Virtual-private-network-based multi-instance Ethernet ring protection switching method
A technology of virtual private network and protection switching, which is applied in the directions of network interconnection, data exchange network, and data exchange through path configuration. Problems such as logical port protection and inability to provide VPN service group protection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0048] Method of the present invention, concrete steps are as follows:
[0049] (1) The specific steps for creating an Ethernet ring network protection instance based on a virtual private network:
[0050] (1.1) Create an Ethernet ring network protection instance 1 on each node on the ring. This instance includes 2 ring ports, wherein instance 1 of a certain node is designated as the RPL owner node, and a certain ring port is an RPL link;
[0051] (1.2) Create an Ethernet ring network protection instance 2 on each node on the ring. This instance contains 2 ring ports, which are the same as the ring ports of instance 1. Instance 2 of a certain node is designated as the RPL owner node. A ring port is an RPL link;
[0052] (2) Specific steps of mapping from a virtual private network service group to an Ethernet ring network protection instance:
[0053] (2.1) Map virtual private network service group 1 (this service group includes 1-100 altogether 100 virtual private network se...
example 2
[0054] (2.2) mapping virtual private network service group 2 (this service group includes 100 virtual private network services of 101-200) to instance 2;
[0055] (3) Concrete steps for controlling the mapping of virtual private network services to Ethernet ring network instances:
[0056] (3.1) Create and control virtual private network service 1, and then map the service to instance 1;
