Web vulnerability scanning method and device based on infiltration technology
A vulnerability scanning and web browser technology, applied in the field of computer networks, can solve problems such as performance discounts
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
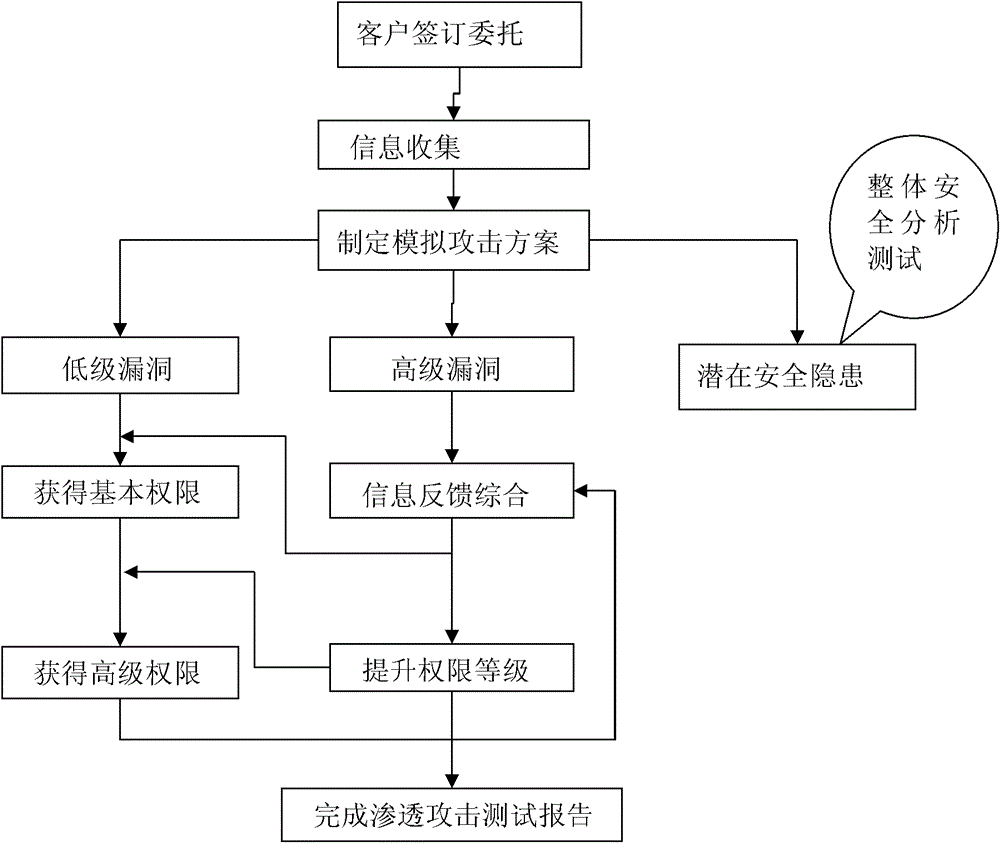
[0028] The present invention will be further described below in conjunction with drawings and embodiments. The invention aims to provide a tool for scanning website security loopholes. Automatically and efficiently check the loopholes and security risks existing in web applications, and evaluate the system security.
[0029] The present invention mainly improves the loophole scanning method of the traditional web server, and the method is as follows: adopt a loophole scanner, and the loophole scanner structure includes four parts: client, browser, scanning host and web server, such as figure 1 As shown, the scanning host part includes a control platform, a scanning mode setting module, a scanning module and a vulnerability database. The user sets the scanning mode in the scanning mode setting module through the control platform, and the single-level scanning in the scanning module The depth and breadth are expanded to two times or more, and finally the target website is scann...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com