Intra-cell handover method and intra-cell handover equipment
An intra-cell handover and cell technology, applied in the field of intra-cell handover methods and devices, can solve problems such as unspecified specific procedures, and achieve the effects of avoiding re-establishment and updating of security parameters and business interruption.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
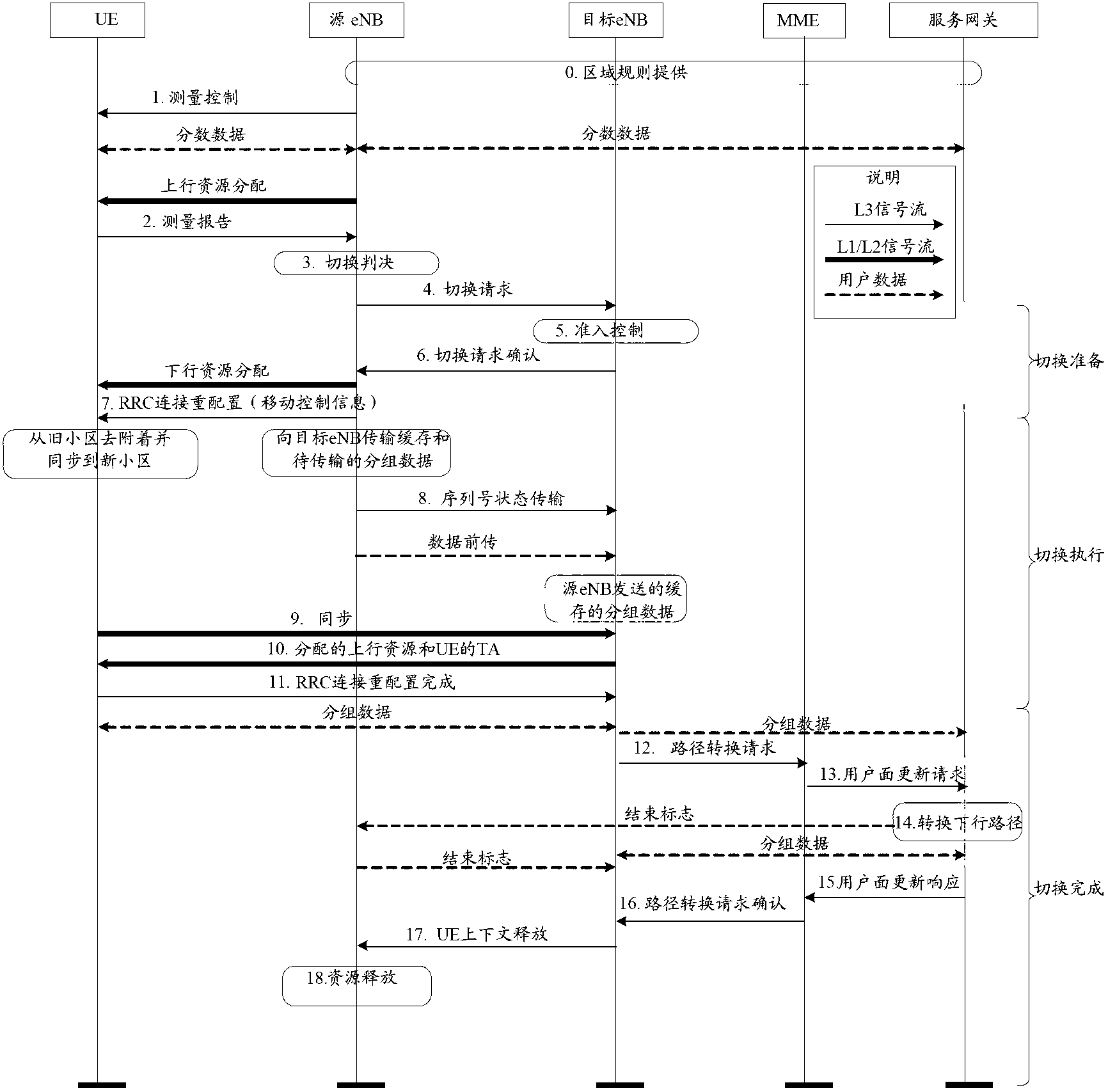
[0079] The specific process is as Figure 5a Shown:
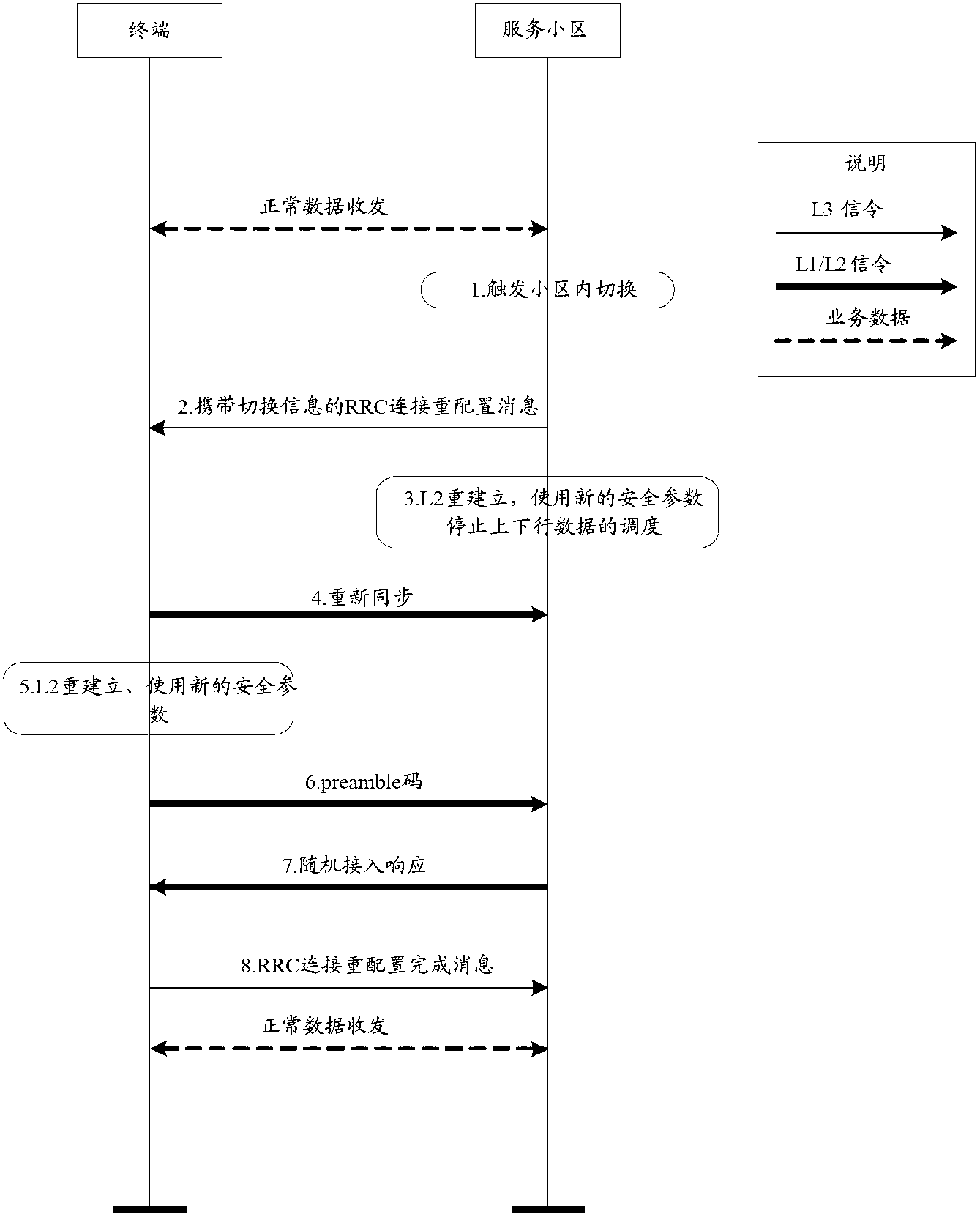
[0080] Step S01: After the terminal transmits and receives data reaches a certain amount or repeatedly establishes and deletes a bearer for a certain number of times, the base station of the serving cell initiates an intra-cell handover.
[0081] Step S02: The base station of the serving cell sends an RRC connection reconfiguration message carrying a handover command to the terminal. The target cell carried in the handover parameters is the current cell, that is, the cell where the terminal is located before the handover, and carries updated security parameters, including Encryption and decryption keys and integrity protection keys. In particular, the new C-RNTI assigned to the terminal is also carried in the handover parameters but does not carry a dedicated preamble code, as shown in Table 1 below, the new C-RNTI is different from the C-RNTI used by the terminal before the handover.
[0082]
[0083]
[0084] Tabl...
Embodiment 2
[0101] The specific process is as Figure 5b Shown:
[0102] Step S11: After the terminal sends and receives a certain amount of data or repeatedly establishes and deletes a bearer for a certain number of times, the base station of the serving cell initiates an intra-cell handover.
