Protection system for network access behavior
A network access and protection system technology, applied in transmission systems, electrical components, etc., can solve problems such as the inability to determine the purpose of network access requests, the inability to timely and effectively intercept malicious program network access behaviors, etc., and achieve the effect of timely interception
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] Exemplary embodiments of the present disclosure will be described in more detail below with reference to the accompanying drawings. Although exemplary embodiments of the present disclosure are shown in the drawings, it should be understood that the present disclosure may be embodied in various forms and should not be limited by the embodiments set forth herein. Rather, these embodiments are provided for more thorough understanding of the present disclosure and to fully convey the scope of the present disclosure to those skilled in the art.
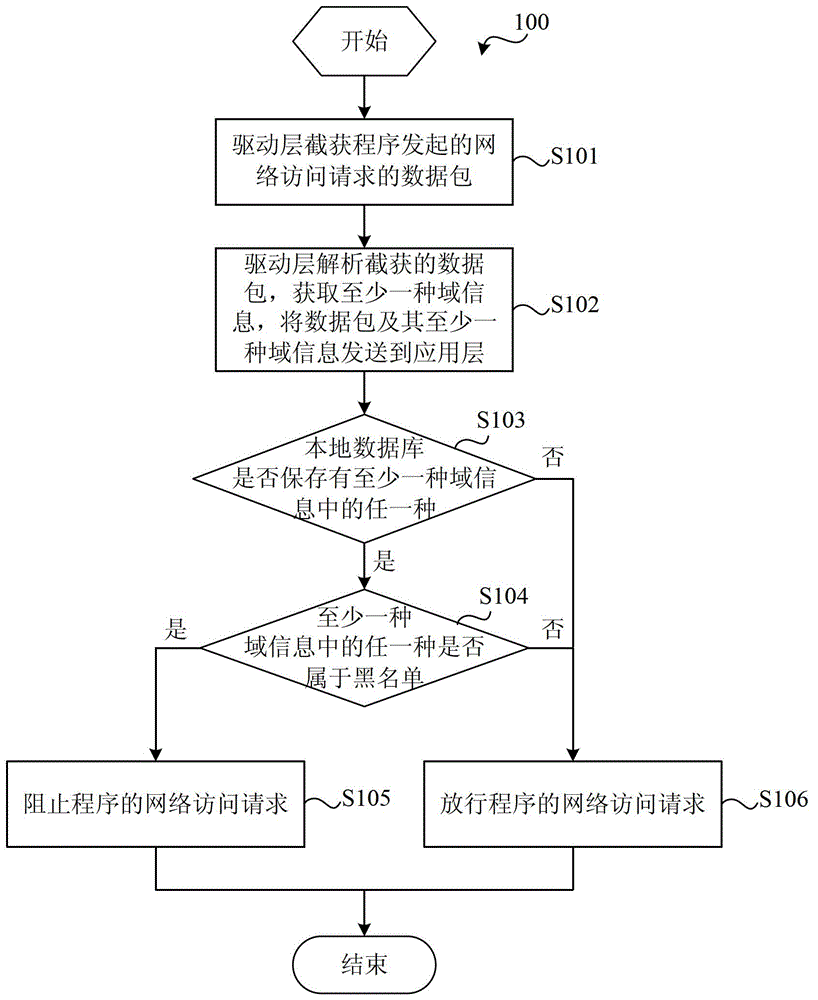
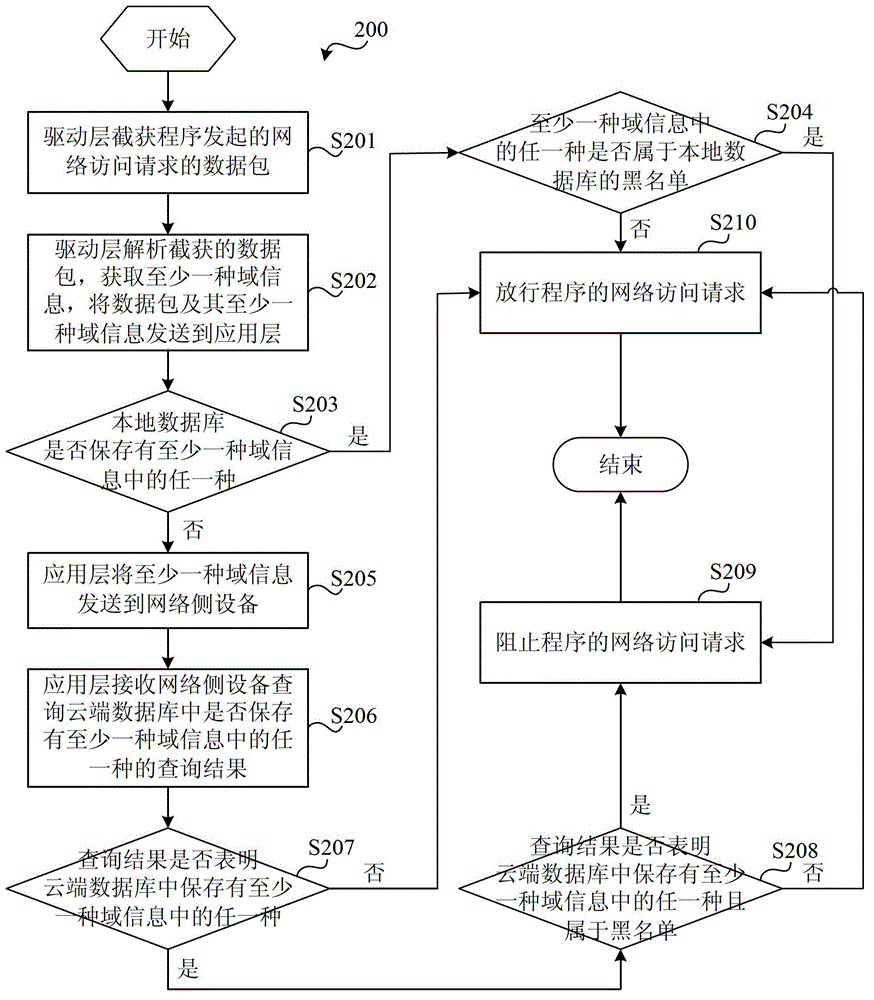
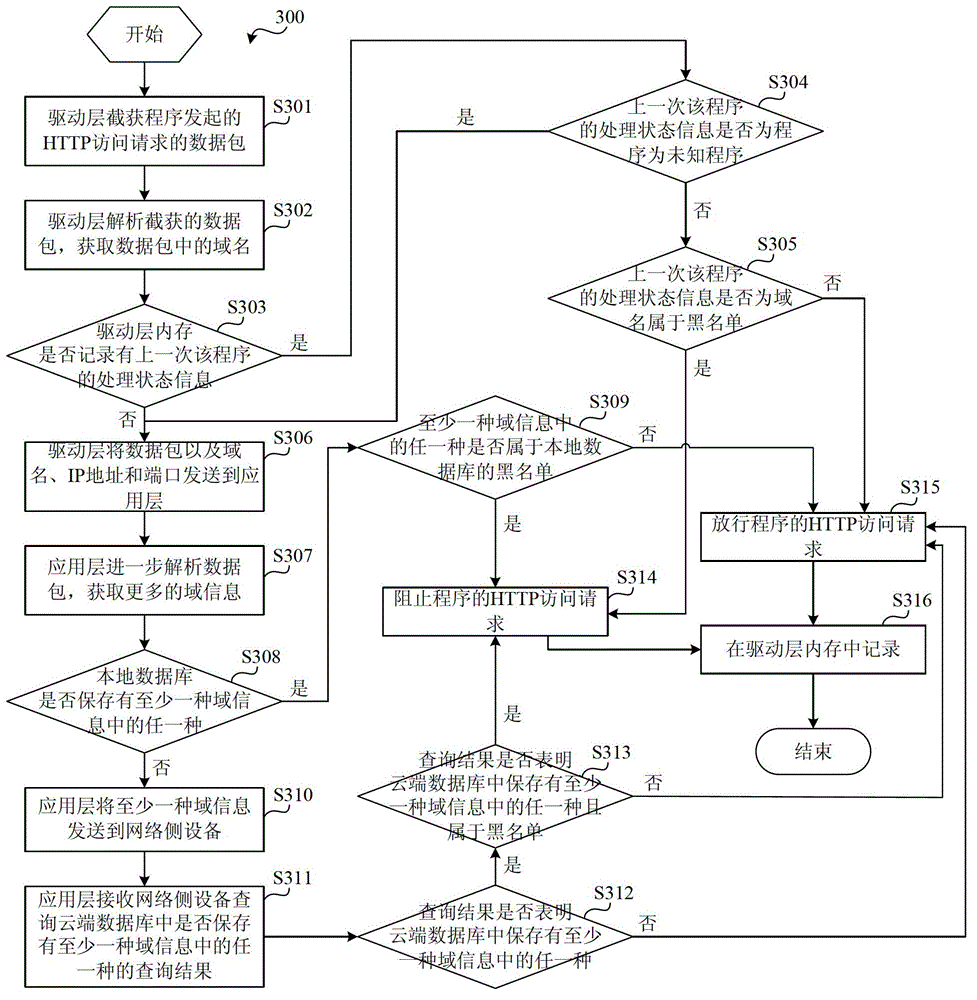
[0021] A program is an ordinary file, a collection of machine code instructions and data, and a static concept. A process is an execution process of a program on a computer and is a dynamic concept. The same program can run on several data sets at the same time, that is to say, the same program can correspond to multiple processes. Network access behaviors are initiated by running programs (that is, processes). The current networ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com