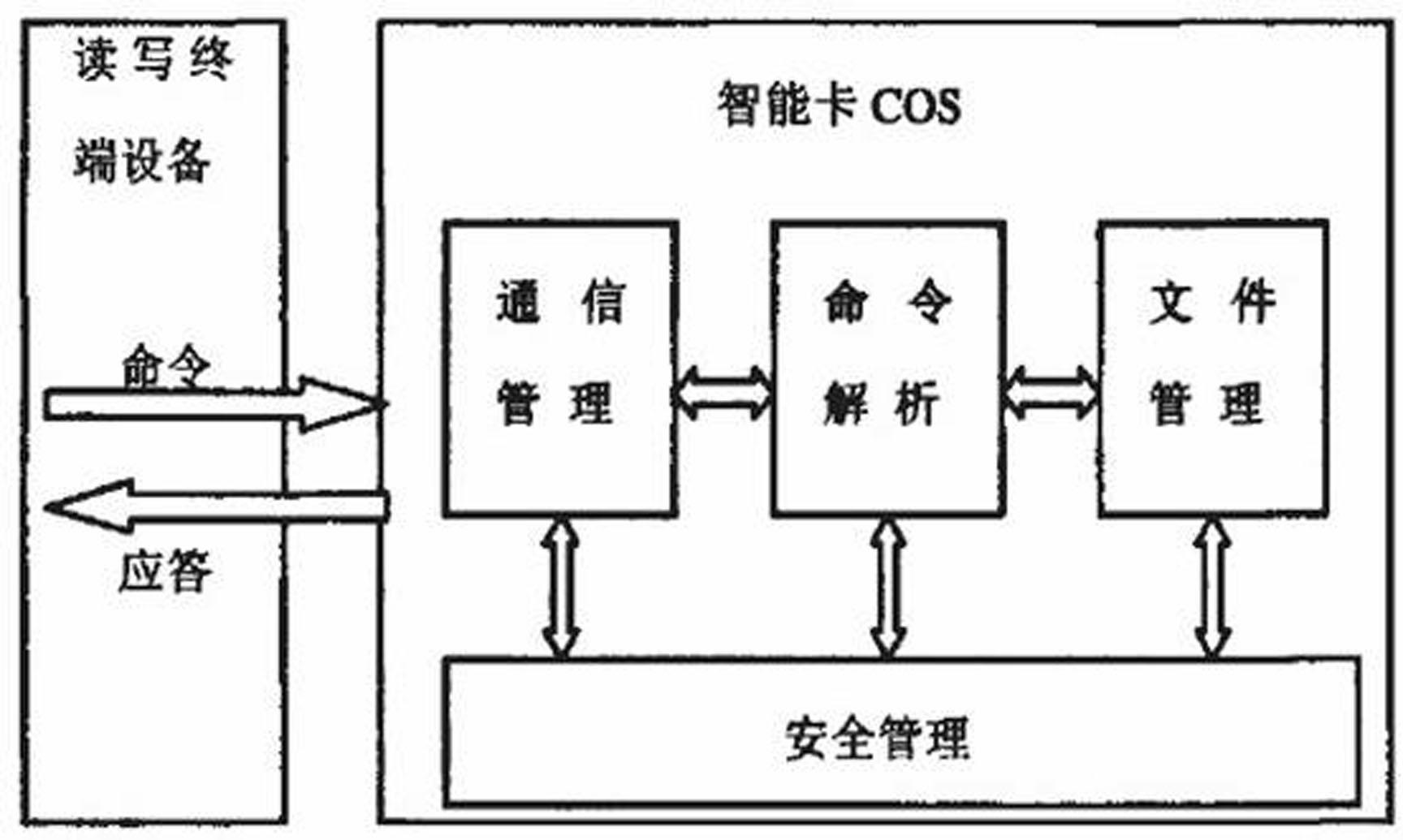
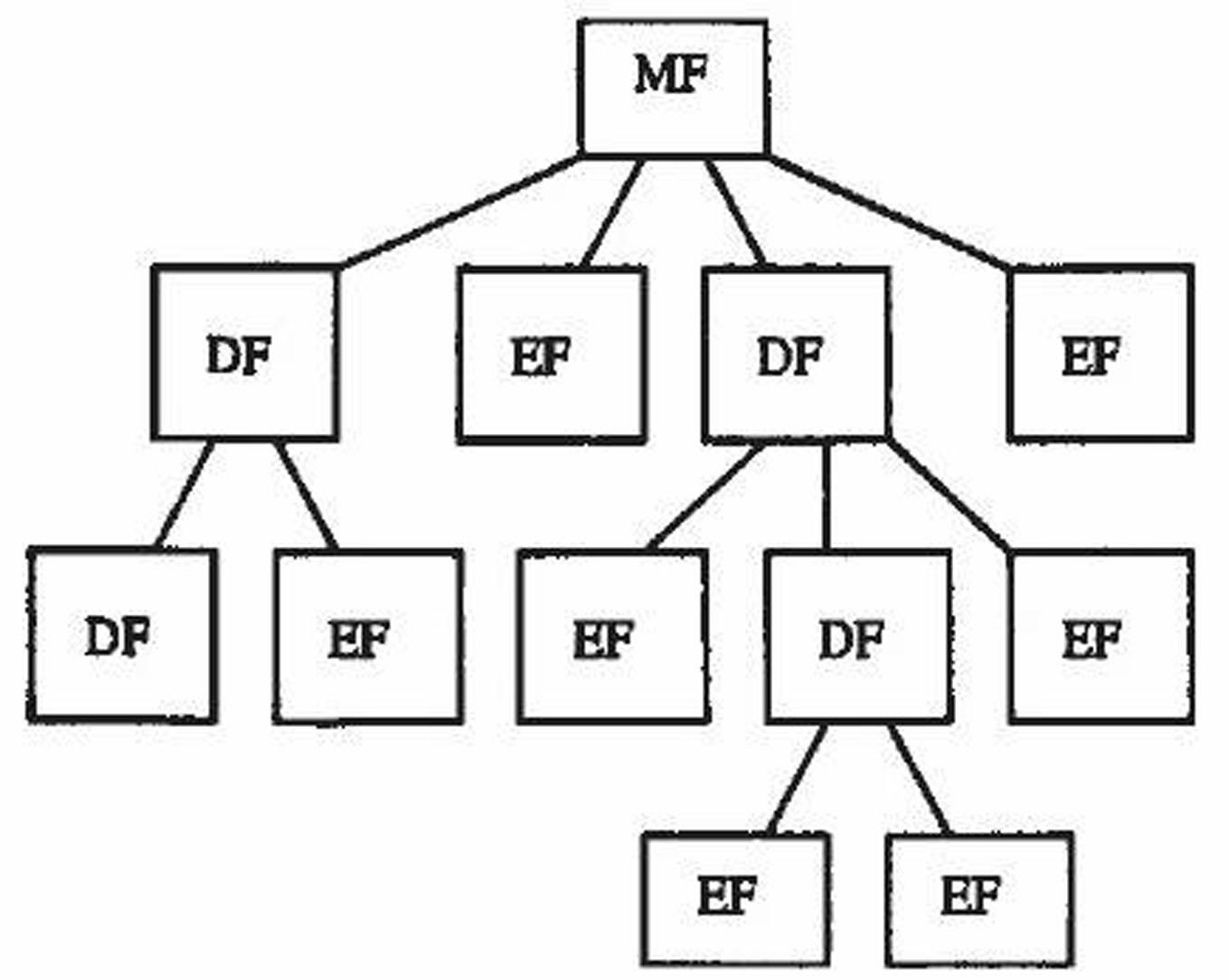
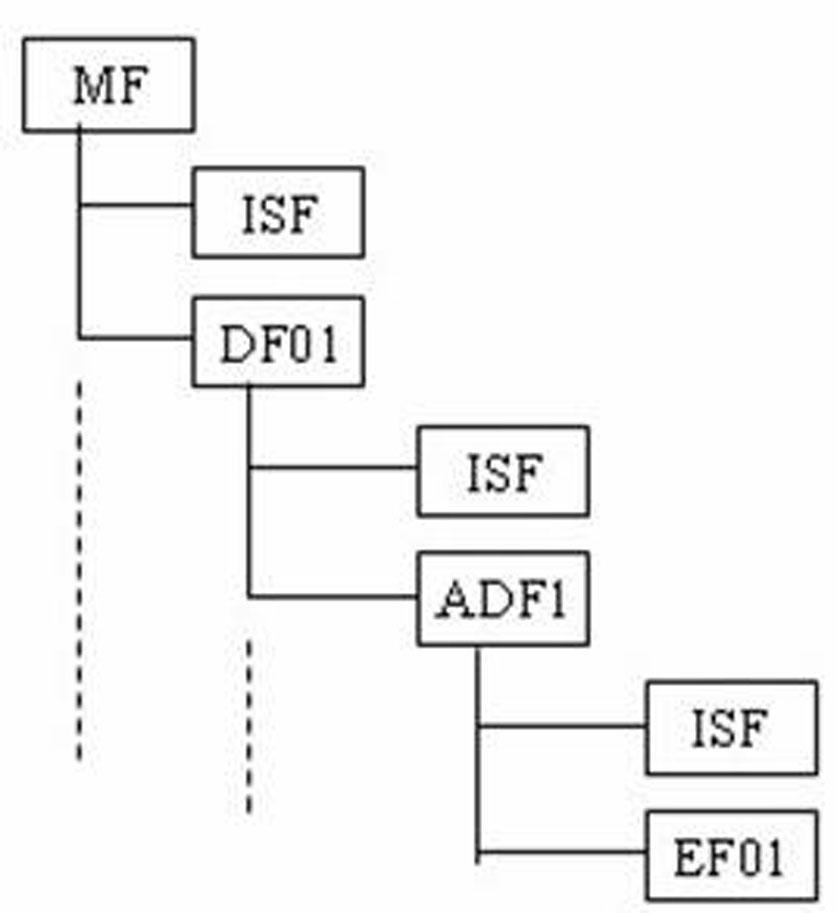
Method for realizing chip operating system (COS) safety mechanism of intelligent card
A technology of safety mechanism and implementation method, which is applied to record carriers, computer parts, and instruments used in machines, and can solve problems such as difficulty in implementing safety mechanisms and discrete safety attributes.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] According to the present invention, a smart card COS multi-dimensional security mechanism of individualized file access authority is proposed, which implements security status and security attributes by bit logic, and uses security control words to control the relationship between security attributes.
[0036] The control word is stored in the register and can be defined and modified. The operation and status corresponding to each bit of the predefined control word are reversely analyzed to complete the relevant control, operation, and status transfer.
[0037] Correspondingly, the security control word is to control the use of security attributes, specifically the control of access rights. The security control word is defined in the security attributes, and its initialization content should be expressed as a comprehensive prohibition of access rights, that is, no access rights are obtained. Authorization conditional on security attributes.
[0038]In one embodiment, bi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com