Confidential file protection method
A confidential file and computer technology, applied in memory systems, computer security devices, instruments, etc., can solve problems such as tampering and performance deterioration, reduce the possibility of tampering, suppress performance deterioration, and prevent improper access behaviors Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0044] Hereinafter, an embodiment of the present invention will be specifically described with reference to the drawings.
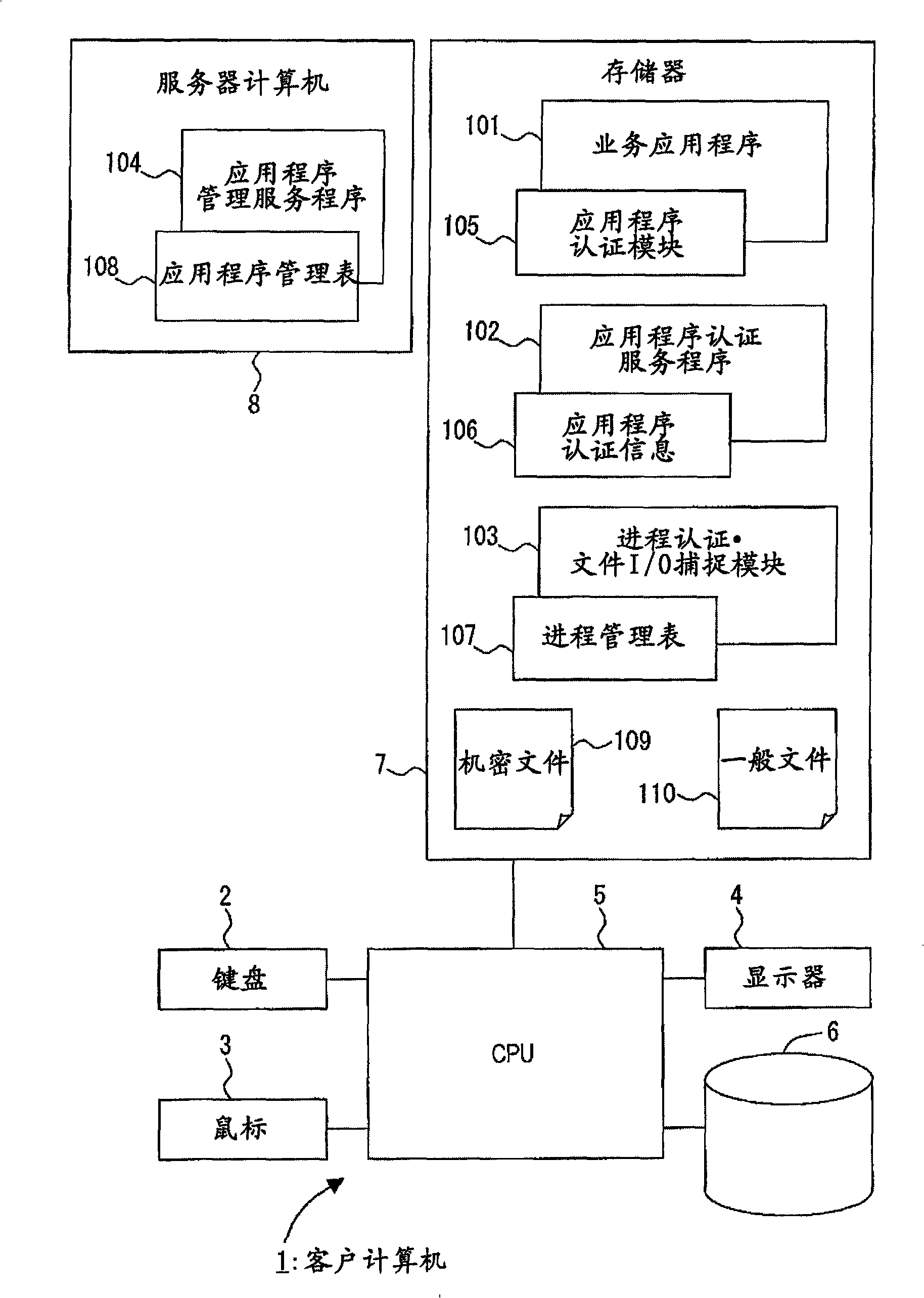
[0045] figure 1 It is a functional block diagram showing an embodiment of a system (secret document protection system) to which the present invention is applied.
