Method for detecting extra-large ring hidden dangers based on basic configuration data acquired by network management system of manufacturer
A technology for configuring data and network management, which is applied in the field of network transmission and communication resource management, and can solve the problems of consuming human resources, unintuitive analysis results, and consuming a lot of resources
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0023] Below with the accompanying drawings ( Figure 1-Figure 5 ) to illustrate the present invention.
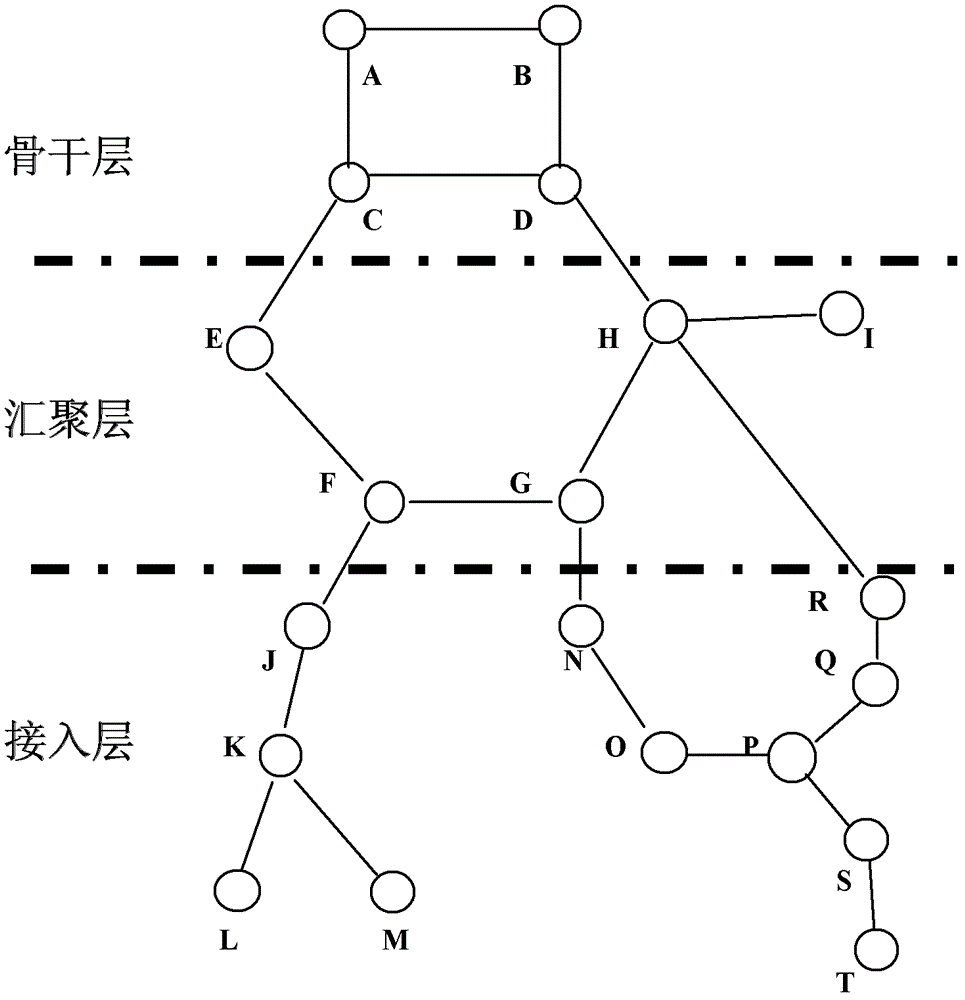
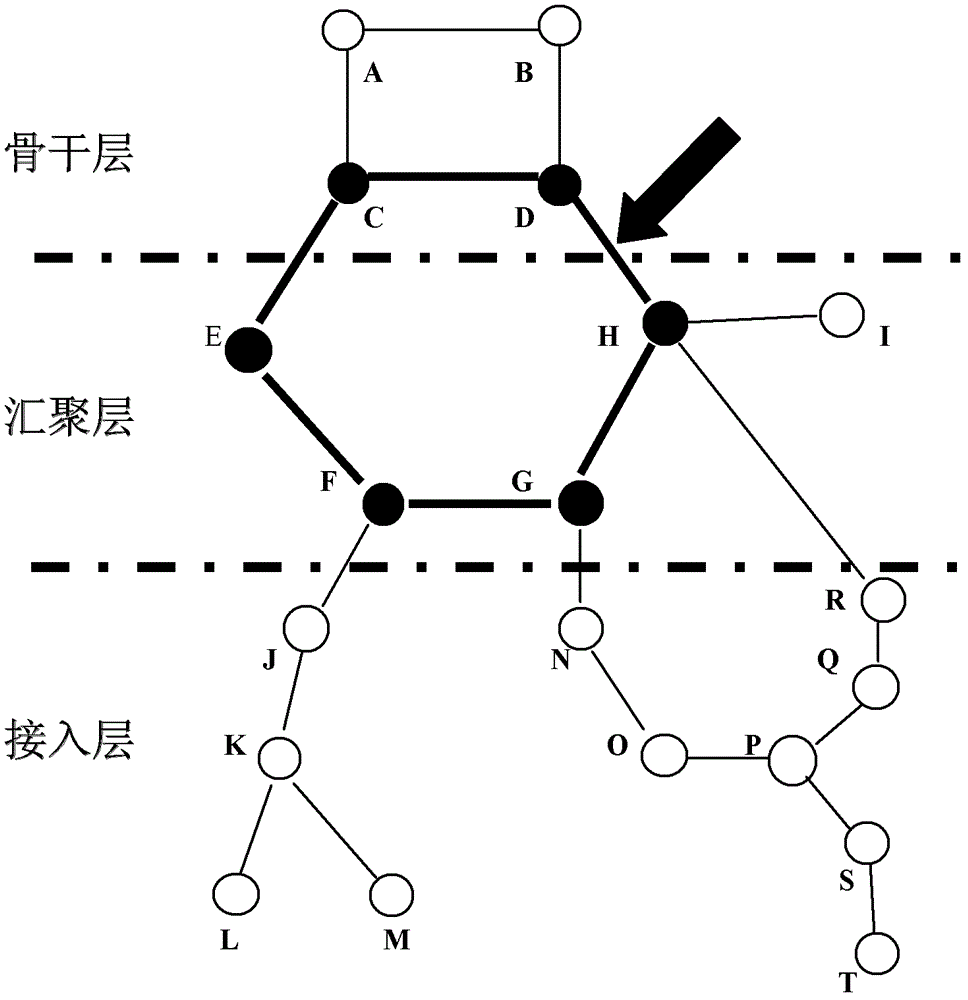
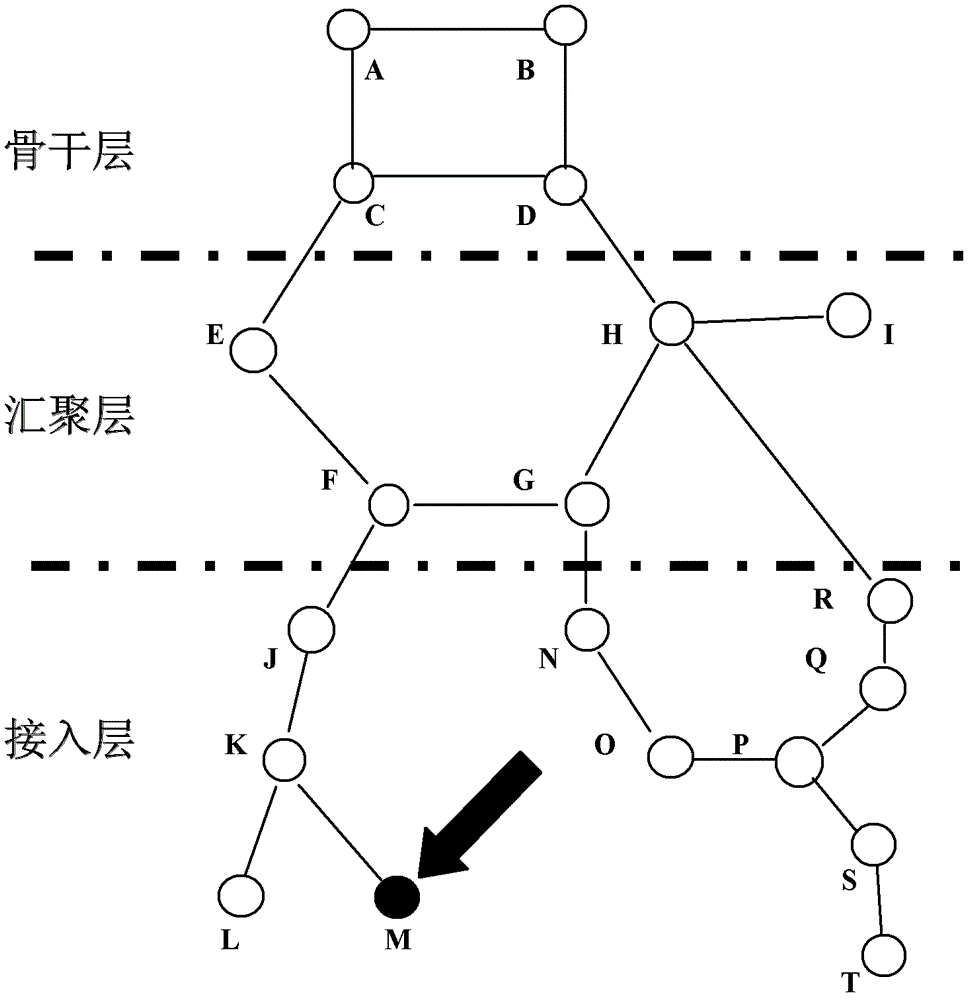
[0024] figure 1 It is a schematic diagram of the topology structure of the transmission network. figure 1 The backbone layer has network elements A, B, C, and D; the aggregation layer has network elements E, F, G, H, and I; the access layer has network elements J, K, L, M, N, O, P, and Q , R, S, T. 1. Analysis of the transmission network structure: The basic data required for the analysis of the transmission network structure comes from two parts: one is from the CORBA (Common Object Request Broker Architecture, commonly known as northbound interface) interface provided by the network management of the manufacturer, through The CORBA interface automatically collects transmission network element objects, topological connections between network element objects, cross-connection data within network elements, and channel data composed of transmission network elements; the s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com