Method for combining encryption to lower computer based on schoolyard card entrance guard system
A technology of access control system and lower computer, which is applied in the direction of instruments, single input/output registers, time registers, etc., can solve the problems that products are easy to be copied by others, endanger the intellectual property rights of original creators and design enthusiasm, etc., to achieve The effect of protecting independent intellectual property rights, simple and effective independent intellectual property rights, and strong anti-cracking ability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
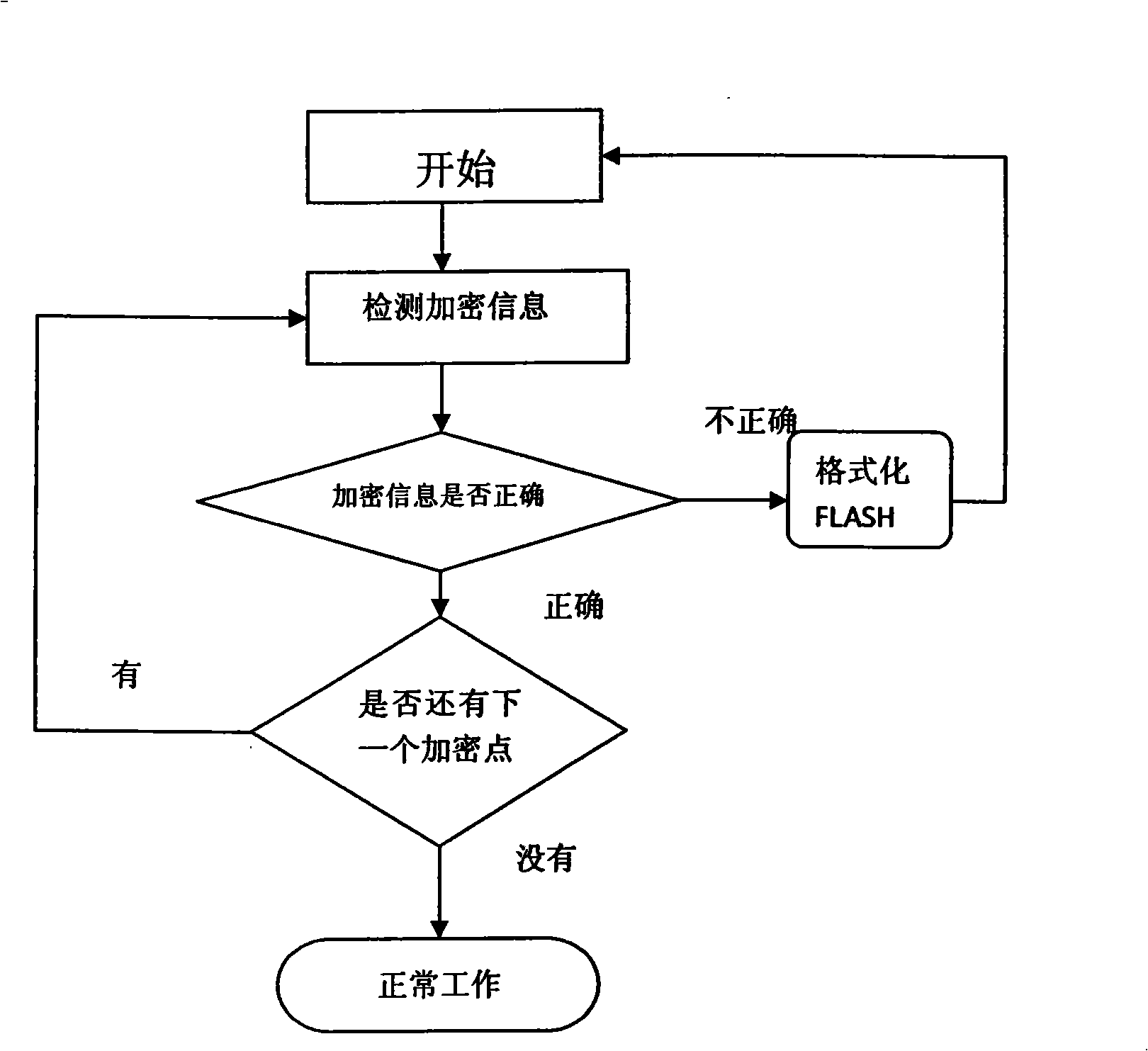
[0040] First determine to set up 3 encryption points, each encryption point location is provided by the previous encryption point, the first encryption point location is address 1, and the number of people who open the door is 4, then each encryption point performs a layer of encryption. The house number controlled by the lower computer is 1356, and the encryption point is a 16-bit sequence of 6 and 0. After all these are determined, the upper computer sends encrypted information according to this regulation during work, so that the lower computer can work normally after detecting the encrypted information.
example 2
[0042] First determine that this is an encryption point, and the location of this encryption point is dynamic. The house number of the door controlled by this lower computer is 1234, then The result is address 98. If the number of people who open the door is 9, each encryption point will be encrypted with three layers. The year of opening the door for the first person to issue the card is 2008, and the encryption number at this encryption point is a 16-bit number alternating between 4 and 8. After all these are determined, the upper computer sends encrypted information according to this regulation during work, so that the lower computer can work normally after detecting the encrypted information.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com