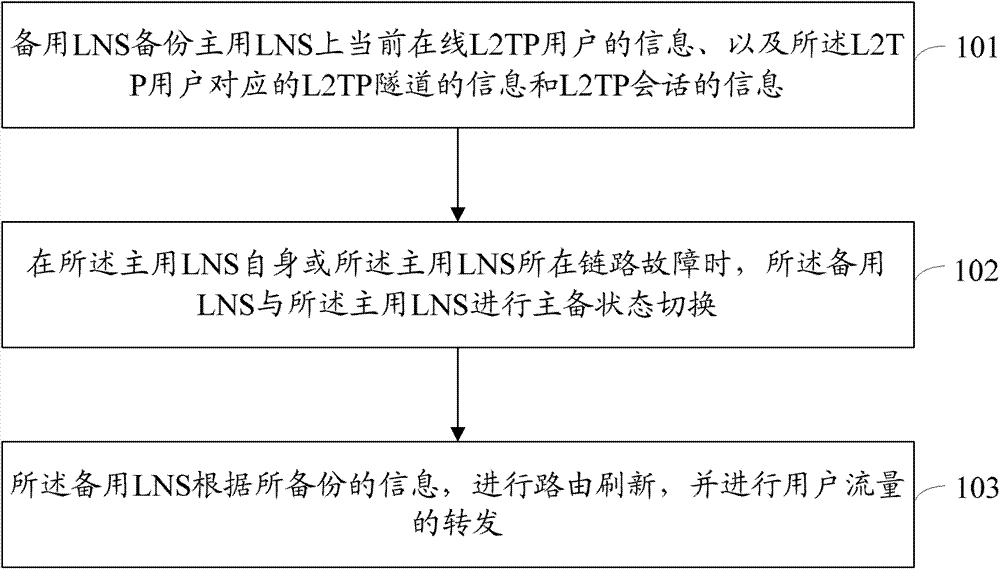
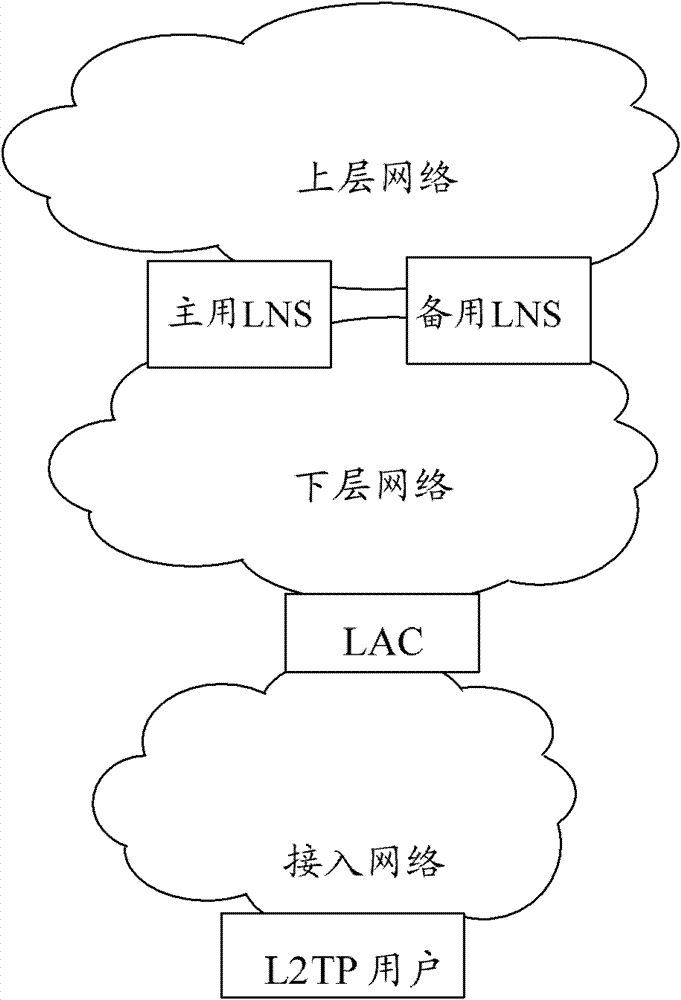
A protection method and system for l2tp network
A network and network equipment technology, applied in the protection method and system field of L2TP network, can solve problems such as inability to guarantee the normal progress of L2TP sessions, and does not support L2TP user backup, so as to achieve the effect of improving service reliability and user experience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
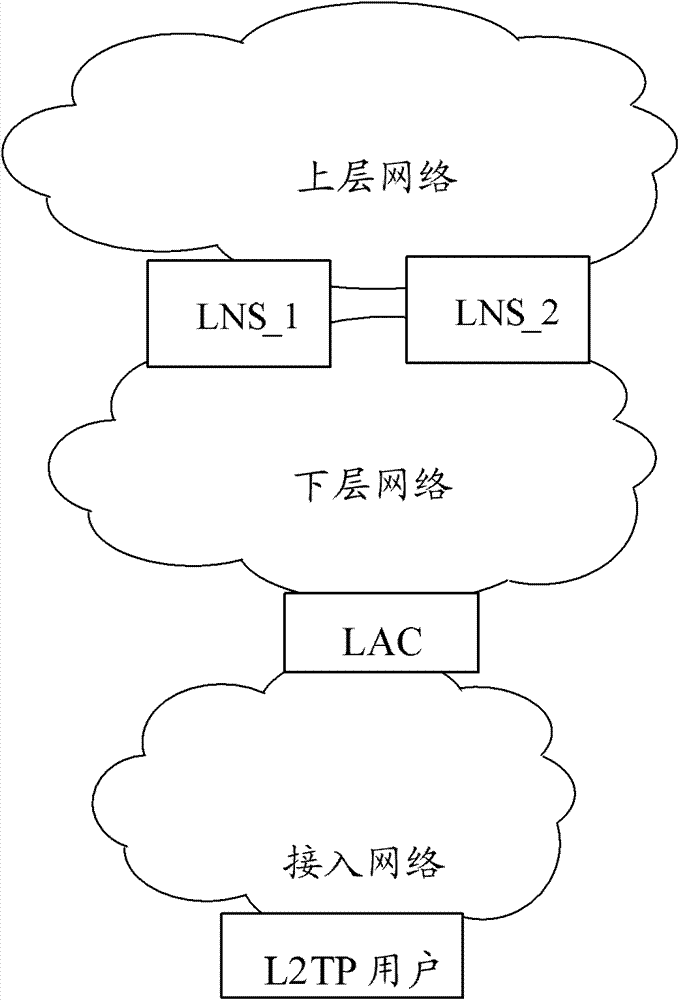
[0060] In this embodiment, the L2TP network topology is as follows image 3 As shown, it includes LNS_1, LNS_2, and LAC devices, wherein the link state detection is performed between LNS_1 and LNS_2 through the BFD protocol, and the LNS device state switching is performed through VRRP.
[0061] In this embodiment, to realize the process of troubleshooting in the L2TP network, refer to Figure 4 As shown, it specifically includes the following steps:
[0062] Step 401, performing active and standby configurations on LNS_1 and LNS_2 respectively;
[0063] Specifically, run the VRRP protocol between LNS_1 and LNS_2, configure their respective VRRP addresses on LNS_1 and LNS_2, and configure priority information on LNS_1 and LNS_2 respectively, where