Multi-user spectrum allocation method capable of realizing defense of various attacks in cognitive radio network
A cognitive wireless network and spectrum allocation technology, applied in the fields of cognitive wireless network security and multi-user spectrum allocation, can solve the problems of increasing the complexity of cognitive networks, improve spectrum utilization, reduce attack power, and reduce destructive capabilities. small effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
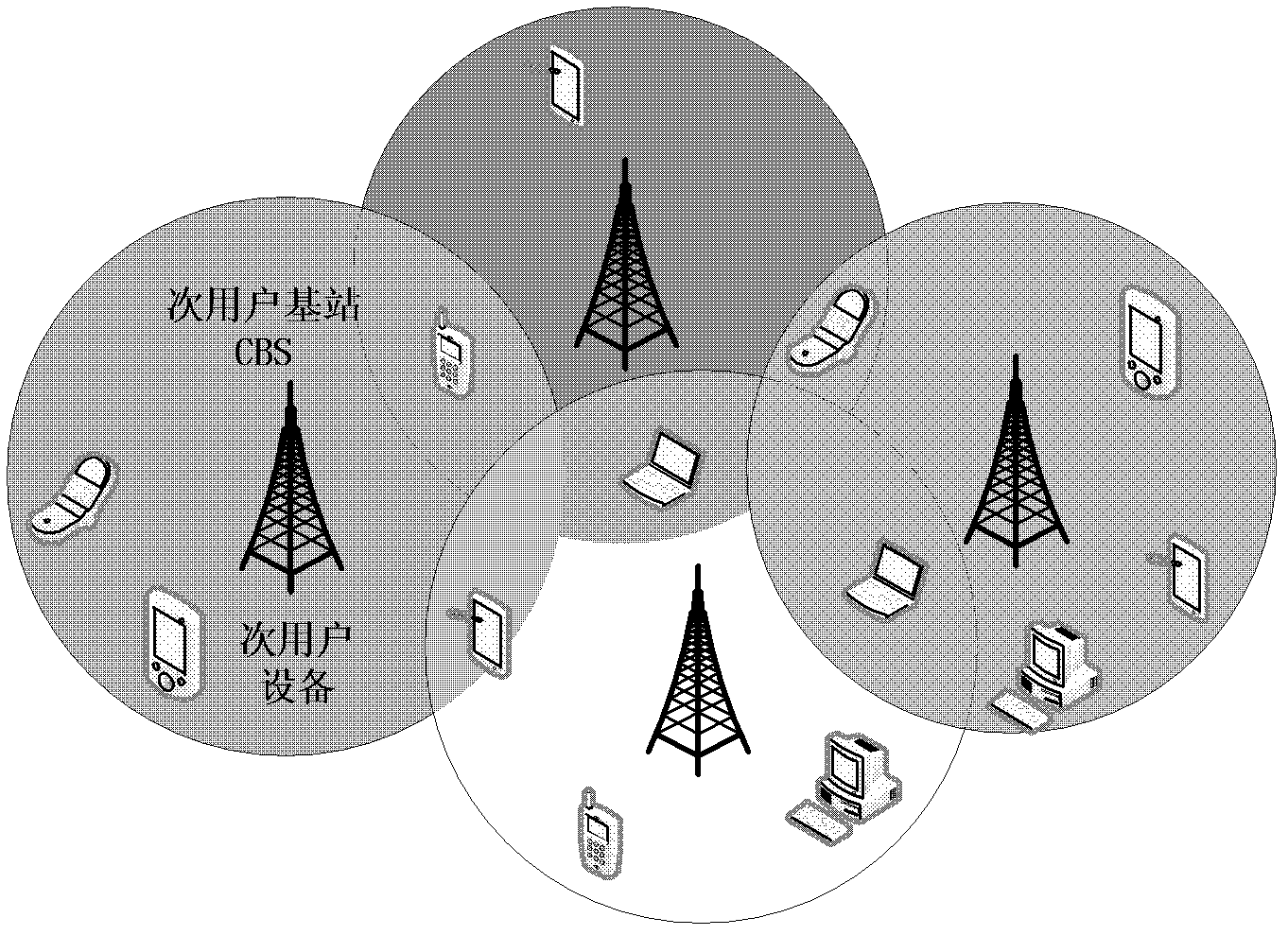
