Security analysis method for mimicry defense architecture
An analysis method and security technology, applied in the direction of digital transmission system, data exchange network, electrical components, etc., can solve the problems of lack of security of mimic defense, lack of security of mimic defense model, etc., and achieve reliable analysis results
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
[0096] combine figure 1 , the present invention is oriented to the security analysis method of mimic defense framework, comprises the following steps:
[0097] Step 1. Define four variables in the security analysis model: the dynamic change cycle of the executive body, the time required for the successful implementation of the attack, the probability of the execution body showing a difference after being attacked, and the probability of the attacker successfully transferring the attack, as follows:
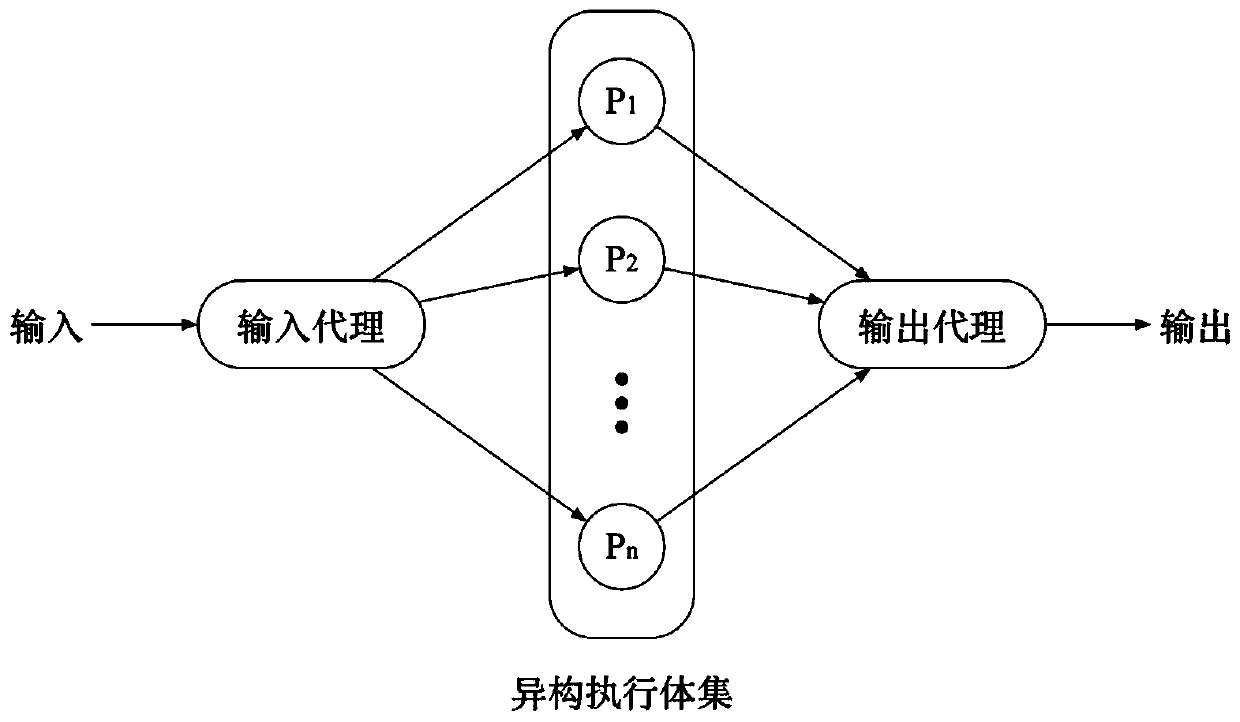
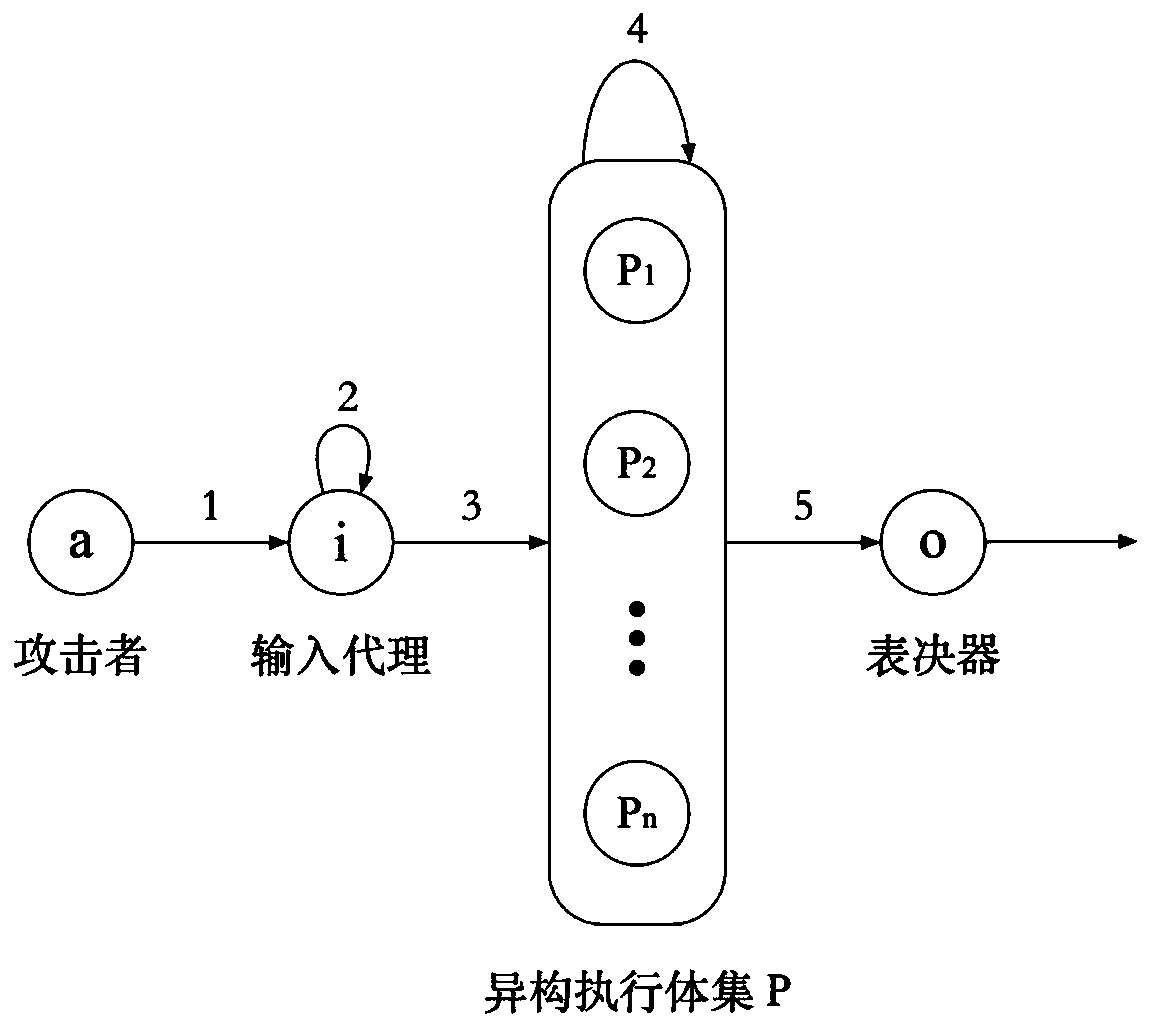
[0098] The main structure of mimic defense is the Input-Processing-Output (IPO) model, such as figure 2 shown. From figure 2 It can be seen that the security of mimic defense is related to the following aspects:
[0099] (1) The professional level and technical means of the attacker determine whether the input in the model is aggressive;
[0100] (2) Input agent, which determines whether the attacker’s input information can be normally distributed to heterogeneous executive ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com