A data fusion method and device
A data fusion and data technology, applied in the computer field to prevent leakage, reduce trust costs, and improve efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
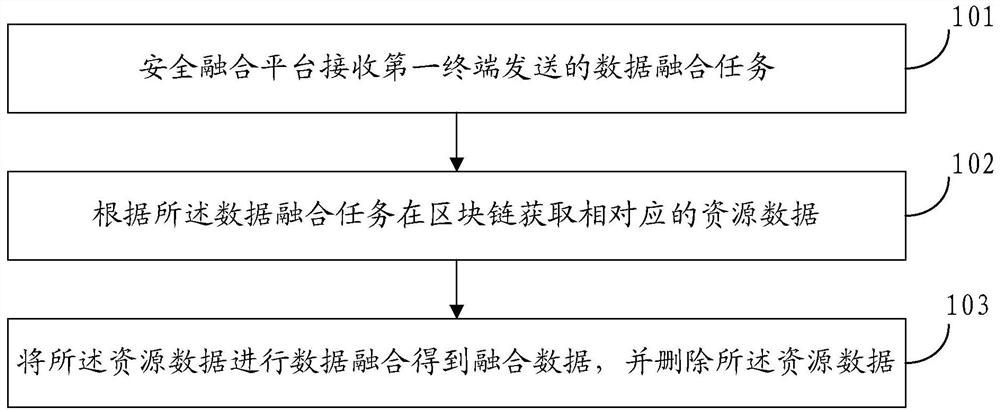
[0061] refer to figure 1 , shows a flow chart of the steps of an embodiment of a data fusion method of the present invention, the method may specifically include the following steps:
[0062] Step 101, the security fusion platform receives a data fusion task sent by a first terminal.
[0063] In the embodiment of the present invention, the data fusion task is configured based on actual needs when the first terminal needs to obtain fusion data, wherein the data fusion task includes a plurality of resource data for query Identification information and fusion configuration information for determining fusion parameters. The security fusion platform is a server dedicated to data fusion set up by technicians in an isolated deployment environment to realize the embodiment of the present invention. The first terminal is a data provider that communicates with the security fusion platform and has data fusion service requirements. The data fusion platform is connected to multiple data ...
Embodiment 2
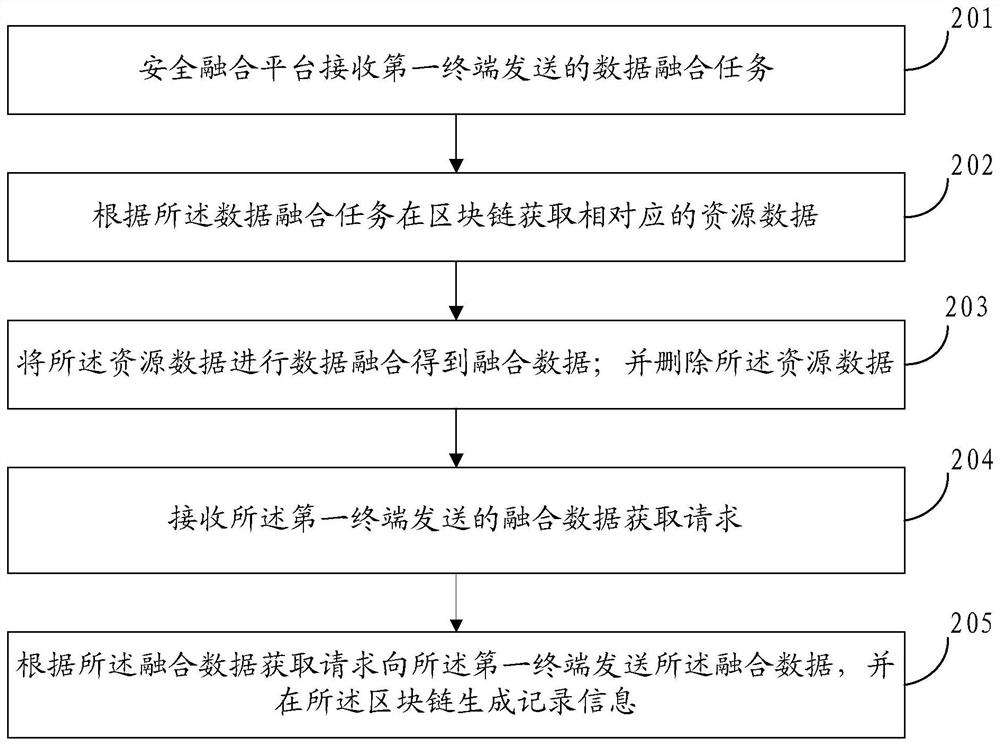
[0071] refer to figure 2 , which shows a flow chart of the steps of another data fusion method embodiment of the present invention, the method may specifically include the following steps:
[0072] In step 201, the security fusion platform receives a data fusion task sent by a first terminal.
