CC attack detection method, device and electronic equipment
A detection method and technology of preset times, applied in the direction of error prevention/detection, electrical components, digital transmission system, etc. using the return channel, which can solve the problems of unrecognized or low recognition rate of CC attacks, so as to alleviate the unrecognized CC attacks. Or the effect of low recognition rate, strong real-time detection capability, and fast network abnormality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
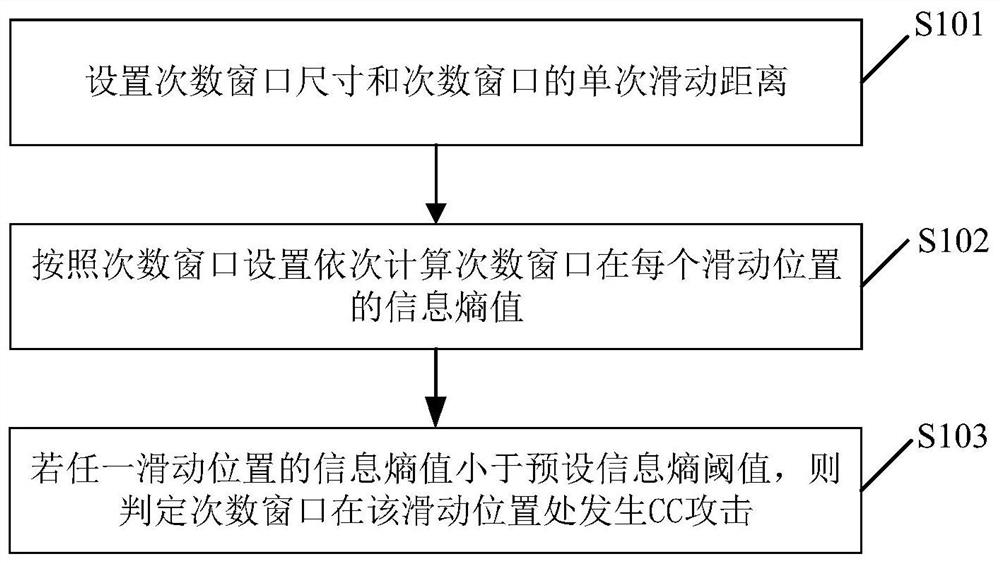
[0066] Such as figure 1 As shown, the embodiment of the present invention provides a CC attack detection method, which is applied in the field of network CC attack detection. The detection methods of this CC attack include:
[0067] Step S101, setting the size of the times window and the single sliding distance of the times window;
[0068] The frequency window here refers to the sliding window defined by the number of requests; that is, the size of the frequency window and the single sliding distance are characterized by the number of requests; the size (or size) of the frequency window is characterized by the window width. Wherein, the size of the times window and the single sliding distance of the times window are called window parameters of the times window.
[0069] Step S102, calculate the information entropy value of the number of times window at each sliding position sequentially according to the number of times window setting;
[0070] Specifically, the information...
Embodiment 2
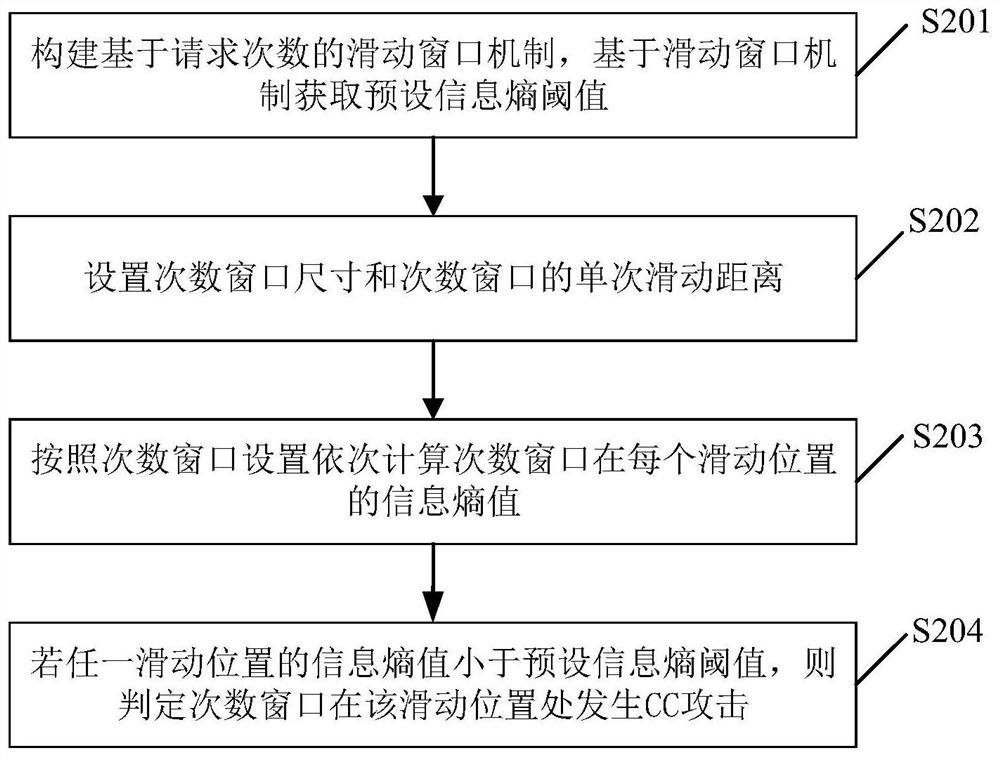
[0077] Such as figure 2 As shown, the embodiment of the present invention provides another CC attack detection method, which is applied in the field of network CC attack detection. The detection methods of this CC attack include:
[0078] Step S201, constructing a sliding window mechanism based on the number of requests, and obtaining a preset information entropy threshold based on the sliding window mechanism.