[0046] A client computer (secret file protection device) 1 includes a keyboard 2, a mouse 3, a display 4, a CPU 5, an external storage device 6, and a memory 7, and the memory 7 stores business application programs 101 for various tasks.
[0047] Furthermore, a process authentication / file I / O capture module 103 for protecting a confidential file 109 is stored.
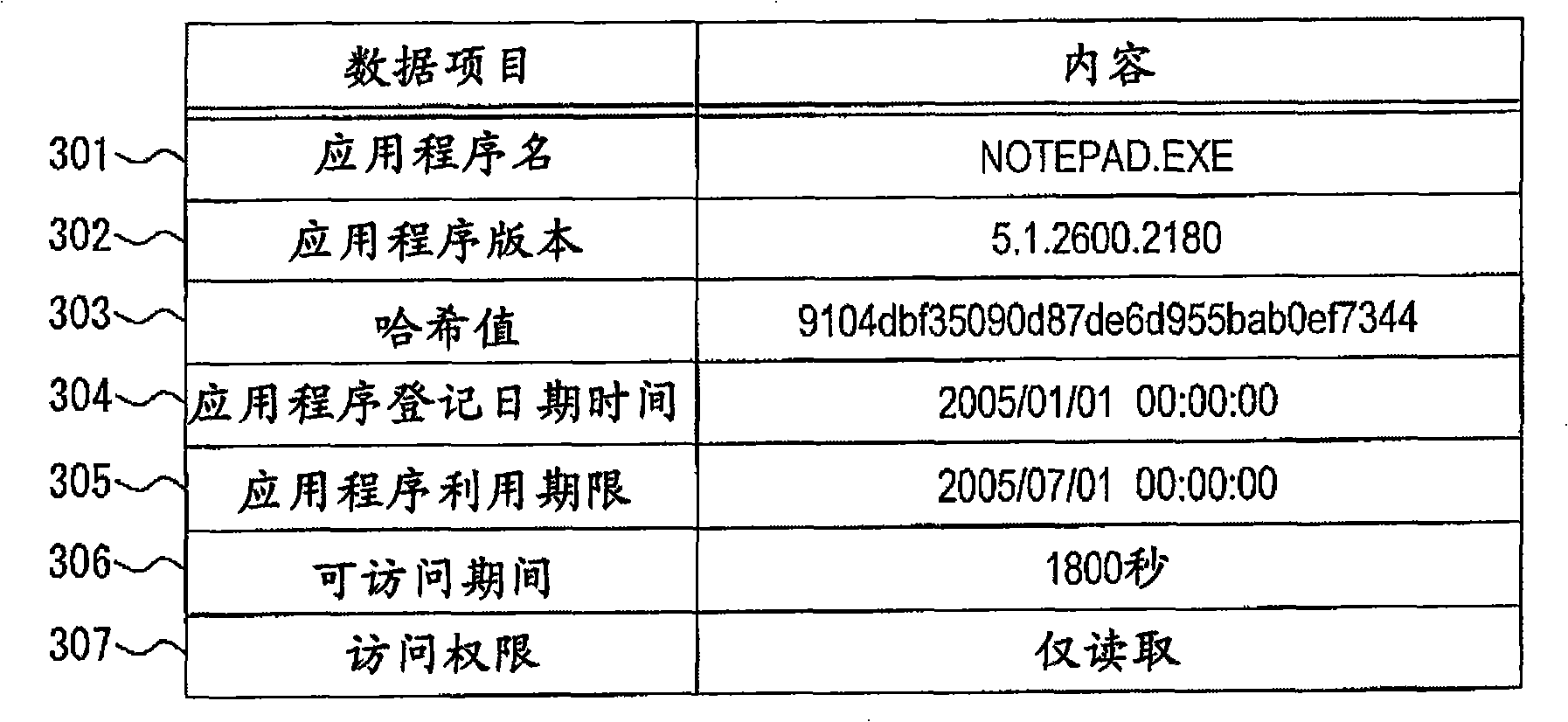
[0048] The process authentication·file I / O capture module 103 has a process management table 107, captures the registration of the process and the file I / O command, and performs process authentication according to the management information registered in the process management table 107, for the process from which the authentication is...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com