Method for forwarding internet protocol security (IPSec)
A data item, encryption and decryption technology, applied in the field of network security, can solve problems such as bandwidth waste and increased costs, and achieve the effect of reducing costs and improving user experience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] The specific implementation manners of the present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments. The following examples are used to illustrate the present invention, but are not intended to limit the scope of the present invention.
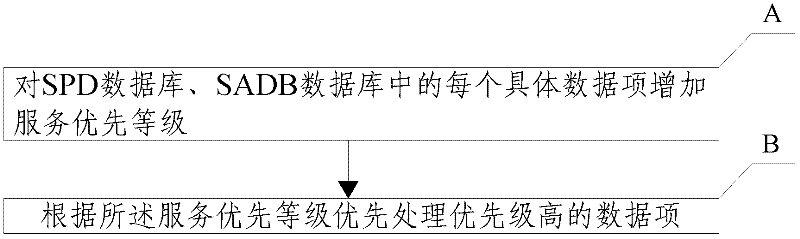
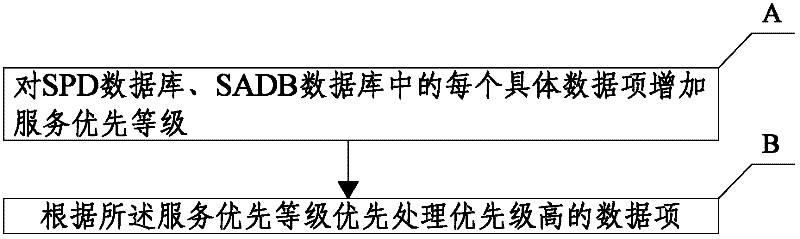
[0021] Such as figure 1 As shown, a kind of Ipsec forwarding method of the present invention comprises the following steps:
[0022] A: Increase the service priority level for each specific data item in the SPD database and SADB database;
[0023] B: Prioritize processing of data items with high priority according to the service priority.
[0024] In step B, the cpu obtains the SPD or SADB data item corresponding to the message that needs to be encrypted and decrypted, and then adds the data item that needs to be encrypted / decrypted to the predetermined encryption and decryption queue according to the service priority. Specifically, it is realized through the following ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com