System operation method using hardware lock and electronic device thereof
A technology of electronic devices and operating methods, applied in computer security devices, electrical digital data processing, instruments, etc., can solve data theft and other problems, and achieve the effect of preventing data from being stolen, maliciously intruded or cracked by hackers
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
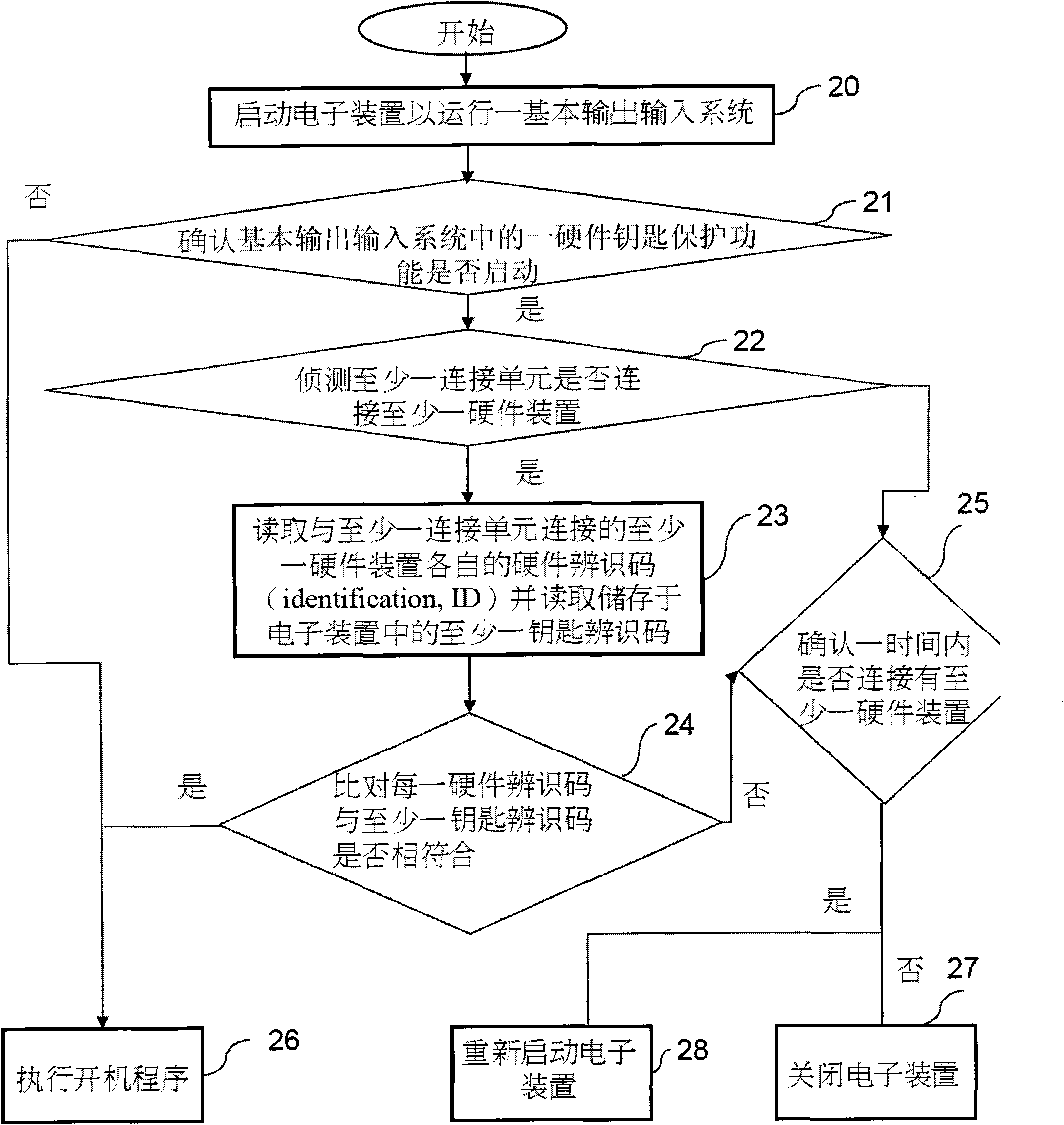
[0031] figure 1 It is a flow chart of the system operation method using hardware lock according to the first embodiment of the present invention.
