Data protection method, device and system for storage device
A storage device and data technology, applied in the direction of preventing unauthorized use of memory, input/output to record carriers, etc., can solve the problems of costly legal user protection methods, inflexibility, etc., to maintain interests, prevent illegal transmission, and protect reading Take the effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
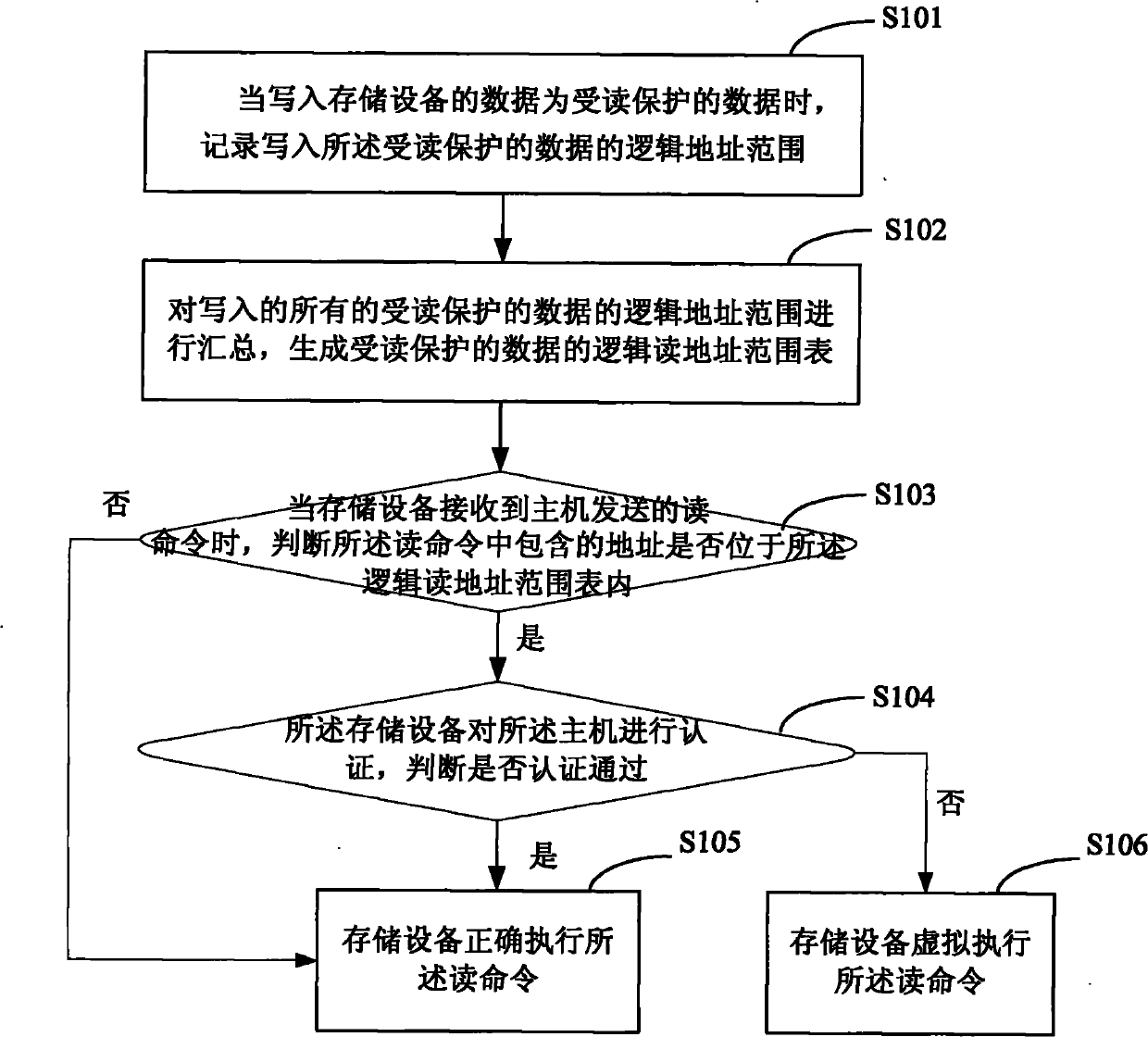
[0039] figure 1 It shows the implementation process of the storage device data protection method provided by Embodiment 1 of the present invention, and its specific steps are as follows:
[0040] In step S101, when the data written into the storage device is read-protected data, record the logical address range for writing the read-protected data;
[0041] In the embodiment of the present invention, the read-protected data is user-defined data, and the present invention can provide the user with a specific interface for the user to define the read-protected data.
[0042] In step S102, the logical address ranges of all read-protected data written are summarized to generate a logical read address range table of read-protected data;
[0043] In the embodiment of the present invention, the address range in the logical read address range table of the read-protected data can be set as required, and the size of the range can be different, and it can be a continuous range or a disco...
