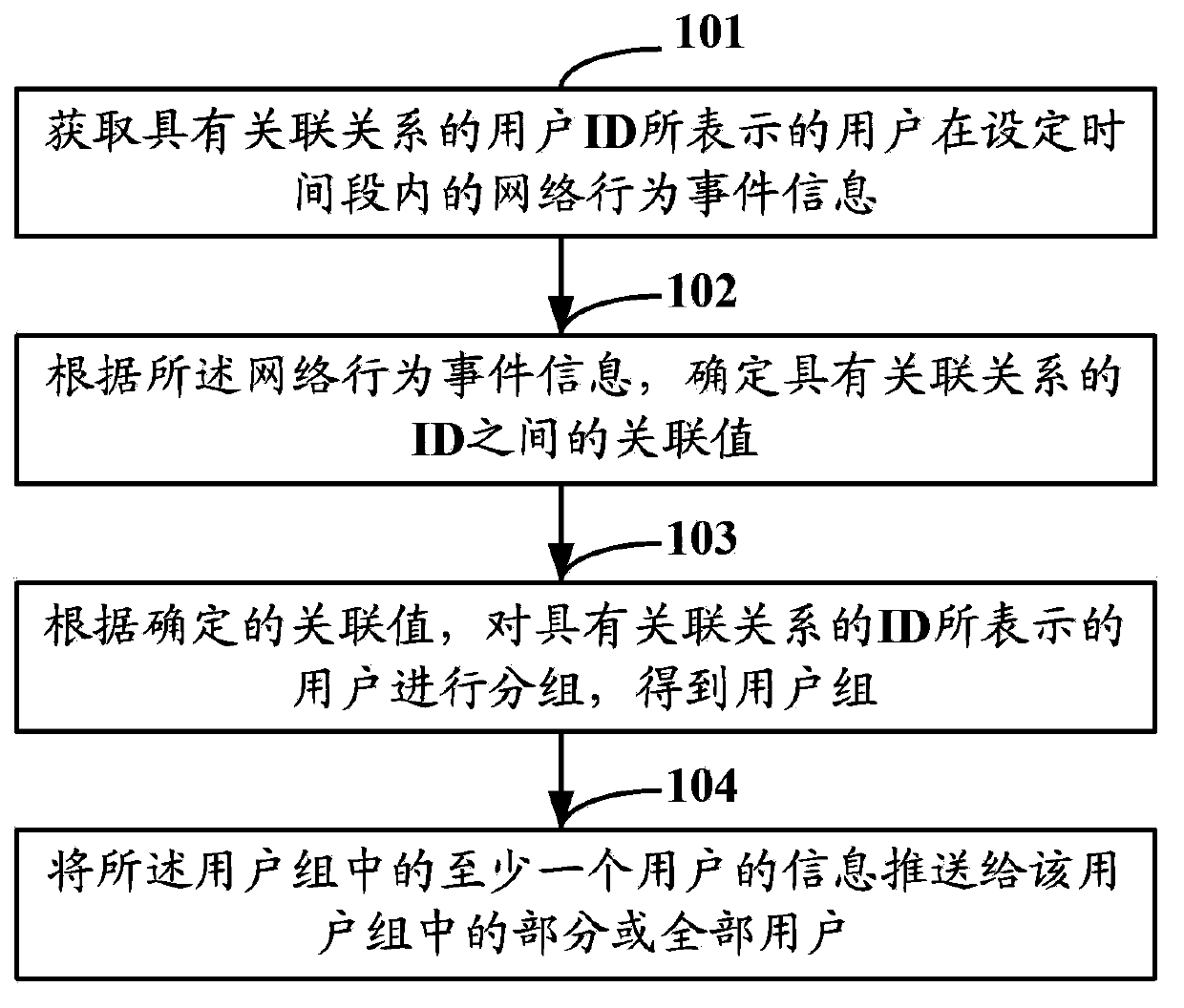
[0030] like figure 1 As shown, it is a schematic diagram of the information push method in Embodiment 1 of the present application, and the method includes the following steps:
[0031] Step 101: Obtain the network behavior event information of the user represented by the associated user ID within a set period of time.
[0032] The user with an associated relationship refers to a certain user attribute or users with the same user attributes, or a certain user attribute or multiple user attributes complementary users, for example: assume that user A and user B have the same user attribute , then user A and user B can be called users with an associated relationship.
[0033] The set time period may be determined according to actual needs.
[0034] Step 102: According to the network behavior event information, determine an association value between IDs having an association relationship.
[0035] The association value may be a similarity value between two users, or a similarit...
