Method for classifying pixel blocks of JPEG images and image falsification detecting and falsified area positioning methods based on same
A tampered, pixel-block technology, applied in character and pattern recognition, instruments, computer components, etc., can solve the problem of failing to detect and locate tampered areas
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
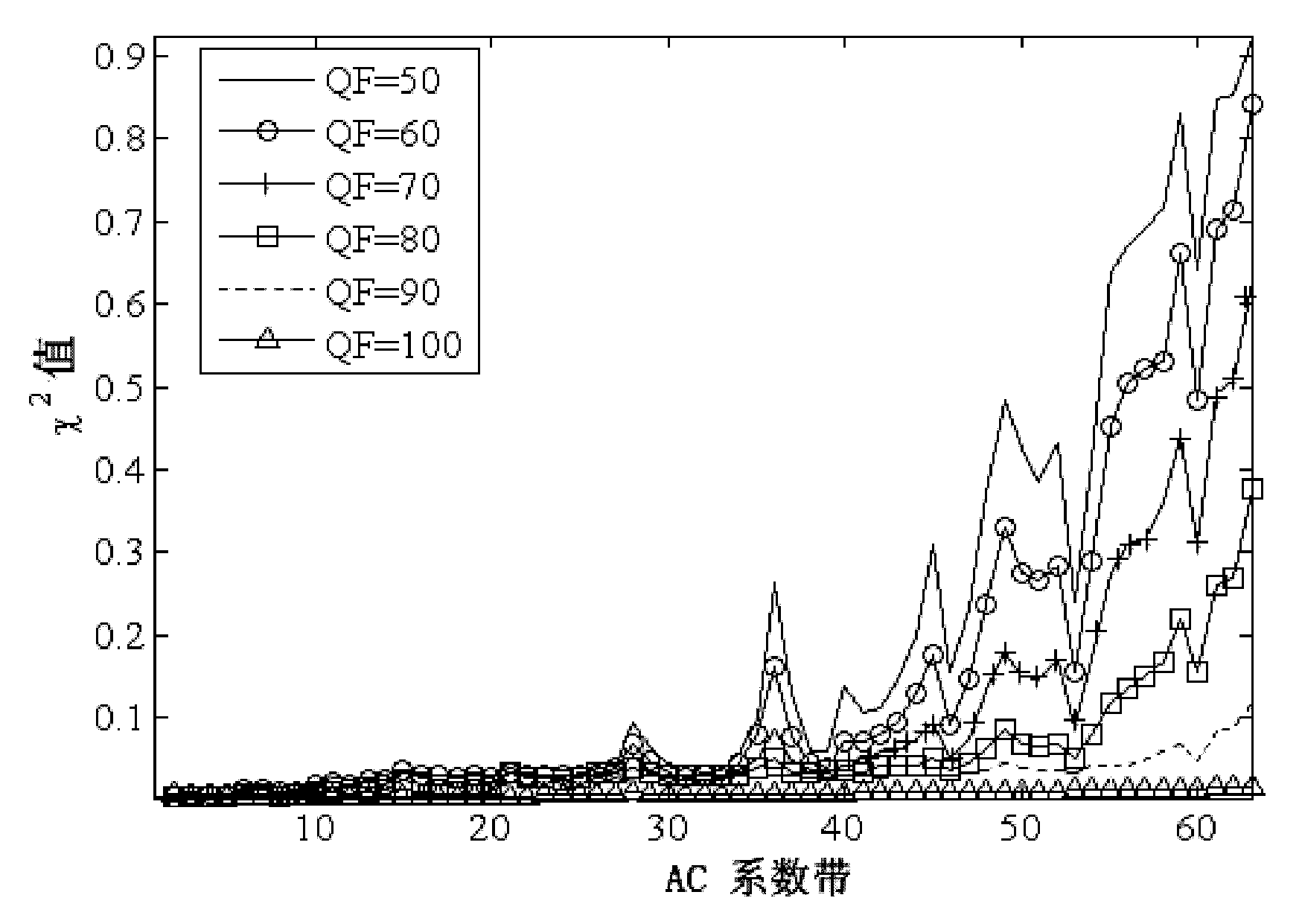
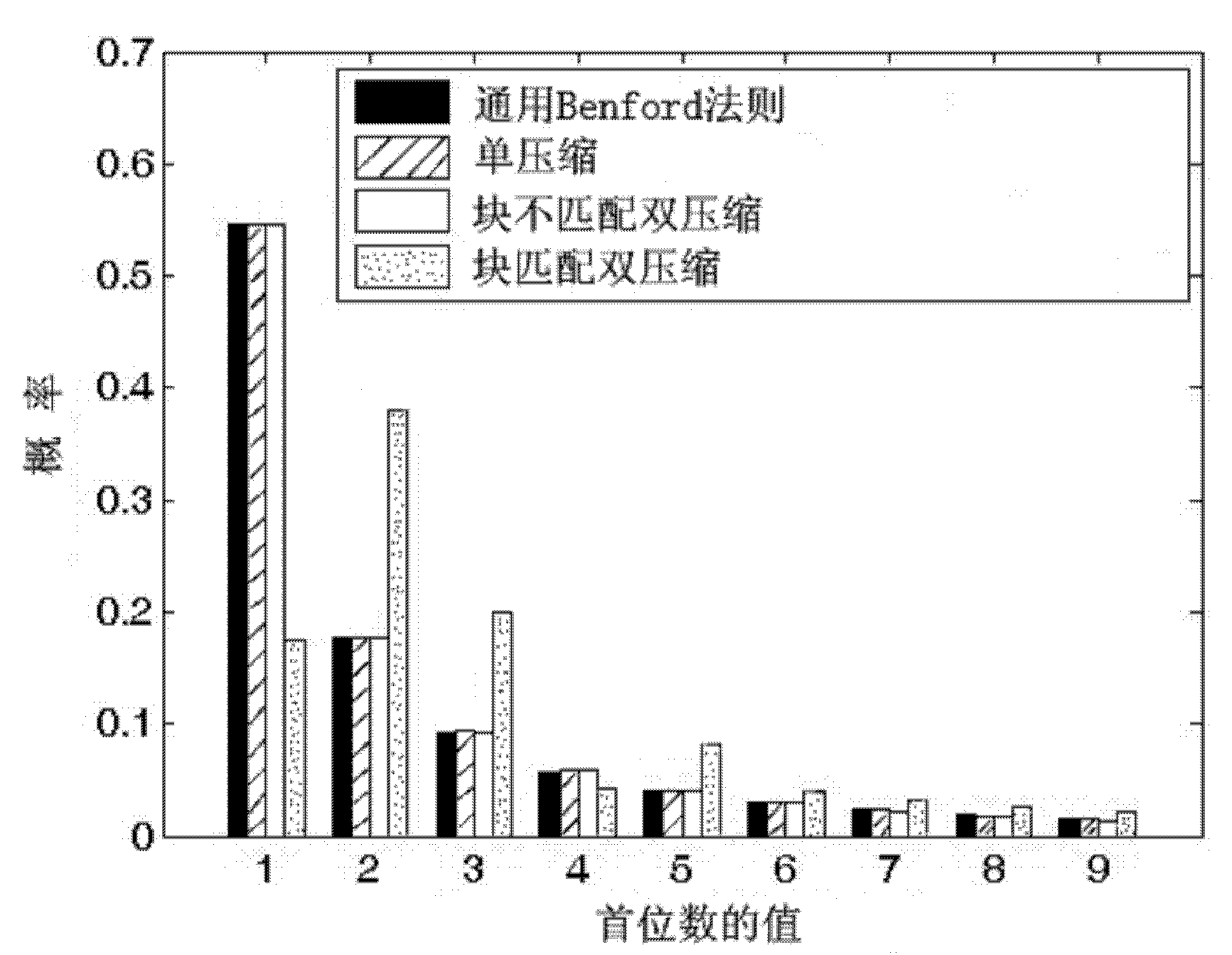
[0028] Assuming that a JPEG image is tampered and saved as JPEG format again, the tampered area and the non-tampered area generally have different compression histories. For copy-paste tampering and the insertion area is from an uncompressed image (referred to as "JPEG+uncompressed") and JPEG image retouched tampering (referred to as "JPEG+retouched") two tampering methods, the tampered area has undergone JPEG single compression, while the untampered area Experienced JPEG block-matching double compression; for copy-paste tampering and the insertion area comes from a JPEG image (abbreviation, "JPEG+JPEG") tampering method, the probability of the tampered area undergoing JPEG block-matching double compression is only 1 / 64, and the probability of experiencing JPEG block is not There is a 63 / 64 chance of matching double compression, and the untampered region has undergone JPEG block matching double compression. Our experiments show that the probability distributions of the first d...
