Design method of collaborative unmanned aerial vehicle data acquisition system based on physical layer security
A technology of data acquisition system and physical layer security, which is used in wireless communication, power management, interference to communication, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0077] Firstly, an implementation mode is given when there is only one node on the ground, that is, K=1. Since there is only one node, the scheduling variable does not need to be optimized, which is similar to military information transmission. Assuming that the starting position and the ending position of the receiver and the jammer are different, within a mission period, only one-way flight is enough. Specific steps are as follows:
[0078] Assume the emitter's position is w k =[800,600] T ; The center of the eavesdropper's estimated position is w e =[400,600] T ;Radius of the eavesdropper's estimated position circle r e =20m. The starting position and ending position of the drone Bob are [100,100] respectively T and [1100,100] T ; The start position and end position of the UAV Jack are [100,1000] respectively T and [1100,1000] T . Some fixed parameters are set as follows: σ 2 =-110dBm, d 0 = 1m, ρ 0 =-60dB, B w =1MHz, α=3, H=150m, V max =50m / s, a max =3m / s ...
Embodiment 2
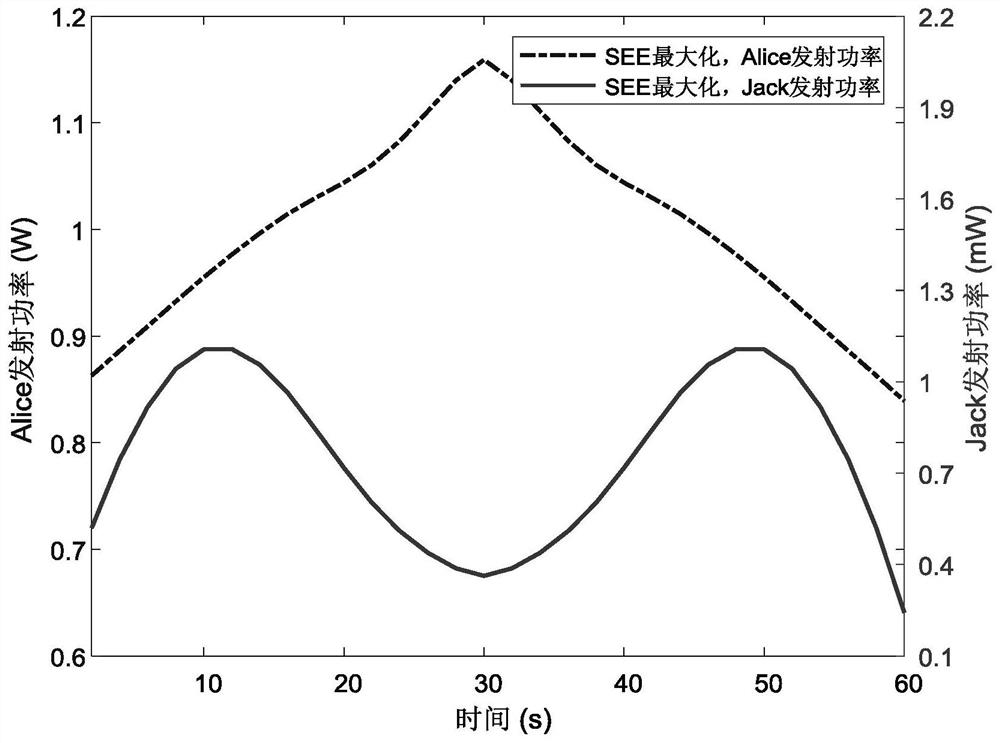
[0082] Considering the actual situation, the UAV may need to collect information of multiple nodes on the ground. In this example, K=3. Assuming that the starting position and ending position of the receiver and the jammer are the same, the trajectory of the UAV becomes a closed loop, and all users can be visited sequentially. where w k =[1000,1000; 200,600; 900,150] T ;w e =[500,500] T . This section mainly compares the performance of the following five schemes, scheme 1: maximizing safe energy efficiency. Scheme 2: Maximize the average security rate. Scheme 3: Maximize the average safe speed with propulsion power limitation.
[0083] Figure 4 The optimization trajectories of different T maximizing safe energy efficiency schemes are given in . When T=100s, due to the limitation of the flight cycle, the UAV can only fly in a small circle area. In contrast, when T is 180s, Bob is more inclined to be close to the ground node and far away from the eavesdropper, so as to...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com