Embodiment 2
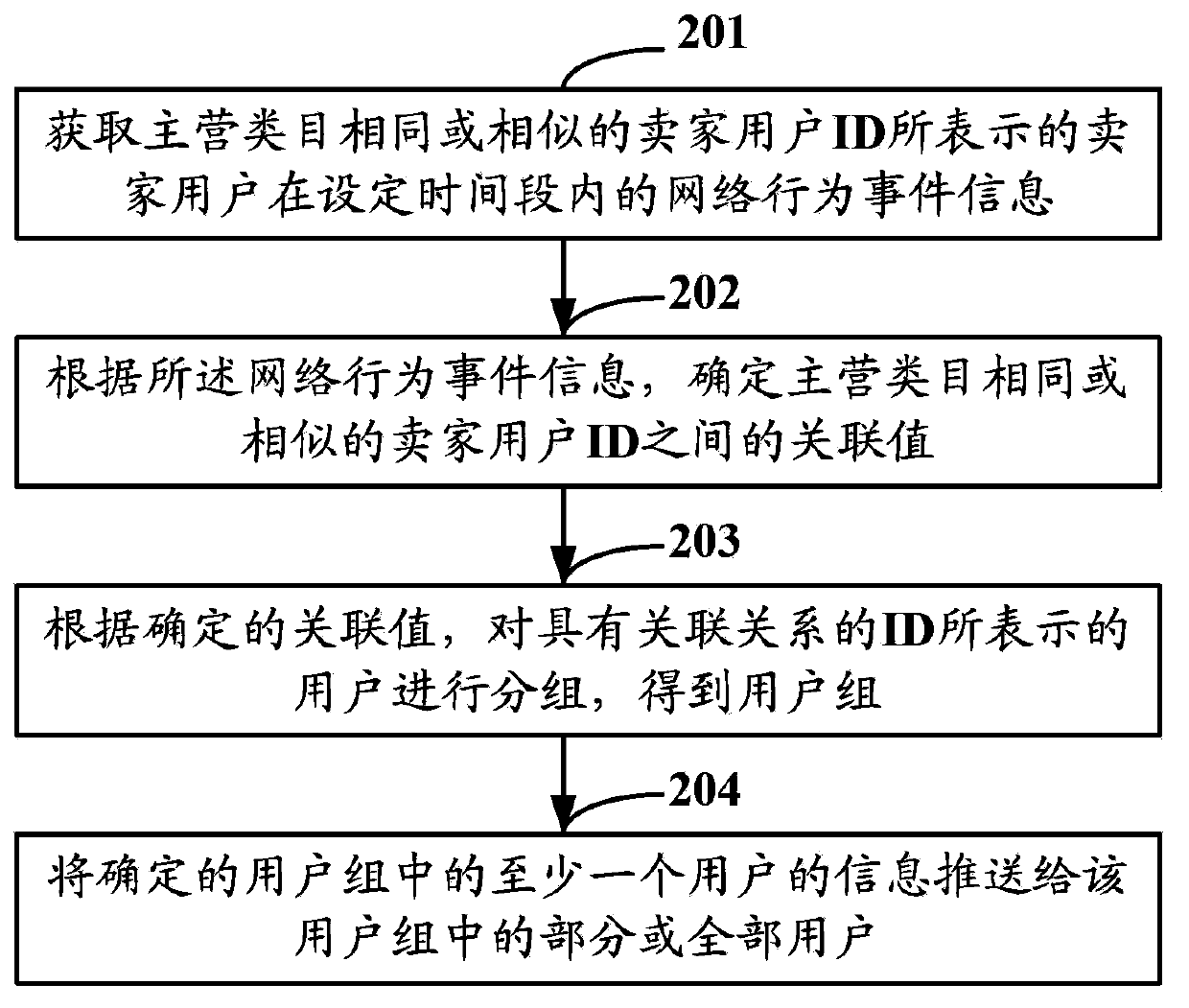
[0043]In the second embodiment of this application, the user is a seller user, and the associated ID can be a seller user ID with the same or similar main business category, or a seller user ID with a complementary main business category. Behavior event information is seller network behavior event information. In the following, when the associated IDs are the seller user IDs with the same or similar main business categories, the network behavior event information is the seller’s network behavior event information, and the related IDs are the seller users whose main business categories are complementary ID, when the network behavior event information is the seller’s network behavior event information, the method of information push is described.
[0044] like figure 2 As shown, it is a schematic diagram of the information push method in Embodiment 2 of the present application, in figure 2 In the method shown, the IDs with the associated relationship are the user IDs of sell...