[0103] Step S12: The base station of the serving cell sends an RRC connection reconfiguration message carrying a handover command to the UE. The target cell carried in the handover parameters is the current cell, that is, the cell where the UE is located before the handover, and carries updated security parameters, including Encryption and decryption keys and integrity protection keys. In particular, the handover parameter also carries a dedicated preamble code but does not carry a new C-RNTI allocated for the UE.
[0104] Step S13: The behavior of each L2 protocol layer of the base station of the serving cell is as follows:
[0105] The PDCP layer stops sending downlink data (including signali...
Embodiment 3
[0118] The specific process is as Figure 5c Shown:
[0119] Step S21: After the terminal sends and receives a certain amount of data or repeatedly establishes and deletes a bearer for a certain number of times, the base station of the serving cell initiates an intra-cell handover.
[0120] Step S22: The base station of the serving cell sends an RRC connection reconfiguration message carrying a handover command to the UE. The target cell carried in the handover parameters is the current cell, that is, the cell where the UE is located before the handover, and carries updated security parameters, including Encryption and decryption keys and integrity protection keys. In particular, the handover parameters also carry a dedicated preamble code and a new C-RNTI allocated for the UE.
[0121] Step S23: The behavior of each L2 protocol layer of the base station of the serving cell is as follows:
[0122] The PDCP layer stops sending downlink data (including signaling data and serv...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com