Method for deleting file
A file deletion and file technology, applied in special data processing applications, instruments, electronic digital data processing, etc., can solve problems such as loss of enterprises or units or even countries, leakage of confidential data, and inability to clear and clean data.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0011] In order to make the purpose, technical solutions and advantages of the present invention clearer, the implementation of the present invention will be further described in detail below in conjunction with the accompanying drawings:
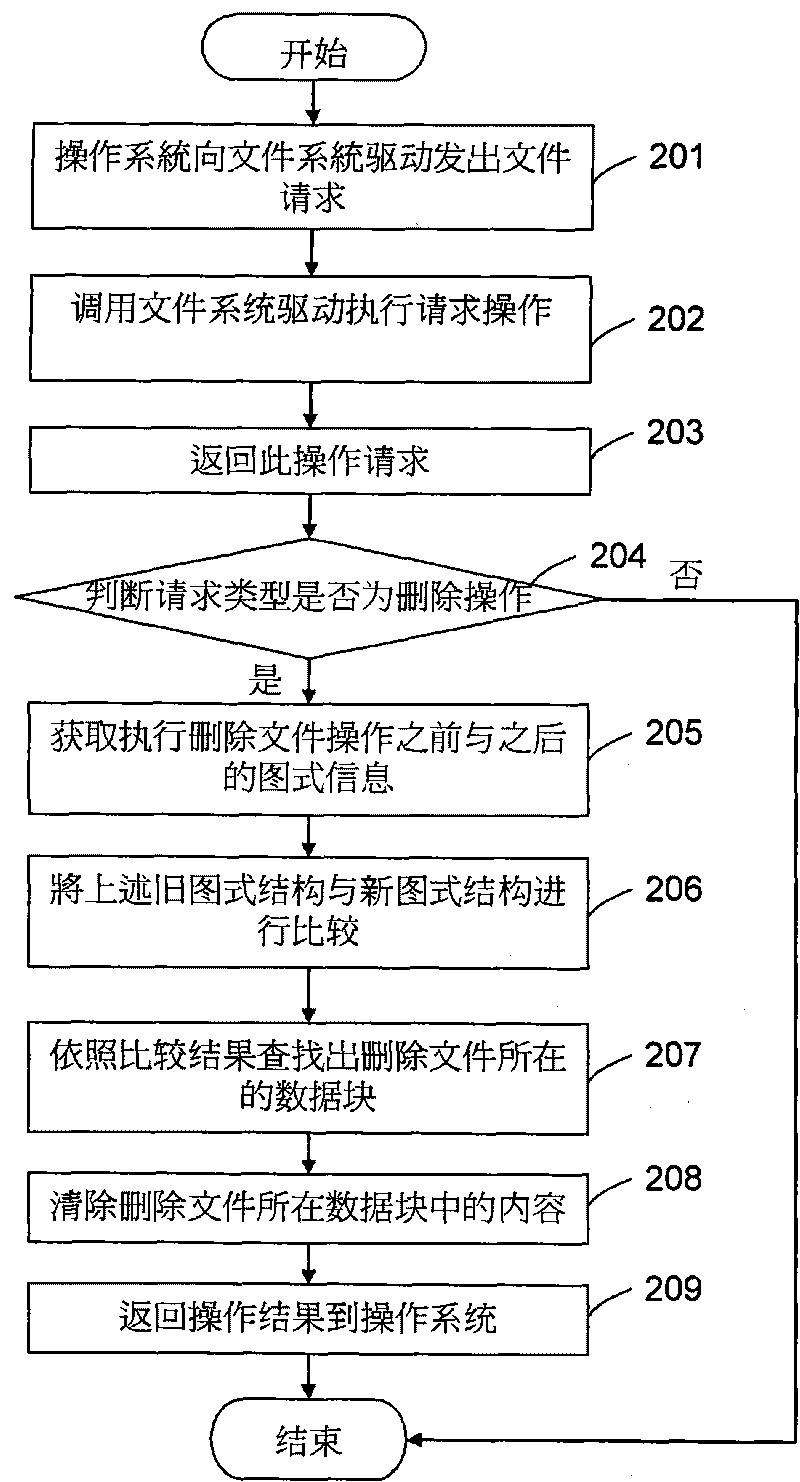
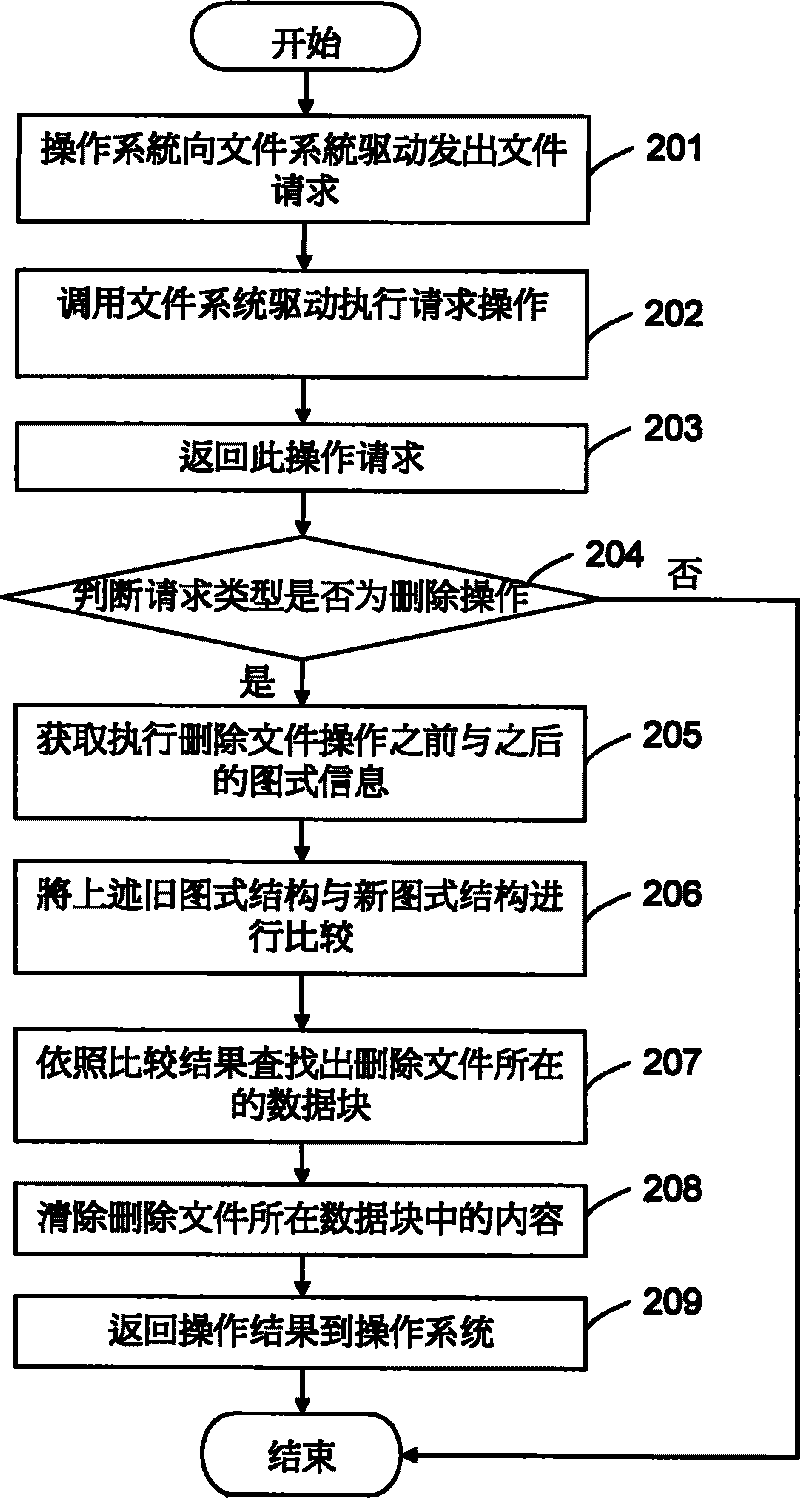
[0012] see figure 1 , this embodiment provides a method for securely deleting a file, the method includes: firstly, the file system sends a file request 201 to the file system driver, for example, requesting to perform a deletion operation on a certain file. Call the file system driver to execute the corresponding request operation 202 according to the above request, then return the operation request 203, and then judge the operation request type to confirm whether it is a delete operation 204, if it is not a delete operation, then end; otherwise, obtain the file delete operation The previous file system schema structure and the information 205 in the schema after the delete operation.
[0013] Here, it is necessary to establish a file sys...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com