Embodiment 3
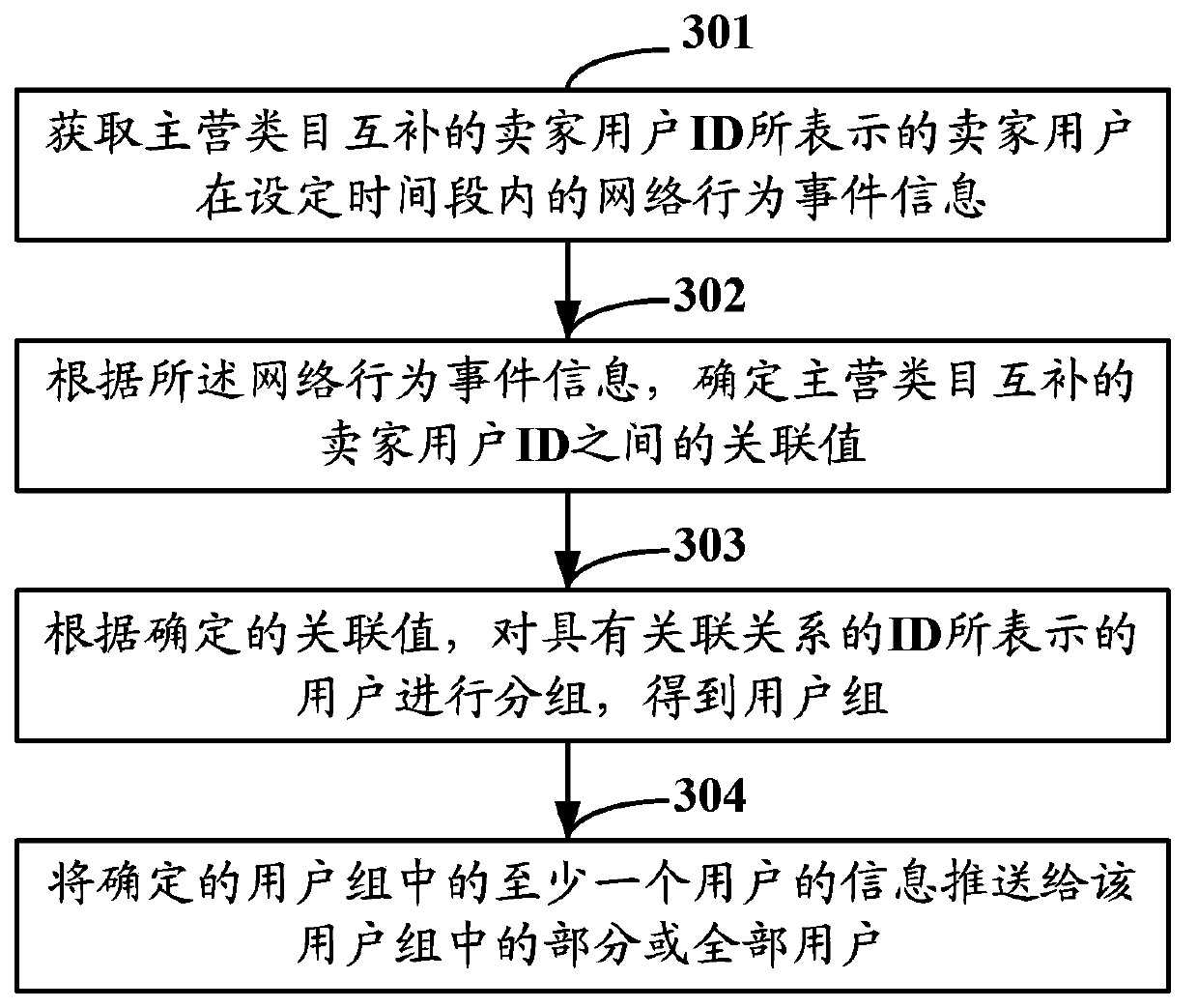
[0122] In the third embodiment of the present application, the user is a buyer user, and the associated ID can be a seller user ID with the same or similar main shopping category, or a buyer user ID with a complementary main shopping category, so The above-mentioned network behavior event information is buyer network behavior event information.
[0123] In the following, when the associated IDs are the same or similar to the buyer’s user ID of the main buyer category, when the network behavior event information is the buyer’s network behavior event information, and the associated IDs are complementary to the main buyer category The buyer user ID, and the method for pushing information when the network behavior event information is buyer network behavior event information will be described.
[0124] like Figure 4 As shown, it is a schematic diagram of the information push method in Embodiment 3 of the present application, in Figure 4 In the method shown, the IDs that have a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com