Network flow and delaminated knowledge library based dynamic file clustering method
A technology of text clustering and network flow, applied in the fields of information processing and network content security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
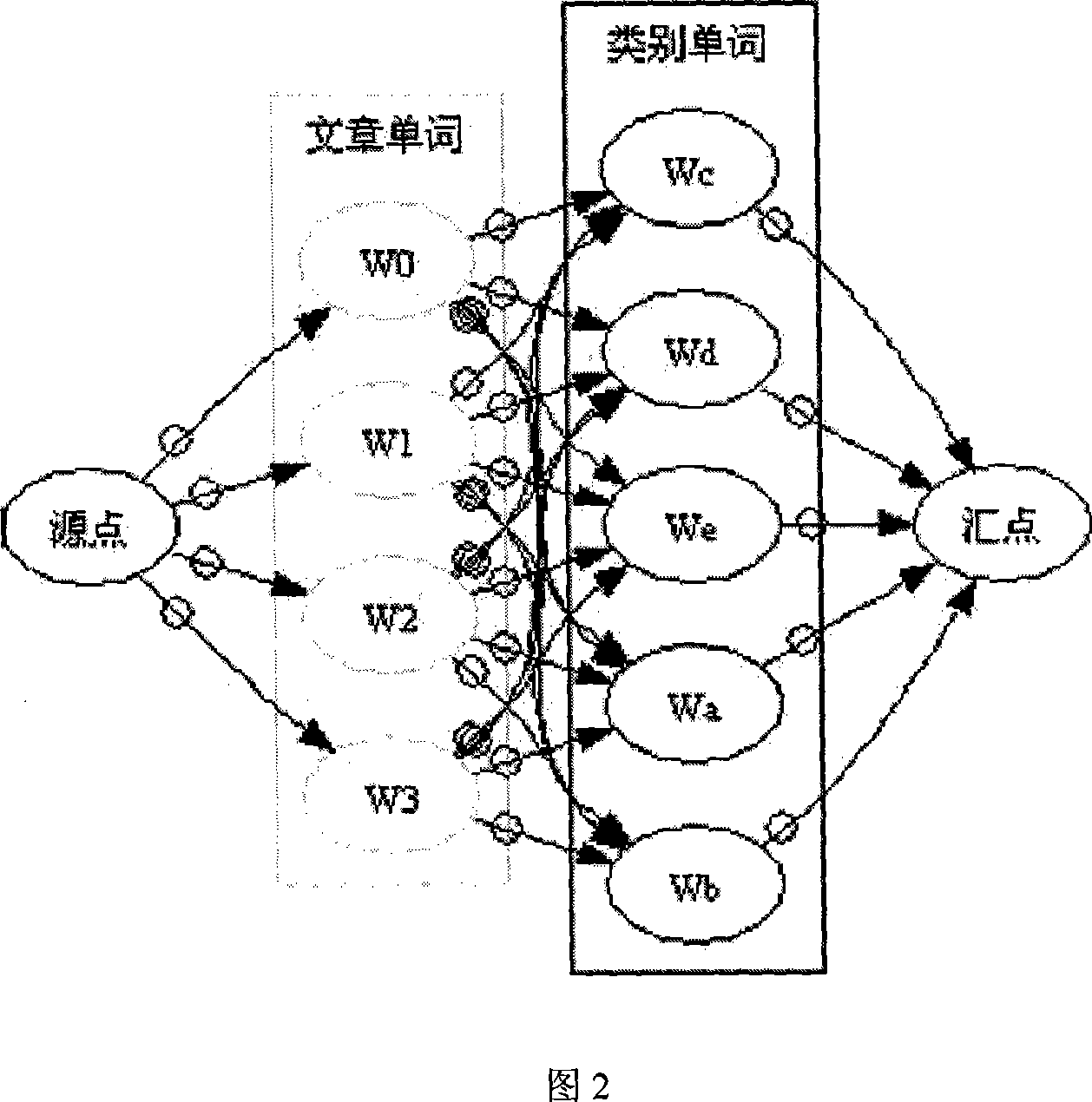
[0075] The method of the present invention is further described below by way of example.
[0076] In this example, the number of documents to be processed is N=3, the similarity threshold θ=0.5, and the vector dimension of the document category Lc=4, where the text vectors are D1, D2, and D3 respectively, and each word in the vector is followed by The weight information calculated by the article through TF·IDF:
[0077] D1 = {(computer, 0.4), (game, 0.3), (download, 0.3)}
[0078] D2 = {(latest, 0.2), (software, 0.5), (download, 0.3)}
[0079] D3={(Computer, 0.4), (Game, 0.3), (Strategy, 0.3)}
[0080] Then when clustering starts, D1 is processed first, because there is no other category to compare with, so it establishes itself as a new category, which is C1, where C1={(computer, 0.4), (game, 0.3), (download, 0.3)}.
[0081] Then process D2, compare D2 with class C1, build the network flow graph, and only have non-zero edge costs from "(download, 0.3)" in D2 to "(download...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com