Method and device for capturing malicious code of mobile terminal
A malicious code and mobile terminal technology, which is applied in the field of mobile terminal malicious code capture, can solve the problem that mobile terminal malicious code is difficult to capture, and achieve the effect of making up for the untimely capture and response
Inactive Publication Date: 2010-12-29
BEIJING ANTIY NETWORK SAFETY TECH CO LTD
View PDF2 Cites 4 Cited by
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
In view of the above problems, considering the current situation that the unique transmission path of mobile terminals and the traditional computer malicious code capture method cannot be applied, the technical problem to be solved by the present invention is to design a capture system and equipment for the spread of mobile terminal malicious codes, and to solve the problem of mobile terminal malicious codes. elusive status quo
a. Capture the malicious code of pseudo-terminals for mobile data services
Method used
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
View moreImage
Smart Image Click on the blue labels to locate them in the text.
Smart ImageViewing Examples
Examples
Experimental program
Comparison scheme
Effect test
Embodiment Construction
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More PUM
 Login to View More
Login to View More Abstract
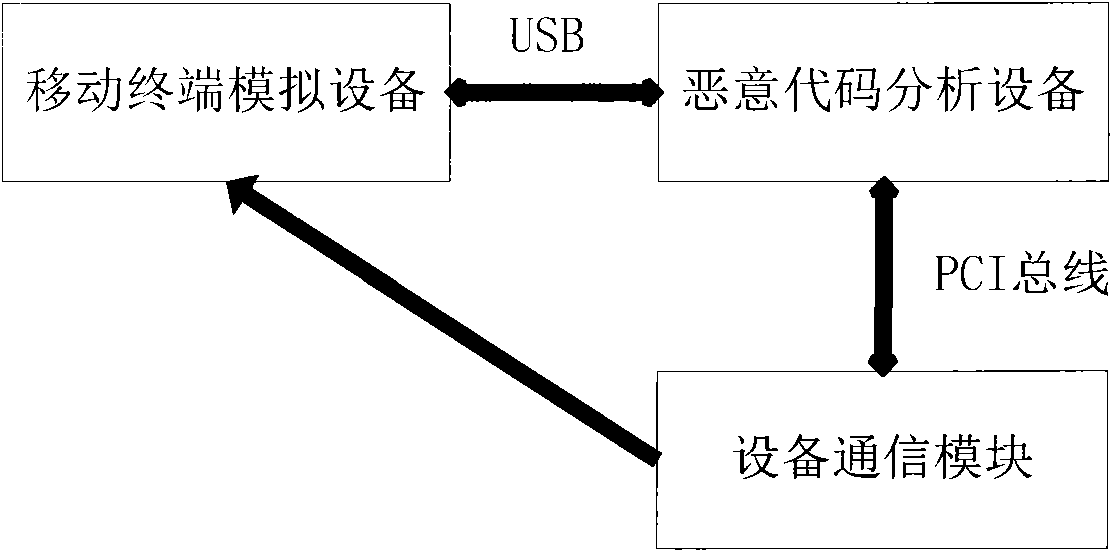
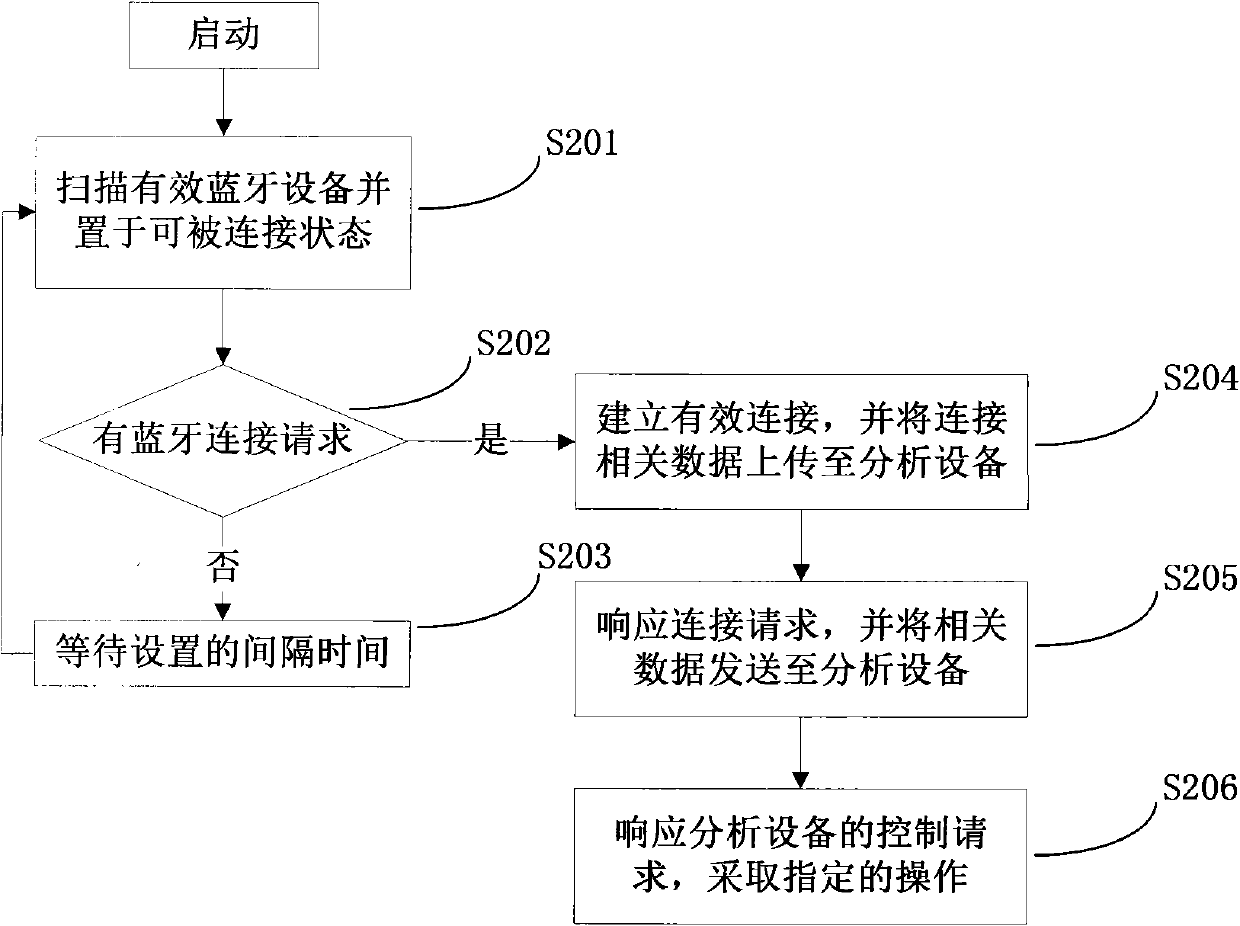
The invention discloses a method and a device for capturing a malicious code of a mobile terminal. The method comprises the following steps of: capturing a malicious code of a pseudo terminal of a mobile telephone data service; capturing a malicious code of a mobile telephone Bluetooth; and updating a terminal virus database by adopting PUSH technology. The device comprises mobile terminal analog equipment and malicious code analytical equipment. The problem of untimely capturing the malicious code of mobile terminal equipment is solved to effectively solve the problems of slow capturing and response of the malicious code of the current mobile terminal, and provide strong support for better solving the propagation event of the malicious code of the mobile terminal.
Description
technical field The invention relates to the technical field of network security, in particular to a method and device for capturing malicious codes of a mobile terminal. Background technique Malicious code is a program with malicious intent that may harm the machine on which it executes or the network over which it propagates. The damage caused by malicious code has increased dramatically in recent years. Therefore, malicious code detection is an important aspect of software security. With the development of communication technology, mobile phones have become indispensable for work and life. The expansion of mobile entertainment and business functions requires that mobile phone functions become increasingly complex and intelligent. The processor performance and storage capacity of mobile phones are all moving towards PC. At the same time, there is also a trend of the mobile phone operating system from a number of independent companies working behind closed doors to the u...
Claims
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More Application Information
Patent Timeline
 Login to View More
Login to View More IPC IPC(8): G06F21/00G06F21/56
Inventor 潘宣辰肖新光
Owner BEIJING ANTIY NETWORK SAFETY TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com