Implementation method of safety time of client
A realization method and security time technology, applied in the direction of electrical components, transmission system, program/content distribution protection, etc., can solve the problem of loss of control over the use of copyright objects, and achieve fine copyright control, good user experience, and guaranteed benefits.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
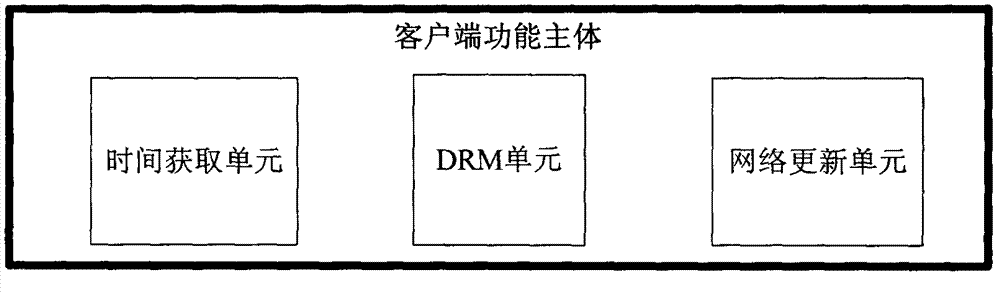
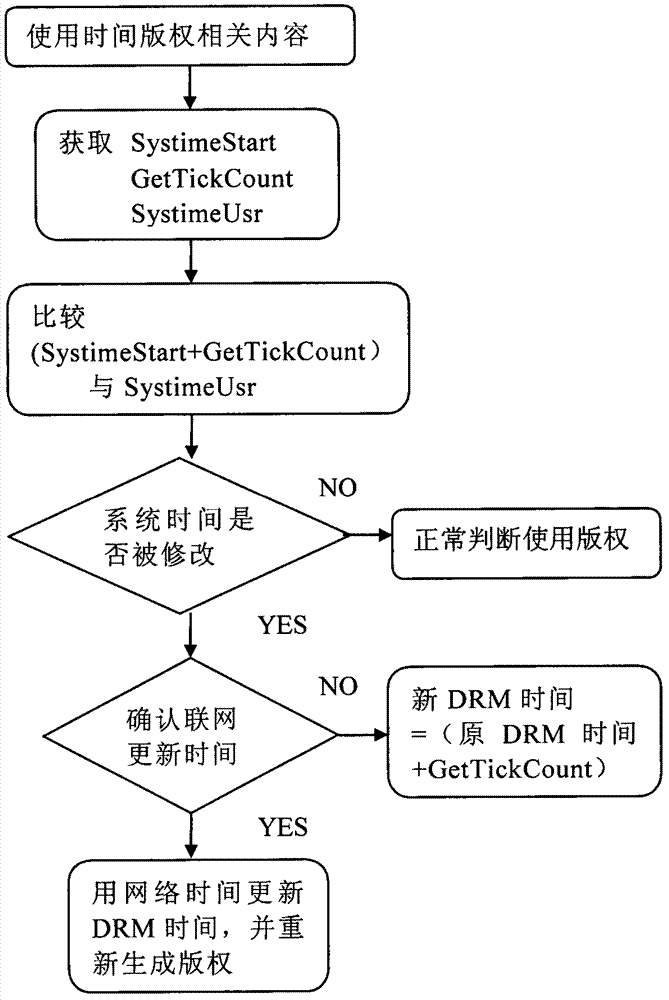
[0021] The invention discloses a method for realizing client security time, such as figure 1 Shown: this method is mainly realized at client end, and this client end comprises time acquisition unit, DRM unit and network update unit; Its specific steps (such as figure 2 )yes:
[0022] Step A: When the user turns on the client device, the time acquisition unit acquires the system startup time SystimeStart. After a period of time, when using the client to open the time copyright product, the time acquisition unit acquires the system running time length GetTickCount. At the same time, the time acquisition unit acquires the current system time timeSystimeUsr;
[0023] Step B: If SystimeUsr=SystimeStart+GetTickCount, it means that the system time is correct, and execute step D; if SystimeUsr≠SystimeStart+GetTickCount, it is considered that the user has modified the system time, and execute C;
[0024] Step C: The client network update unit judges whether the client is connected t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com