User data processing method, intelligent terminal, server and storage medium
A technology for user data and processing methods, applied in the computer field, can solve problems such as illegal registration, verification code leakage, account binding, etc., to achieve the effect of improving security and overcoming security defects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
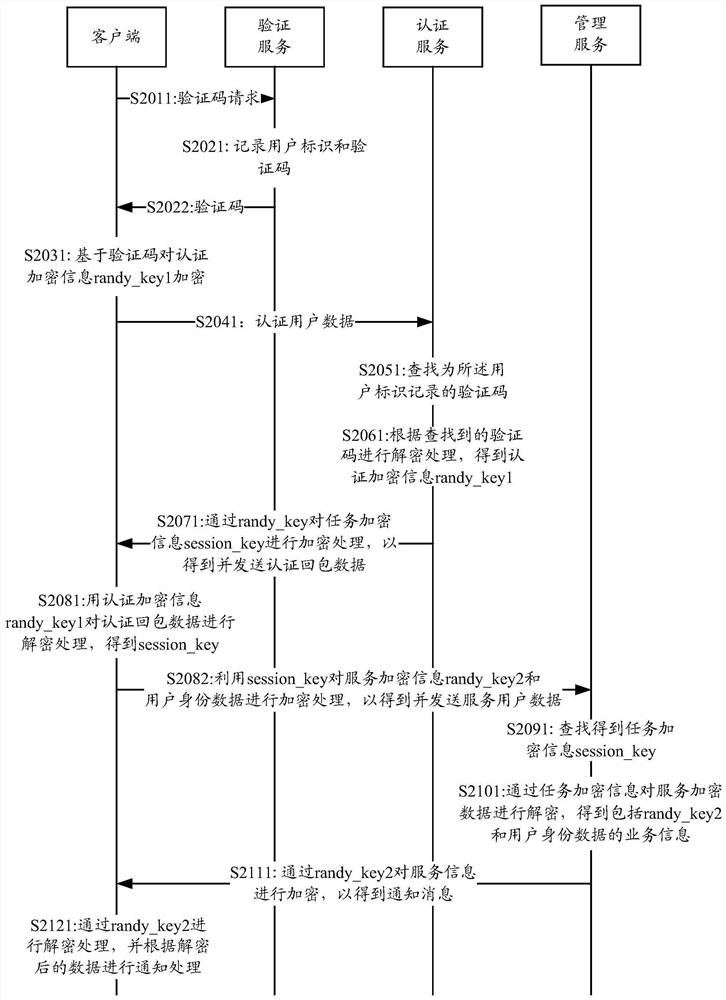
[0054] In application scenarios such as user registration, user account binding, and user data submission, verification processing based on verification codes may be involved. The network-side device that provides verification codes prompts users for verification codes, including SMS verification codes and picture verification. Code, or even voice verification code, etc. After the client receives the corresponding text message or picture or voice data, it can automatically or manually extract characters from the text message, and identify characters from pictures and voice to be verified. After obtaining the verification code, the obtained verification code can be further processed accordingly to ensure the security of the subsequent processing.
[0055] In the embodiment of the present invention, the client can directly use the verification code as the authentication key or the value after processing the verification code as the authentication key (for example, the hash value ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com