[0057] (3.2) Create a control virtual private network service 2, and then map the service to instance 2.
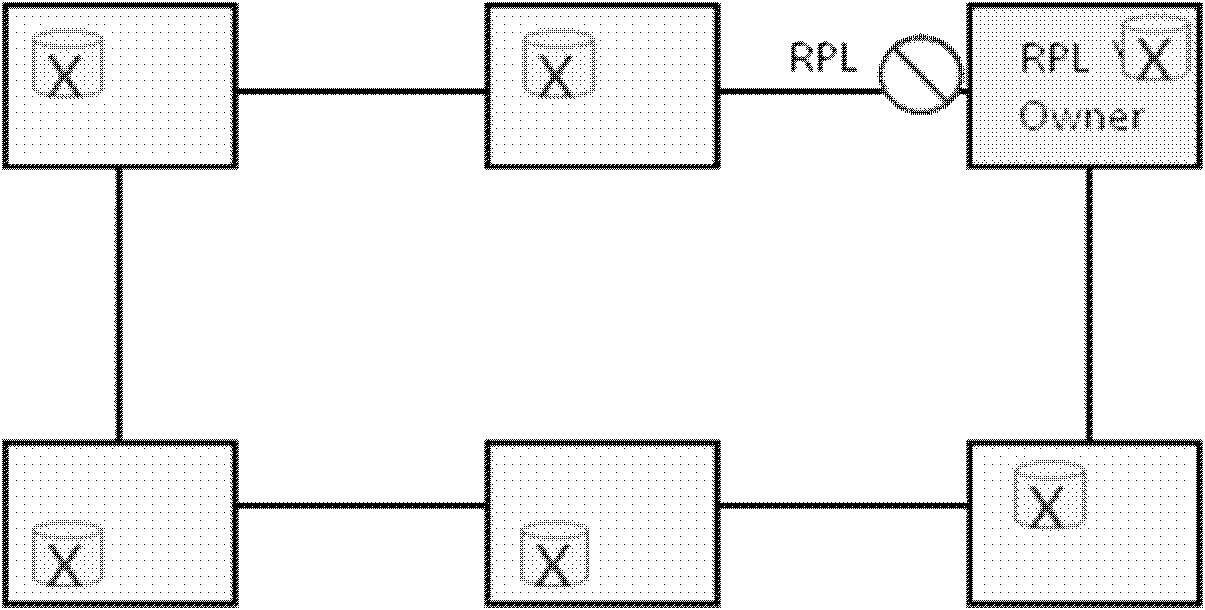
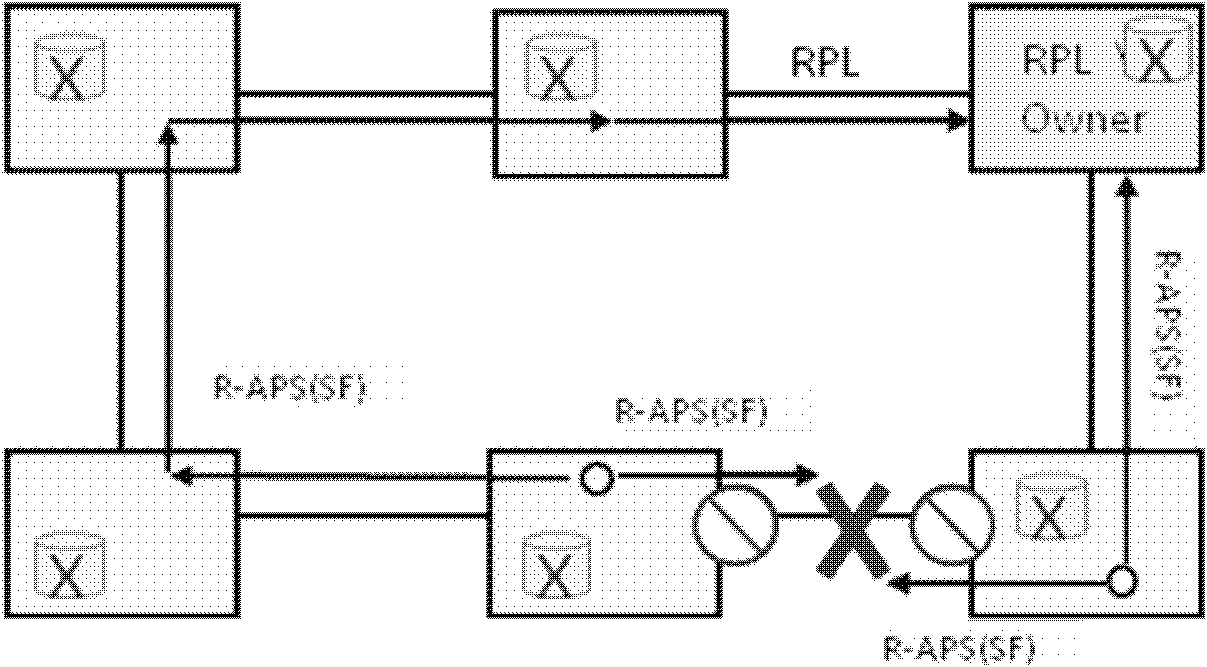
[0058] like figure 1 , figure 2 , image 3 , Figure 4 As shown, the basic idea of the standard Ethernet ring protection protocol is to use a specific link to protect the entire ring. We call this link a Ring Protection Link (RPL). like figure 1 As shown in the case of Ethernet ring network protection under normal conditions, if other links on the ring are not faulty, this link is responsible for blocking the service flow to prevent the occurrence of loops. The special networ...
Embodiment 2
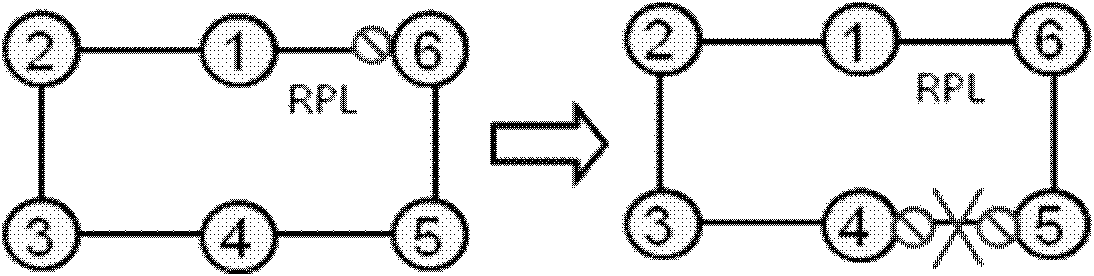
[0066] For shared virtual private network services of logical tangent rings, such as Image 6 As shown, this embodiment provides a solution. At the tangent node, the virtual private network service is mapped to multiple ring instances, and different logical ports of the virtual private network service are on different logical rings, and are affected by different ring instances control.
[0067] This embodiment includes the following steps:
[0068] (1) Create instance 1 on nodes 1, 2, and 3, including ring ports ge-bs / 1 and ge-bs / 2;
[0069] (2) Map virtual private network service group 1 (including 1-100, a total of 100 services) to instance 1;
[0070] (3) Create control virtual private network service 1 on nodes 1, 2, and 3 and map it to instance 1;
[0071] (4) Create instance 2 on nodes 3, 4, and 5, where nodes 4, 5 contain ring ports ge-bs / 1 and ge-bs / 2, and node 3 contains ring ports ge-bs / 3, ge- bs / 4;
[0072] (5) Map virtual private network group 1 (including 1-1...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com