Attack traffic shunting and blocking method based on topology analysis
A technology of attack traffic and topology analysis, applied in digital transmission systems, data exchange networks, electrical components, etc., can solve problems such as low blocking efficiency of countermeasure mechanisms and network congestion
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
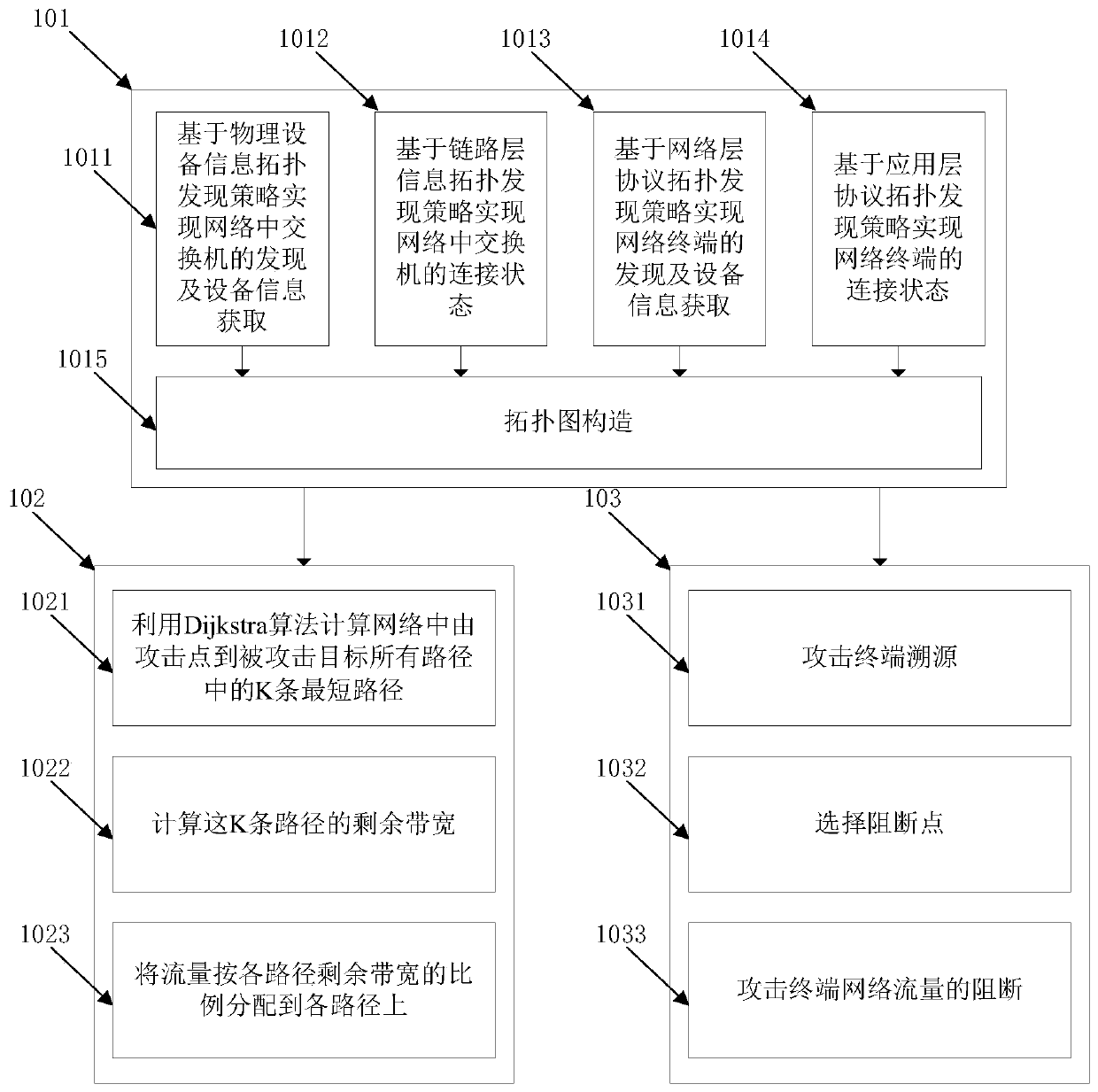
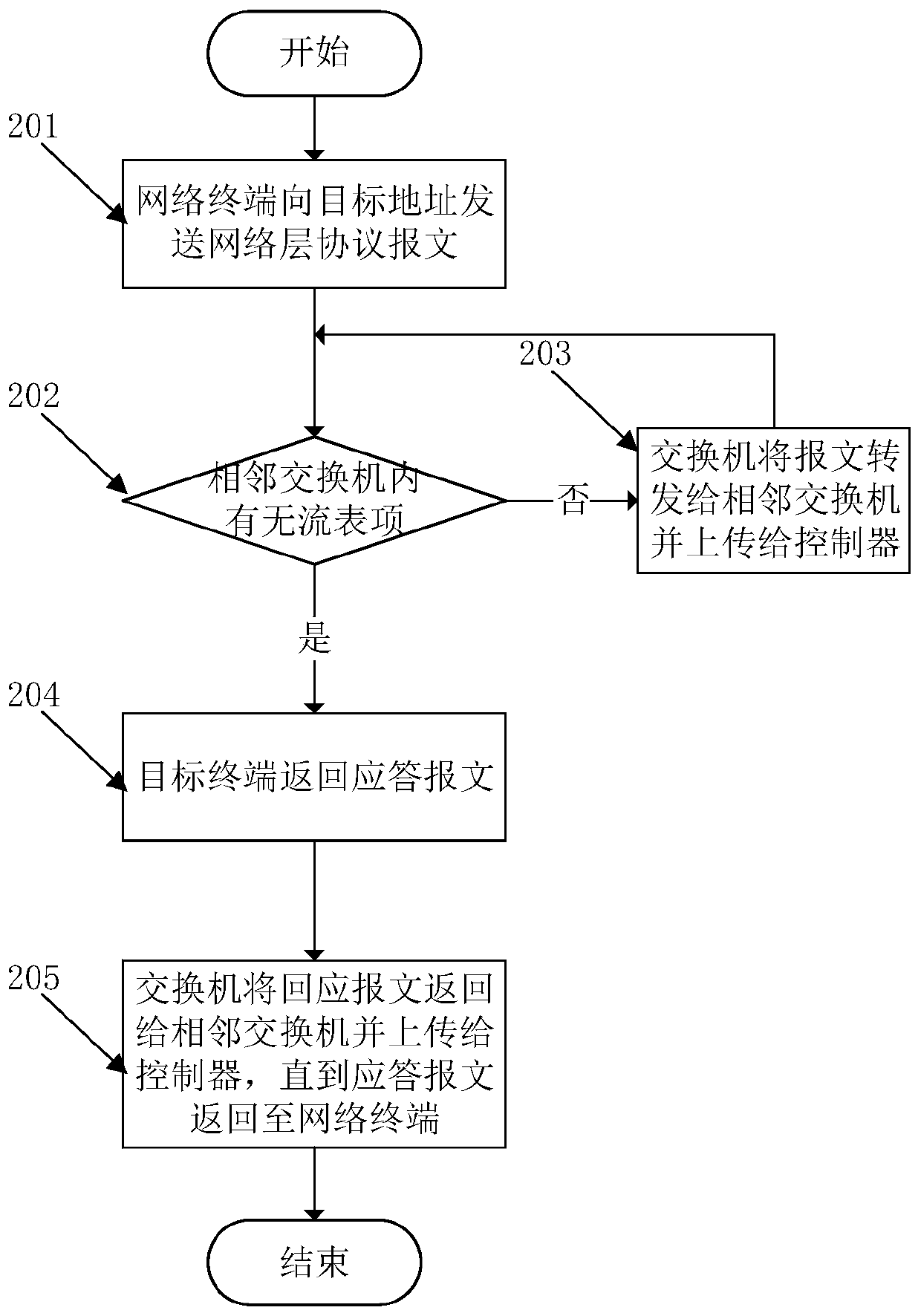
[0115] figure 1 Shown is a flow chart of the method for diverting and blocking attack traffic based on topology analysis in the present invention.
[0116] Such as figure 1 Shown: This embodiment adopts the network architecture of software-defined network, including controllers and switches. The controller is built with Ryu and supports the OpenFlow protocol; the switch is built with Open vSwitch, and interacts with the controller through the OpenFlow protocol. The controller is responsible for forwarding and controlling the message data of the entire network, and the switch forwards the message data according to the forwarding rules issued by the controller. The controller transmits forwarding rules to the switch through the flow entry of the OpenFlow protocol, and manages and controls the switch through the simple network management protocol. The method proposed in this patent first obtains the network topology through multiple discovery strategies. When a traffic-based n...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com