Access control authority management system and method
A technology of rights management and access control, applied in the field of access control rights management system, which can solve problems such as security accidents and irregular operations
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
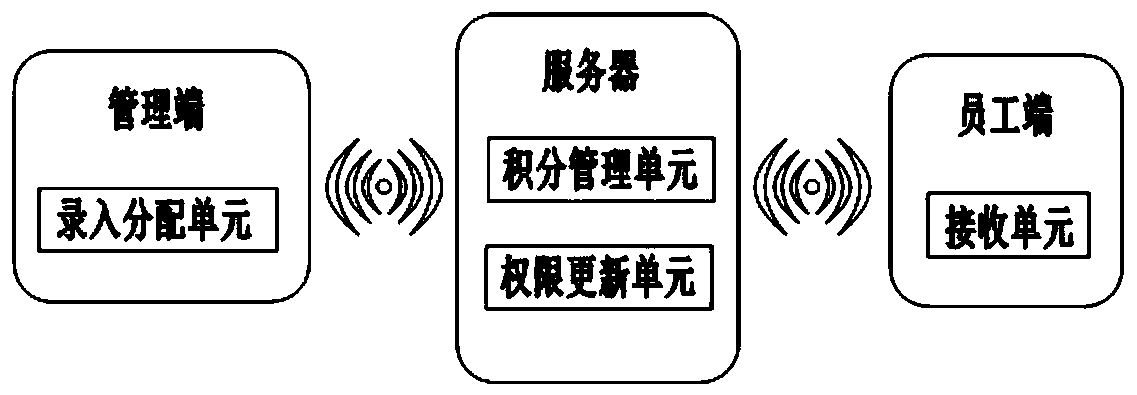
[0044] Such as figure 1 As shown, an access control authority management system includes an entry distribution unit, a point management unit, an authority update unit, and a receiving unit. Among them, the entry and distribution unit is integrated on the management side, the point management unit and authority update unit are integrated on the server, and the receiving unit is integrated on the employee side.
[0045] In this embodiment, the management terminal is a smartphone loaded with relevant APPs, the server is a Tencent Cloud server, and the employee terminal is a smartphone loaded with relevant APPs. The management end and the employee end communicate with the server through the 5G module respectively.
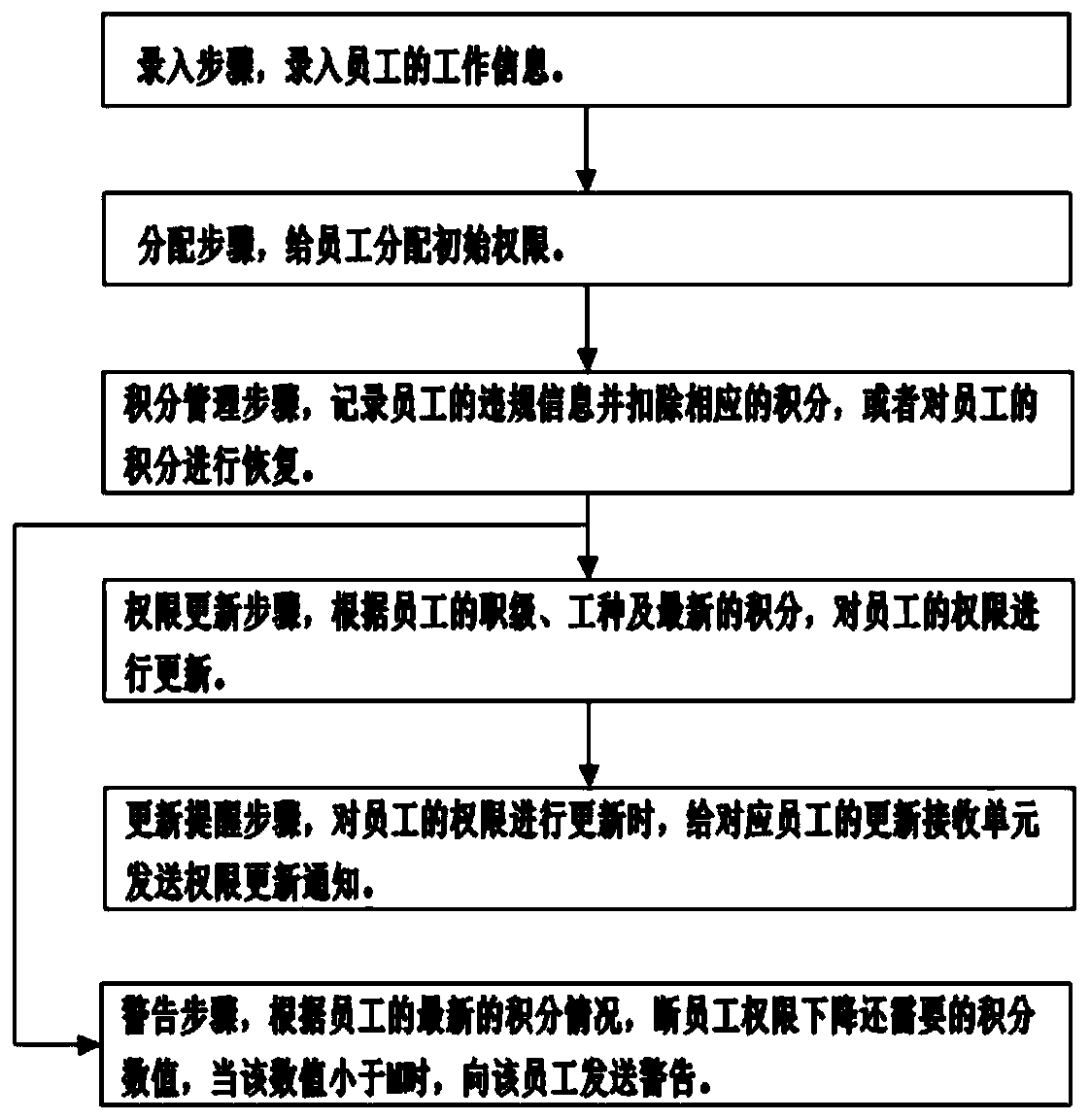
[0046] The entry assignment unit is used to enter the employee's work information, specifically, the job information includes name, rank, type of work, age and contact information; the entry assignment unit is also used to assign initial permissions to the employee. ...
Embodiment 2
[0066] Compared with Embodiment 1, this embodiment is different in that this embodiment also includes a collection terminal for collecting images and voices of the construction site, and sending the collected data to the server. The server also includes a storage unit and a fight analysis unit.
[0067] The storage unit stores the facial information and phone numbers of the workers, and also stores the interpersonal relationship between workers on the same construction site. The acquisition end is a camera and a pickup.
[0068] The fight analysis unit is used to analyze the data sent by the acquisition end by means of image recognition and semantic recognition. When the analysis result shows that there is a risk of two people fighting, after the facial information of the two people is recognized, the facial information of the two people is matched. phone, and send preset call messages to two people respectively. One of the message content is that the foreman calls to site A,...
Embodiment 3
[0076] Different from Embodiment 1, in this embodiment, it also includes intelligent access control. The opening methods of the access control include face recognition, IC card identification and ID card identification. The intelligent access control is integrated with an ID card acquisition unit, a face acquisition unit and IC card acquisition unit.
[0077] It also includes a second collection terminal, which is used to collect the image information of the entrance and exit. The second collection end is a camera.
[0078] The server also includes an analysis unit, which is used to acquire image information from the second acquisition terminal, and identify users entering and exiting the gate based on the image information. The analysis unit is used to close the ID card collection unit, the face collection unit and the IC card collection unit when the user is not recognized. When the analysis unit recognizes the user, it is also used to predict the identity verification met...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com