Cluster access method and related product
An access method and cluster technology, applied in the cluster field, can solve problems such as cluster access failure and Hadoop cluster cluster configuration changes, and achieve the effect of avoiding access failure and improving the probability of successful cluster access.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0068] The technical solution in this application will be described below with reference to the accompanying drawings.
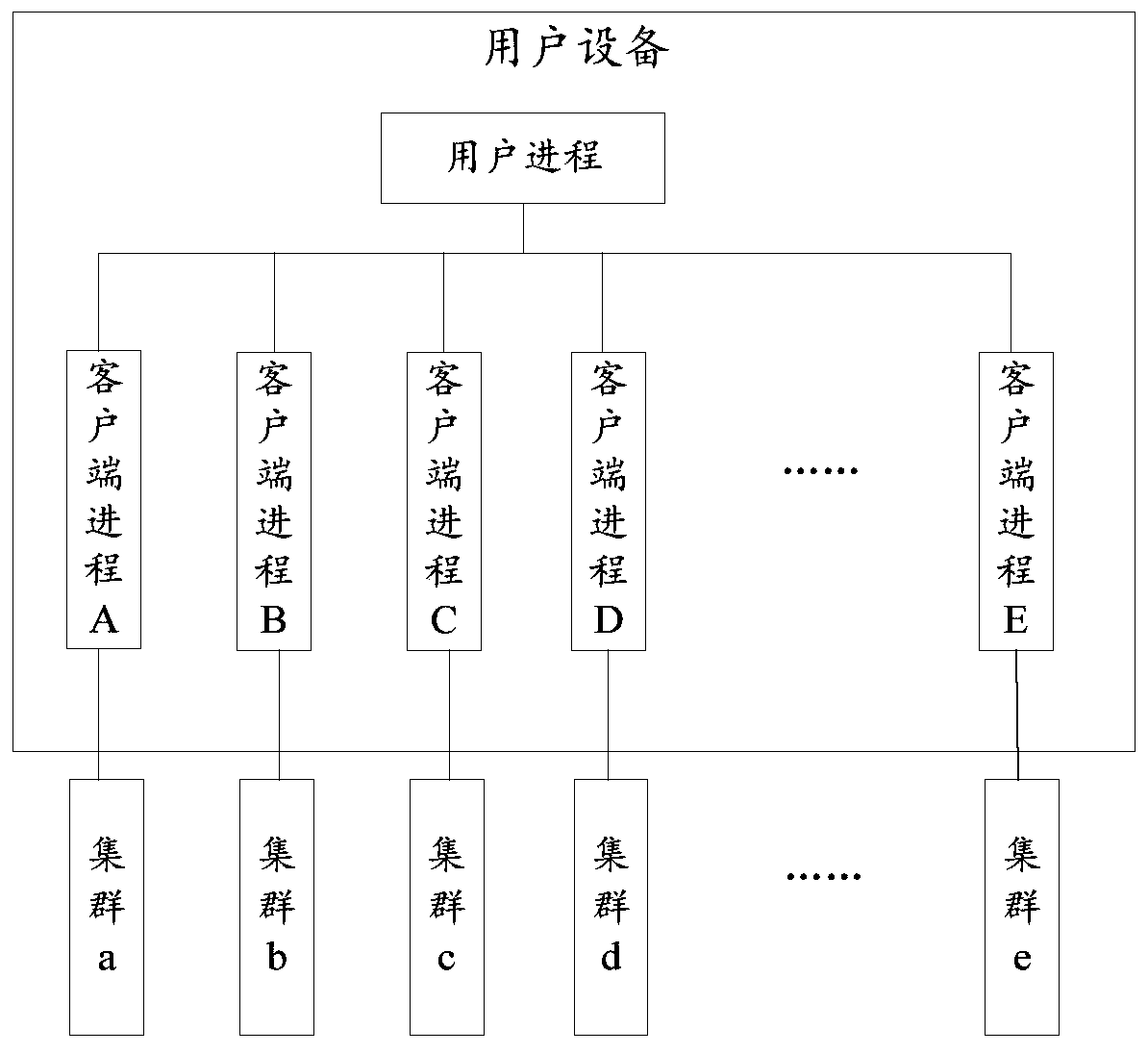
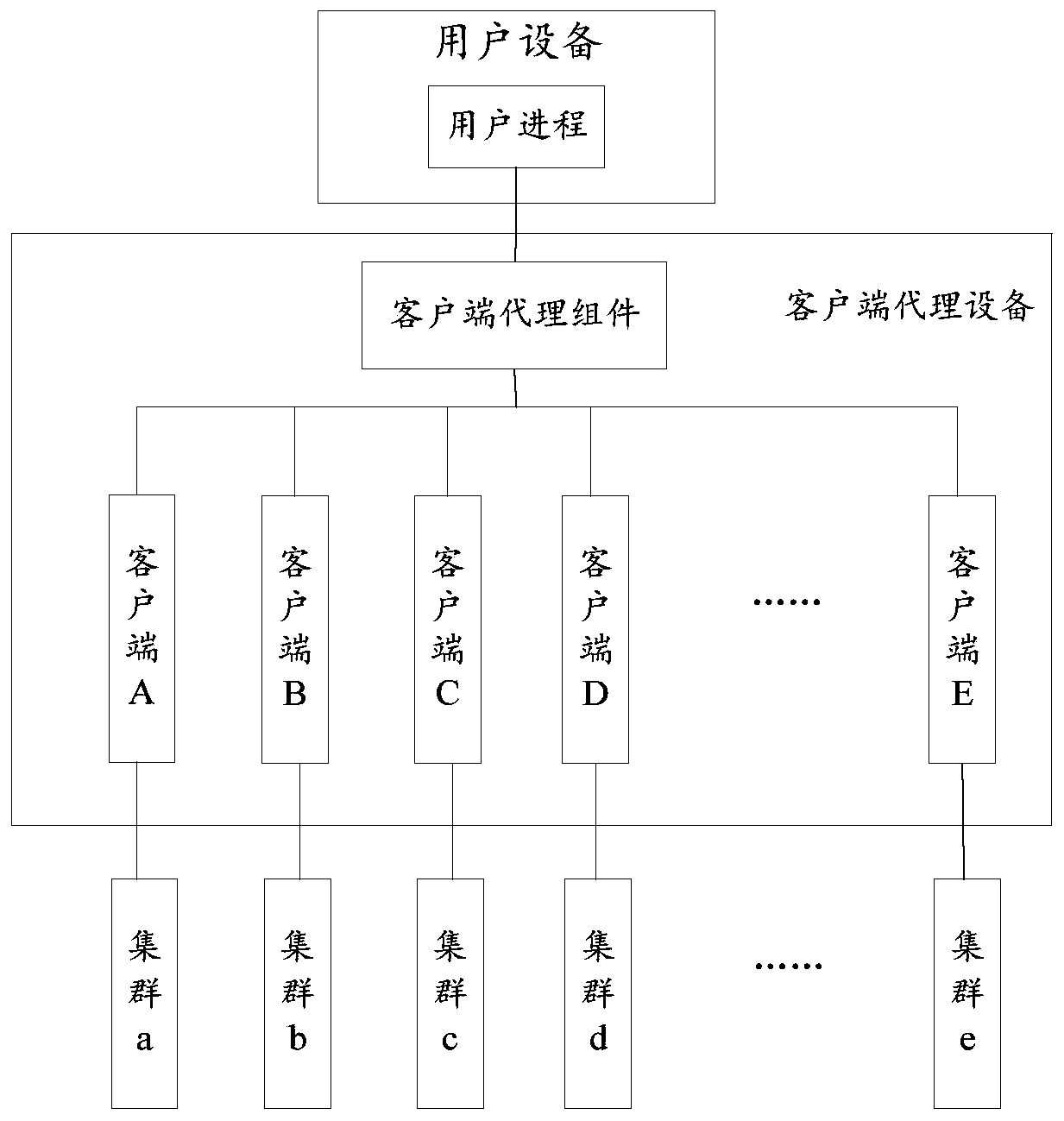
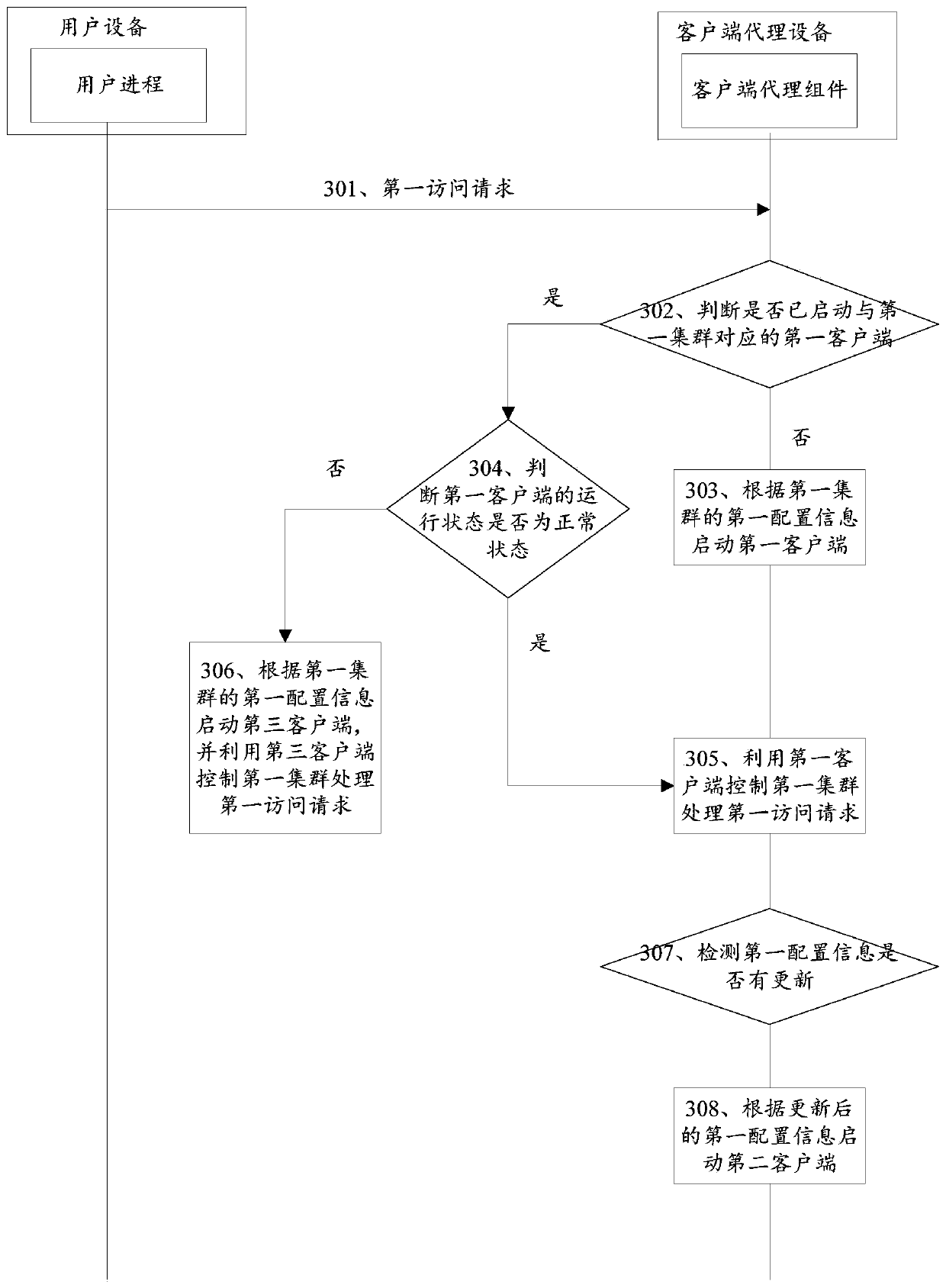
[0069] A cluster is a group of computers that are independent of each other and interconnected through a high-speed network. They form a group and are managed in a single system mode; each computer in the cluster can be used as a node in the cluster. Usually, the user equipment can access the corresponding cluster through the client, and the client is used to connect with the cluster. The client receives the user's access request, finds the cluster corresponding to the access request, and uses the nodes in the cluster to execute the access request.
[0070] Since the client versions corresponding to each cluster are different, and some clients need to store the configuration information of the cluster in the environment variables of the running process of the client, this makes it difficult for a client to be compatible with multiple clusters. That is to sa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com