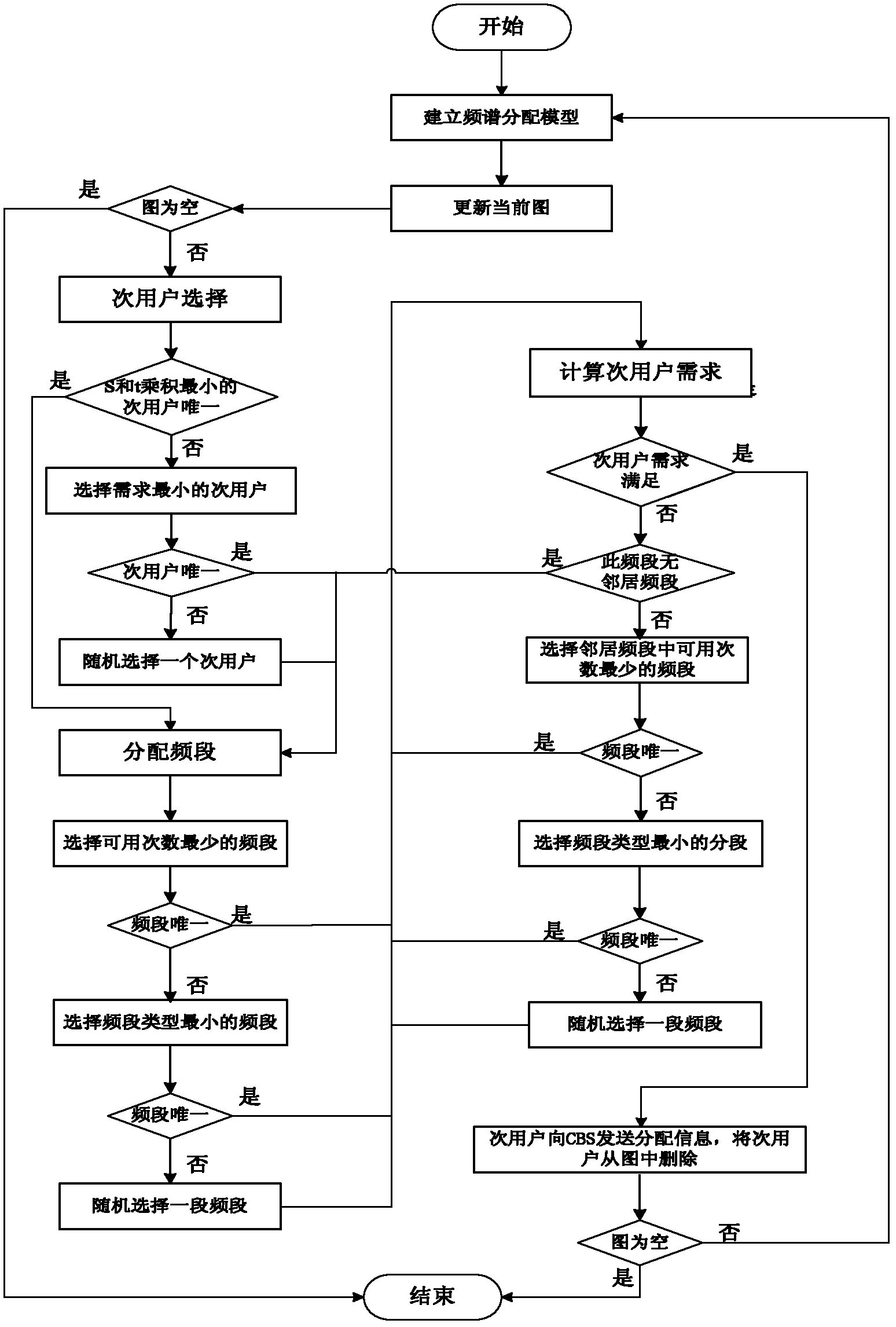
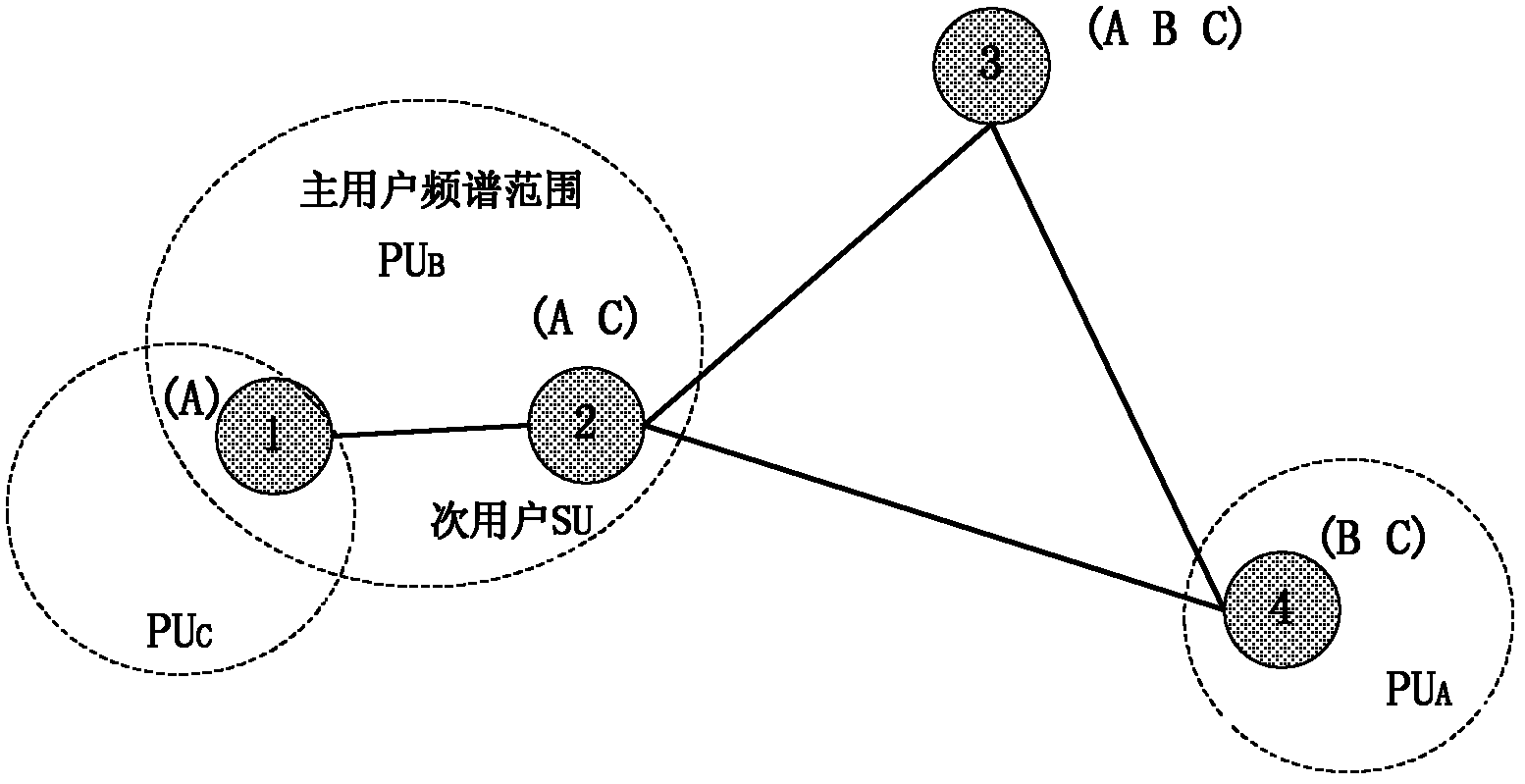
[0026] The present invention is suitable for figure 1 The central network shown in the scene includes the secondary user SU and the secondary user base station CBS; the secondary user SU and the secondary user base station CBS are connected wirelessly, and the secondary user base station CBS allocates spectrum to the secondary user; the secondary user SU and the secondary user base station CBS The information transmission between user base stations CBS is carried out on the control channel, and the information between the secondary users SU is transmitted through the data channel; the traditional single control channel is converted into multiple control channels by using segmentation technology, because the bandwidth required for control information is relatively small , according to the actual situation, the traditional single control channel can be divided into control channels and some data channels that meet the needs. The secondary user base station CBS dynamically adju...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com