Smart home protection system and protection method thereof
A protection system and smart home technology, applied in transmission systems, digital transmission systems, home automation networks, etc., can solve problems such as poor security, and achieve the effect of solving poor security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
[0050] The above is the first embodiment of the smart home protection system provided by the embodiment of the present application, and the following is the second embodiment of the smart home protection system provided by the embodiment of the present application.
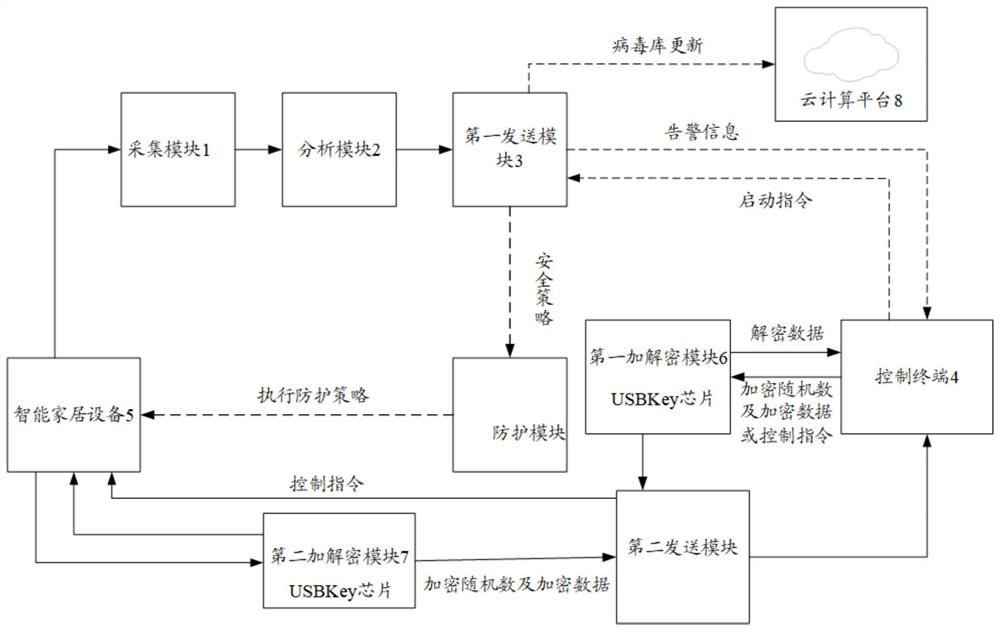
[0051] see figure 1 , a schematic structural diagram of the first embodiment of a smart home protection system in the embodiment of the present application.
[0052] In this embodiment, the smart home protection system includes: an acquisition module 1, an analysis module 2, a first sending module 3 and a control terminal 4; the acquisition module 1 is connected to the smart home device 5, and is used to collect device data from the smart home device 5; The analysis module 2 is used to perform security analysis on the device data to obtain a security analysis result; the first sending module 3 is used to send an alarm message to the control terminal 4 when the security analysis result shows that the smart home devic...
no. 2 example
[0077] The above is the second embodiment of a smart home protection system provided by the embodiment of the present application, and the following is an embodiment of a smart home protection method provided by the embodiment of the present application.
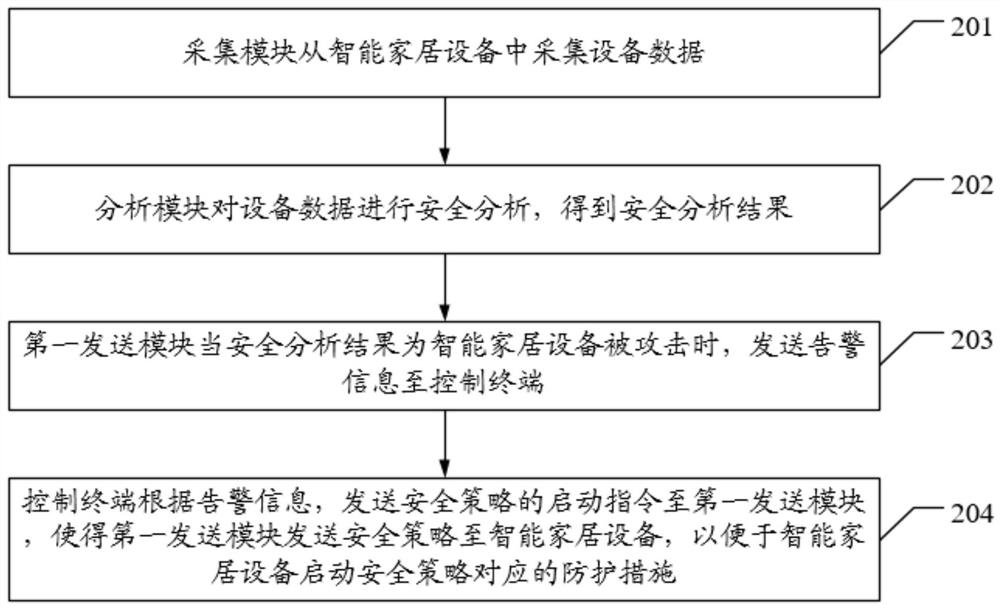
[0078] see figure 2 , a schematic flowchart of an embodiment of a smart home protection method in the embodiment of the present application.
[0079] A smart home protection method in this embodiment includes:
[0080] Step 201, the collection module collects device data from smart home devices.
[0081] Step 202, the analysis module performs security analysis on the device data to obtain a security analysis result.
[0082] Step 203, the first sending module sends an alarm message to the control terminal when the result of the security analysis is that the smart home device is attacked.
[0083] Step 204 , the control terminal sends a security policy start command to the first sending module according to the alarm infor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com