the priority of LNS_1 is greater than that of LNS_2, In this way, LNS_1 is configured as the active state, LNS_3 is in the standby state, and LNS_3 is designated as the backup device of LNS_1. LNS_1 receives the online request of th...
Embodiment 2
[0083] In this embodiment, the L2TP network topology is as follows Figure 5As shown, it includes three LNS devices, LNS_1, LNS_2, and LNS_3, and two LAC devices, LAC_1 and LAC_2. Among them, LAC_1 corresponds to LNS_1, LAC_2 corresponds to LNS_2, LNS_1 and LNS_2 are active devices, LNS_3 is a backup device, and the connection between LNS_1 and LNS_3 Run the BFD protocol between LNS_2 and LNS_3 to detect the link status, and run VRRP to switch between the active and standby states, realizing the function of using one LNS to back up L2TP users for multiple LNSs.
[0084] In this embodiment, to realize the process of troubleshooting in the L2TP network, refer to Image 6 As shown, it specifically includes the following steps:
[0085] Step 601, performing active and standby configurations on LNS_1, LNS_2, and LNS_3 respectively;
[0086] Specifically, run the VRRP protocol between LNS_1 and LNS_3, and between LNS_2 and LNS_3, configure LNS_1 and LNS_2 as active LNSs, and LNS_3...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com