[0073] For step 201, refer to step 101, which will not be repeated here.
[0074] Step 202, obtain corresponding resource data in the blockchain according to the data fusion task.
[0075] For step 202, refer to step 102, which will not be repeated here.
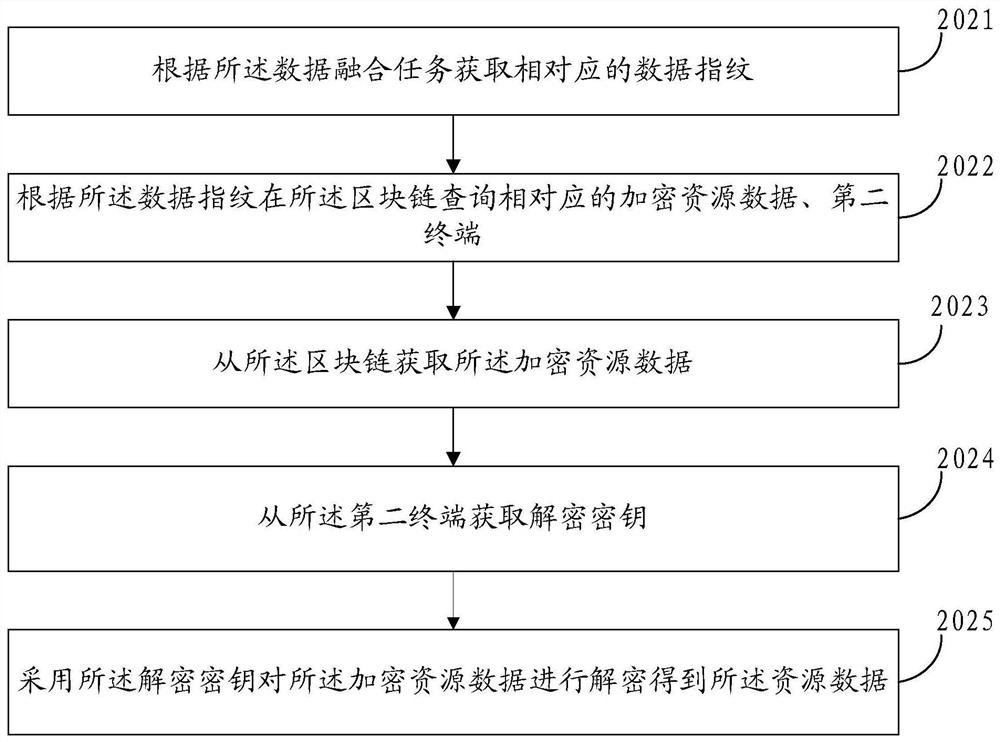
[0076] refer to image 3 , the step 202 may include:
[0077] Step 2021, obtain corresponding data fingerprints according to the data fusion task.
[0078] In the embodiment of the present invention, the data fingerprint is a hash value corresponding to the resource data. The data fusion task includes an identifier of the resource data that needs to be fused, and the corresponding data fingerprint is searched and queried accord...
Embodiment 3
[0107] refer to Figure 6 , which shows a structural block diagram of an embodiment of a data fusion device 30 of the present invention, which may specifically include the following modules:
[0108] The receiving module 301 is used for the security fusion platform to receive the data fusion task sent by the first terminal.
[0109] The acquiring module 302 is configured to acquire corresponding resource data in the blockchain according to the data fusion task.
[0110] The fusion module 303 is configured to perform data fusion on the resource data to obtain fusion data. And delete said resource data.
[0111] An embodiment of the present invention provides a data fusion device, which includes: a receiving module, used for a security fusion platform to receive a data fusion task sent by a first terminal. An acquisition module, configured to acquire corresponding resource data in the blockchain according to the data fusion task. A fusion module, configured to perform data f...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com