Reliable network management method based on TCPA/TCG reliable network connection
A network connection and network management technology, which is applied in the field of trusted network management, can solve problems such as loss of network management and control, administrator system work, and inability to guarantee agent security, etc., and achieve the effect of simplifying the implementation steps and preventing malicious attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
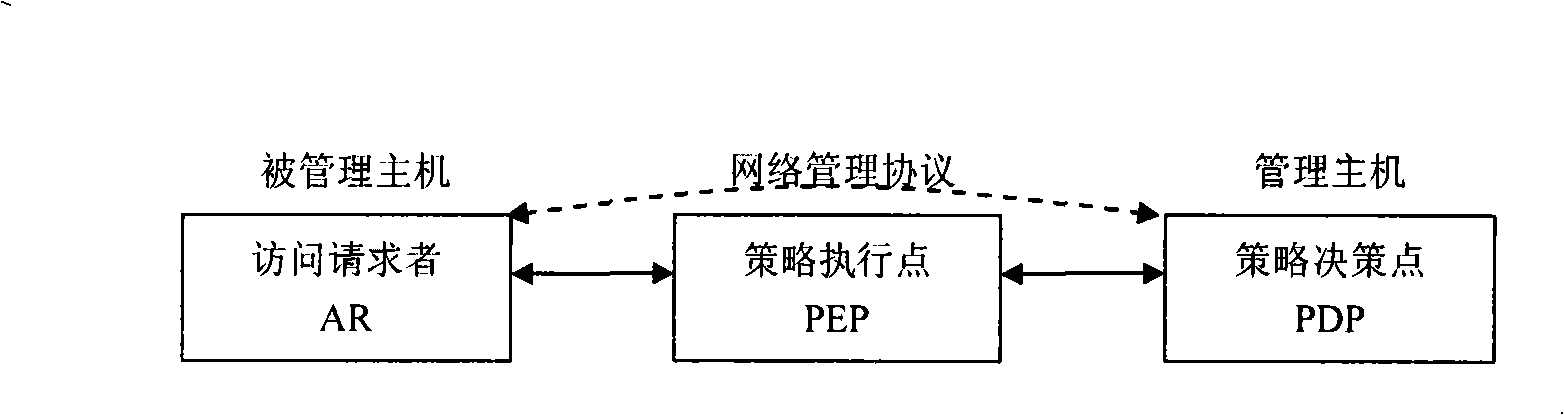
[0049] see image 3 The specific implementation steps of the trusted network management method based on TCPA / TCG trusted network connection in Embodiment 1 of the present invention are:
[0050] 1. Installation and configuration of trusted management agent and trusted management system
[0051] Install and configure the trusted management agent residing in the managed host, install and configure the trusted management system residing in the management host, and the policy decision point PDP acts as the management host. The installation and configuration of the trusted management system is done by the network administrator. The installation and configuration of trusted management agents can be done by network administrators or by network users. When the installation and configuration of the trusted management agent is completed by the network user, the configuration file must be distributed by the network administrator and the content of the configuration file is unknown to t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com