Embodiment 2
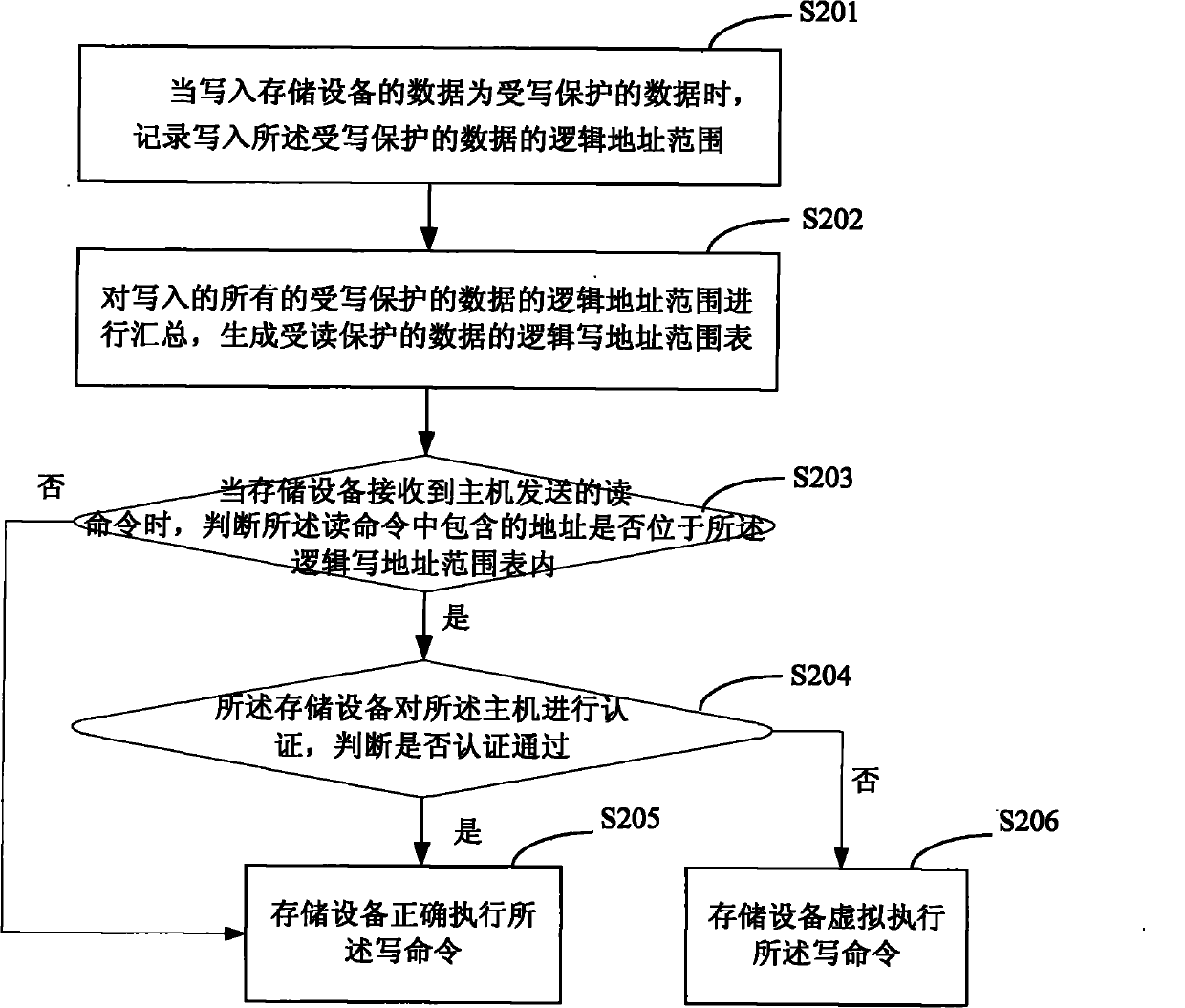
[0050] In this embodiment of the present invention, the method for protecting data of a storage device, in addition to including the steps in Embodiment 1, is as follows: figure 2 As shown, the following steps are also included:
[0051] In step S201, when the data written into the storage device is write-protected data, record the logical write address range for writing the write-protected data;
[0052] In step S202, the logical address ranges of all write-protected data are summarized to generate a logical write address range table of write-protected data;
[0053] In step S203, when the storage device receives the write command sent by the host, it is judged whether the address contained in the write command is located in the logical write address range table; if yes, then execute step S204, otherwise execute step S205;
[0054] In step S204, the storage device authenticates the host, and judges whether the authentication is passed; if yes, execute step S205, otherwise e...
Embodiment 3
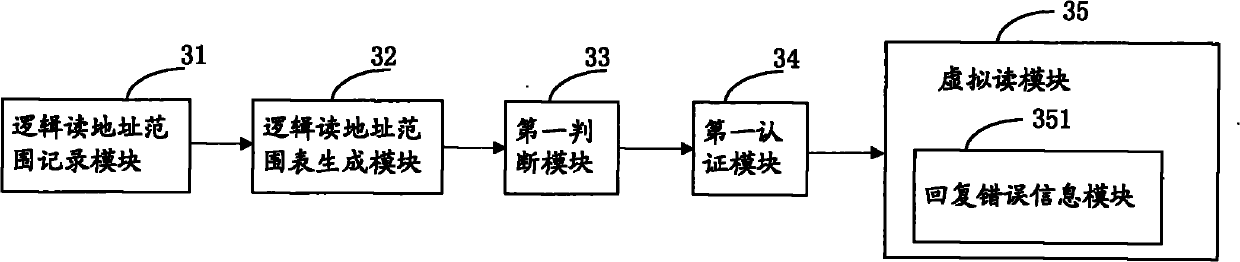
[0059] The purpose of the embodiments of the present invention is to provide a protection device for storing device data, image 3 It shows a structural block diagram of an apparatus for protecting data of a storage device provided by an embodiment of the present invention. For ease of description, only parts related to the embodiment of the present invention are shown in the figure.
[0060] The device for protecting data of the storage device includes:
[0061] A logical read address range recording module 31, configured to record the logical address range of the read-protected data written into the read-protected data when the data written into the storage device is read-protected data;
[0062] Logical read address range table generating module 32, used for summarizing the logical address ranges of all read-protected data written, and generating the logical read address range table of read-protected data;
[0063] The first judging module 33 is configured to judge whether...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com