[0079] The sliding window mechanism can be established through machine learning; it should be noted that the preset information entropy threshold can be re-learned and tuned according to actual operating conditions.
[0080] Specifically, this step S201 includes the following steps:
[0081] 1. Obtain the preset number of requests during normal visits;
[0082] First, ensure that the detected server (or system) is under normal access conditions; then obtain the preset request times M of the server during normal access, and use the preset request times M as the win...
Embodiment 3
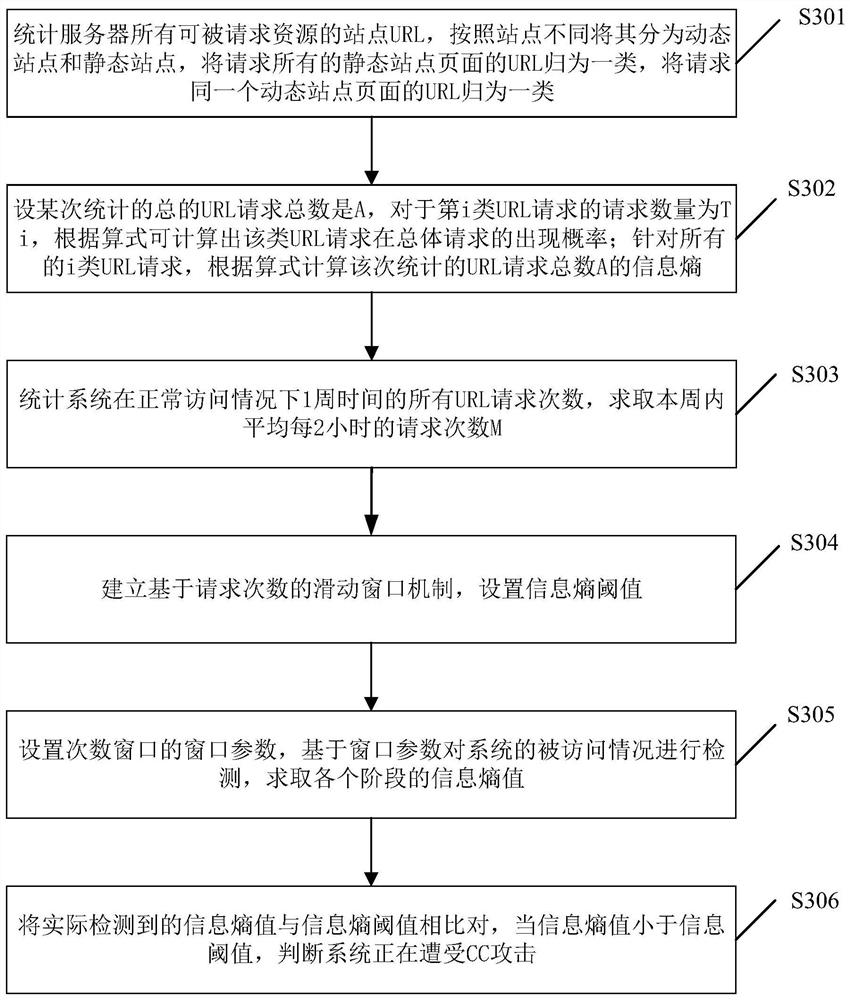
[0130] Such as image 3 As shown, the embodiment of the present invention provides a third CC attack detection method, including:
[0131] Step S301: Count all the site URLs of the server that can be requested resources, divide them into dynamic sites and static sites according to different sites, classify URLs that request all static site pages into one category, and group URLs that request the same dynamic site page grouped together.
[0132] In order to facilitate understanding, the following takes the web application server of XX official website as an example, and uses the packet capture tool to capture and analyze the data packets of external access requests, and classify the URL addresses of the received request texts:
[0133] Among them, the homepage address is http: / / www.dbappsecurity.com.cn / index.aspx, and the dynamic page name is index.aspx is classified into one category; the specific product page is: http: / / www.dbappsecurity.com .cn / pro_main.aspx? id=XXXXXXXXX...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com