Pre-authentification computer system login method based on high collision probability hash function
A computer system, collision probability technology, applied in transmission systems, user identity/authority verification, electrical components, etc., can solve the problem of password verification algorithm consuming system computing resources, and achieve the effect of reducing wrong input
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
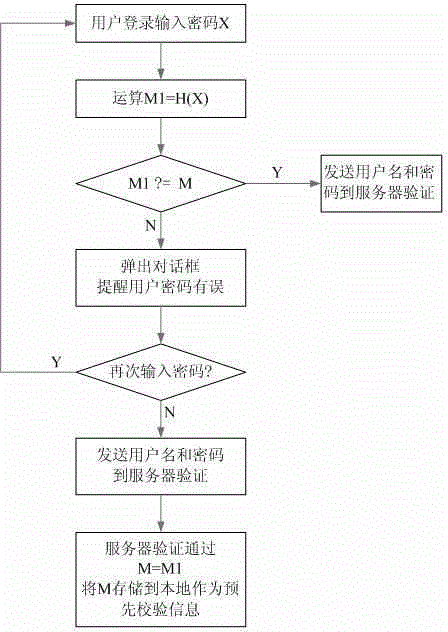
[0054] Such as figure 1 As shown in the overall flow chart of the present invention, a computer system login method based on high collision probability hash function pre-authentication includes the following steps:
[0055] S1 user login input password X;
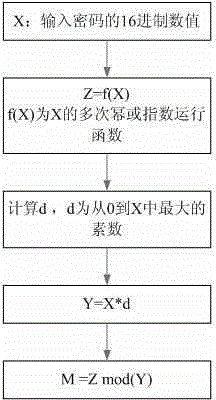
[0056] The S2 password obtains a value M1 through the set high collision probability hash function H(X);
[0057] S3 compares M1 with the locally stored pre-checked information M, and if they are the same, send the user name and password to the server for verification;
[0058] S4 If M1 is different from the locally stored pre-verification information M, a dialog box will pop up to remind the user that the password is wrong;
[0059] S5 The user clicks the dialog box option to determine whether to enter the password again or send it directly to the server for verification;
[0060] S6 If the user chooses to input the password again, repeat the steps of S1-S4 above;
[0061] S7 If the user chooses not to enter the passwo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com