Embodiment 2
[0030] A method for classifying pixel blocks of JPEG images, comprising the following steps:
[0031] (1) Select a sufficient number of uncompressed images to perform JPEG single compression and JPEG block matching double compression respectively, select the first 20 AC coefficient bands of the image, and calculate the first digit of the AC coefficient in each AC coefficient band (that is, 1 to 9 ) probability distribution, thereby obtaining the feature vector of 20×9=180 dimensions, and then training a classifier of single compression / double compression binary classification;
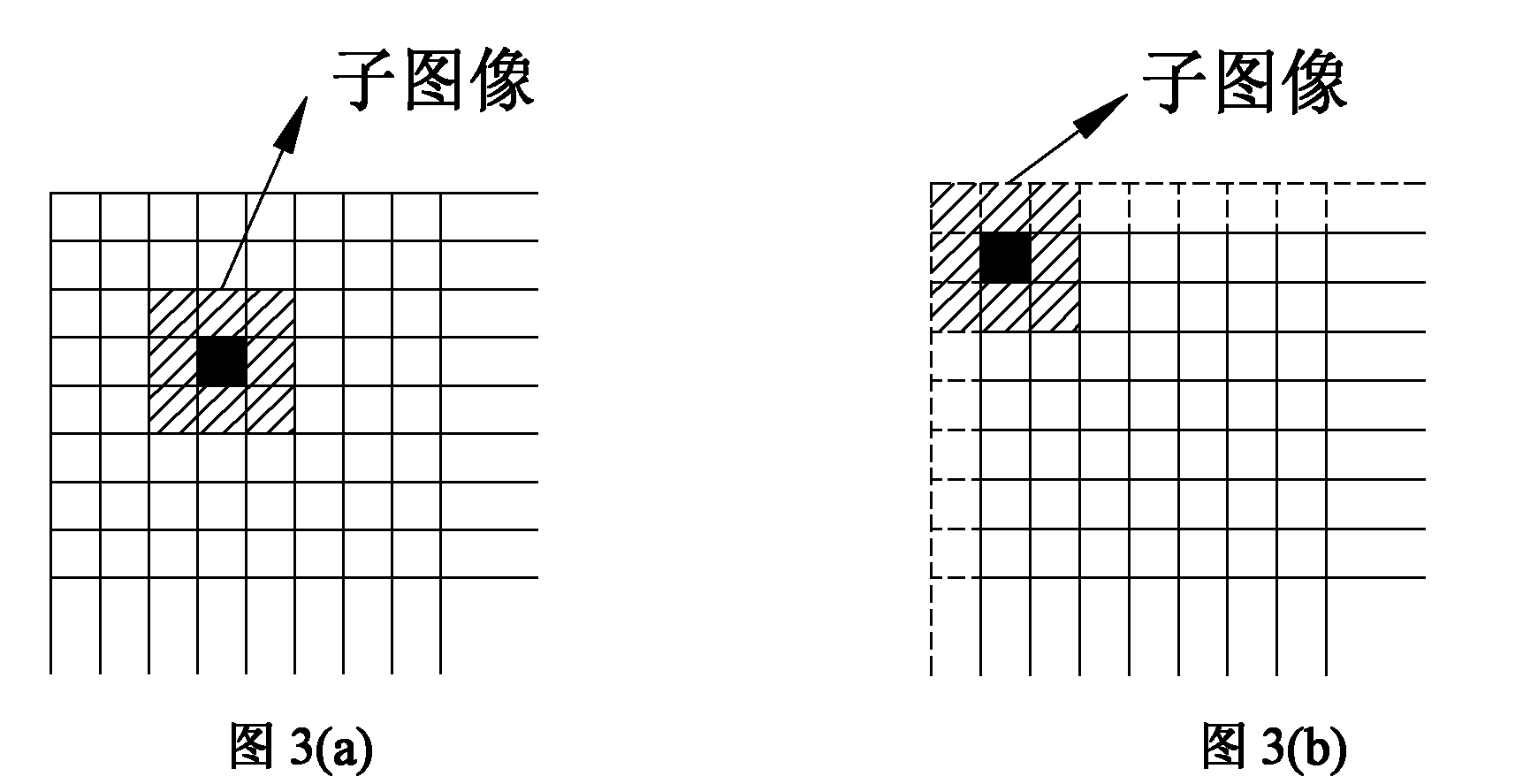
[0032] (2) Select a sub-image on the image to be detected, the method is: divide the JPEG image to be detected into continuous non-overlapping 8×8 pixel blocks, such as image 3 As shown, each small square in the figure is an 8×8 pixel block, image 3(a) is the sub-image selection method under normal circumstances, that is, select 3×3 (that is, the scheme where the value of n in (2n+1)×(2n+1) is 1) wi...
Embodiment 3
[0037] After adopting the method of embodiment 2 to classify all the pixel blocks in the image to be detected, in order to eliminate the influence of noise in the detection results and the resulting misjudgment, when more than M classification results are single-compressed pixel blocks form When the connected regions are connected, the image to be detected is judged as a tampered image, where M is set to 25.
[0038] Further, in order to locate the tampered area of the JPEG image, after all the pixel blocks in the image to be detected are classified by the method of Embodiment 2, all M or more (M is set to 25) classification results are found as Connected areas formed by single compressed pixel blocks, mark these areas as "1", which means tampered areas, and mark other areas as "0", that is, untampered areas.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com