Equipment supervision method and system based on identity verification
An identity verification and supervision system technology, applied in the field of equipment supervision based on identity verification, can solve problems such as high cost, property loss, and loopholes in supervision, and achieve the effect of ensuring legal compliance.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
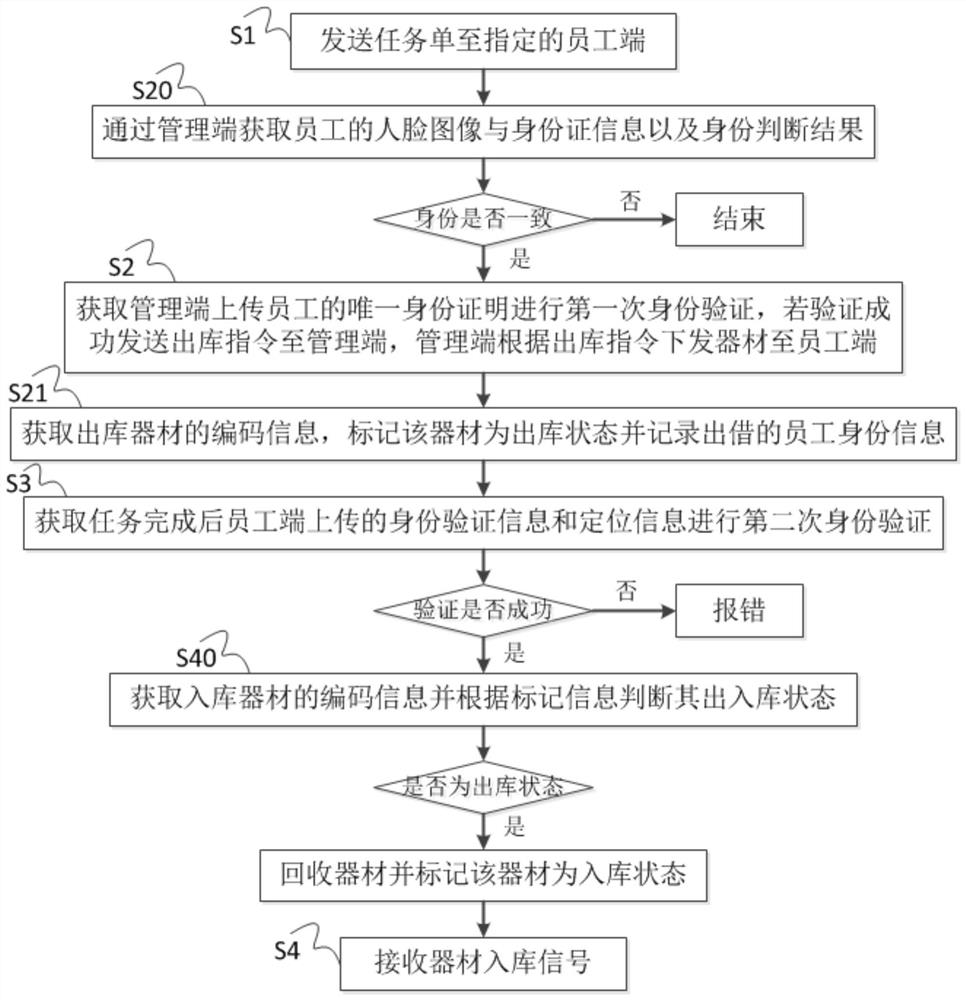
[0034] In order to better rectify the irregular operation of existing high-value equipment when going out to work, and avoid equipment damage caused by private borrowing and borrowing, such as figure 1 As shown, the present invention proposes a method for equipment supervision based on identity verification, including steps:
[0035] S1: Send a task order to the designated employee terminal, the task order includes task information, task location information, and employee identity information bound to the designated employee terminal;
[0036] S2: Obtain the unique identity certificate uploaded by the management terminal for the first identity verification. If the verification is successful, send the warehouse-out instruction to the management terminal, and the management terminal will send the equipment to the employee terminal according to the warehouse-out instruction;
[0037] S3: After the completion of the acquisition task, the identity verification information and locat...
Embodiment 2
[0051]In order to better explain the technical content of the present invention, this embodiment illustrates the present invention in the form of a system structure, a device supervision system based on identity verification, including:
[0052] The server is configured to generate a task order and send it to a designated employee terminal, where the task order includes task information, task location information, and employee identity information bound to the designated employee terminal;
[0053] The management terminal is used to upload the employee's unique identity certificate to the server for the first identity verification, and send the equipment to the employee's end when the verification is successful and the outbound order is obtained;
[0054] The employee side is used to upload the identity verification information and location information to the server for the second identity verification after the task is completed, and return the equipment.
[0055] Further, th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com