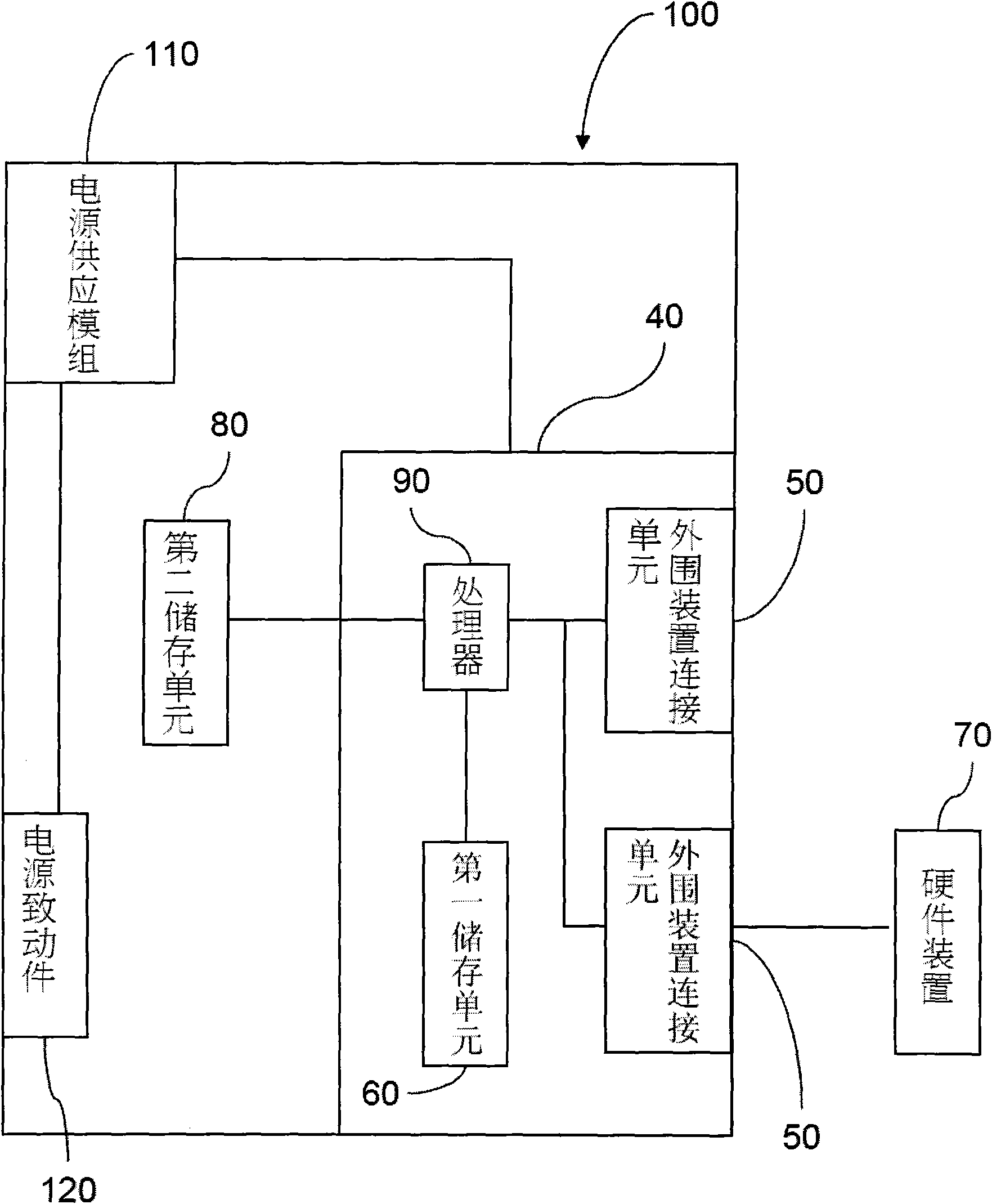
[0032] Please refer to figure 1 , the method for operating a system using a hardware lock in this embodiment is applied to an electronic device having at least one connection unit.
[0033] In the method for operating a system using a hardware lock according to the present embodiment, the first step (step 20 ) starts up the electronic device to run a Basic I / O System (BIOS).
[0034] Wherein, the method for starting the electronic device can be by turning on the power actuator (such as: power switch, power button, etc. or plugging a hardware device with a Universal Serial Bus (Universal Serial Bus, USB) interface into the electronic device correspondingly. connection port), or other means to activate the electronic device.
[0035] Among them, using a hardware device with a Universal Serial Bus (Universal Serial Bus, USB) interf...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com