Implementation method of general access policy in cloud storage
A technology of access policy and implementation method, applied in the direction of instruments, digital transmission systems, security communication devices, etc., to achieve the effect of perfect security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0087] The specific implementation of the present invention will be described in detail below in conjunction with the accompanying drawings.
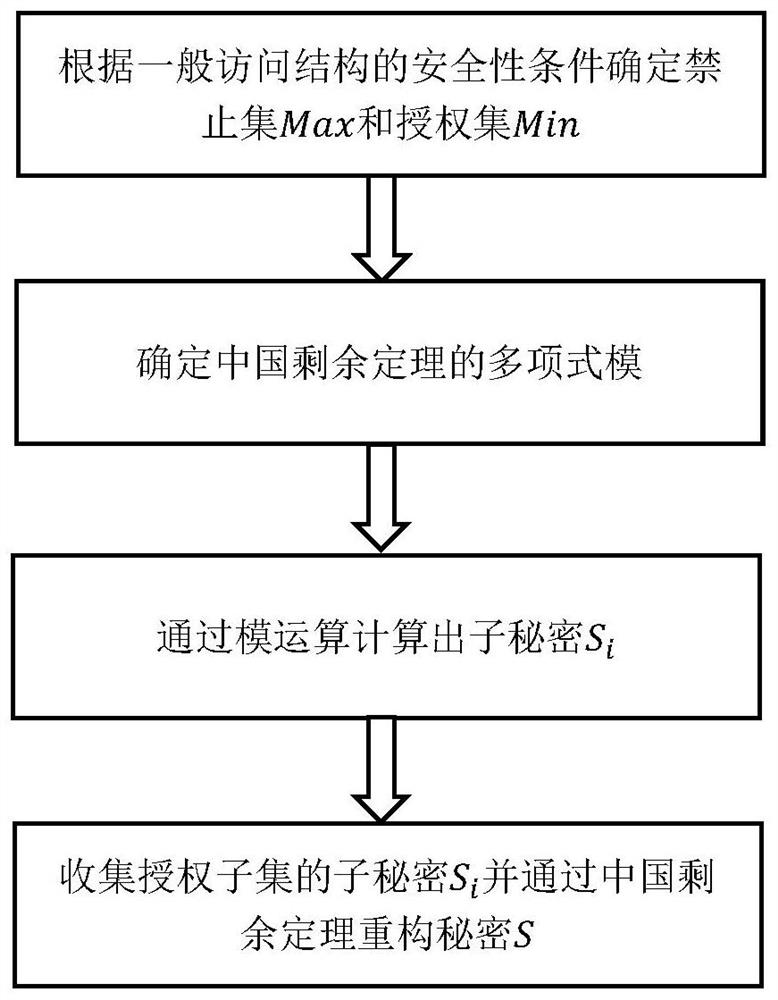
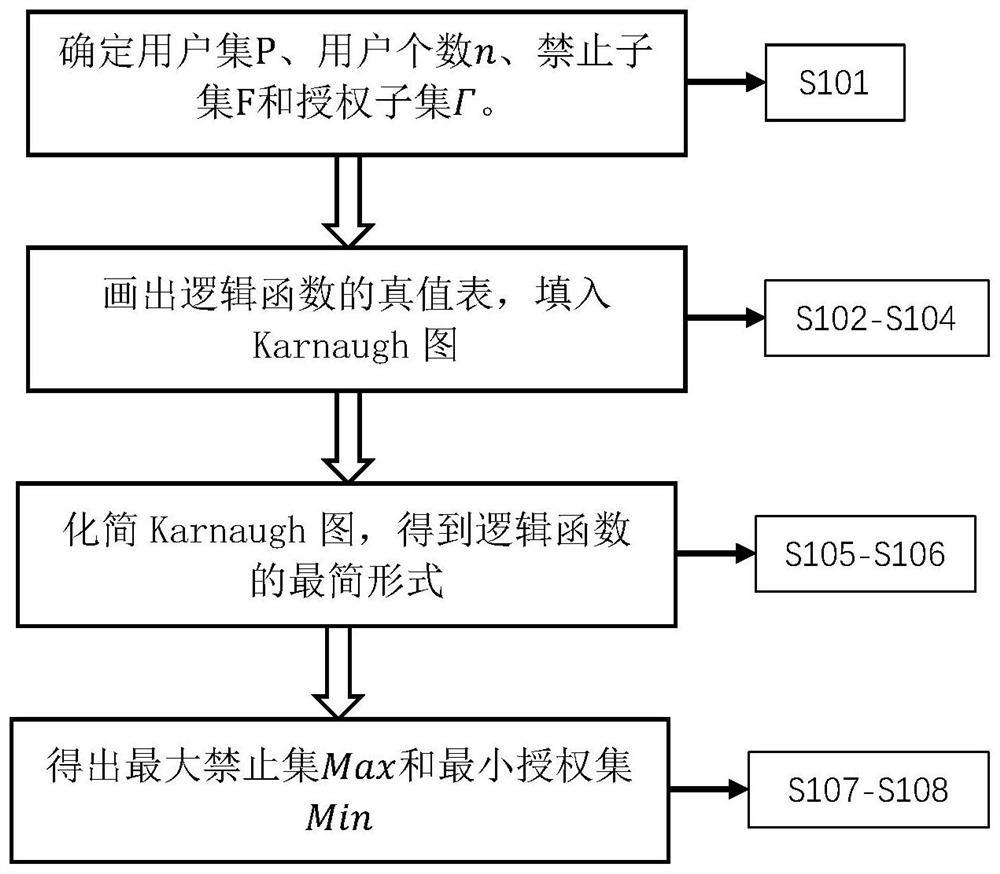
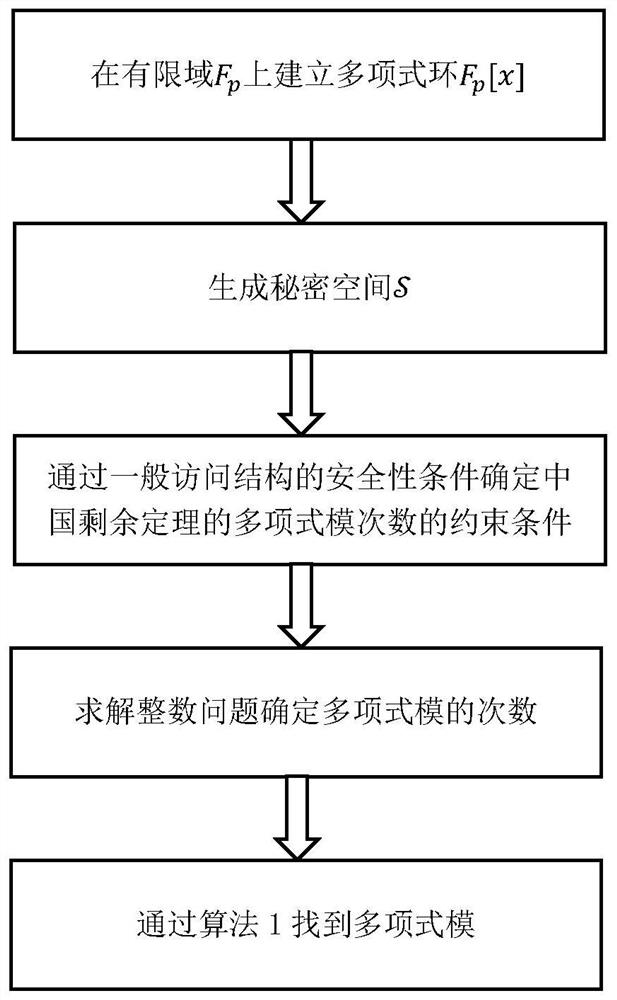
[0088] The implementation example of the present invention provides a general access structure using the Chinese remainder theorem on polynomial rings. In order to construct a general access structure, it is first necessary to use the policies of the general access structure to determine the maximum forbidden set and the minimum authorized set, and then to assign user weights, secondly to use the Chinese remainder theorem on the polynomial ring to carry out secret sharing, and finally the secret refactoring phase.
[0089] The following section first introduces the determination of the maximum forbidden set and the minimum authorized set, then introduces how to determine the modulus of the Chinese remainder theorem, then introduces how to perform secret sharing, and finally introduces the reconstruction of the secret.
[0090] 1. Deter...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com