File information leak-proof method, medium and equipment based on Hash algorithm
A hash algorithm and file information technology, applied in the field of information leakage prevention, can solve the problems of important information leakage and loss
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
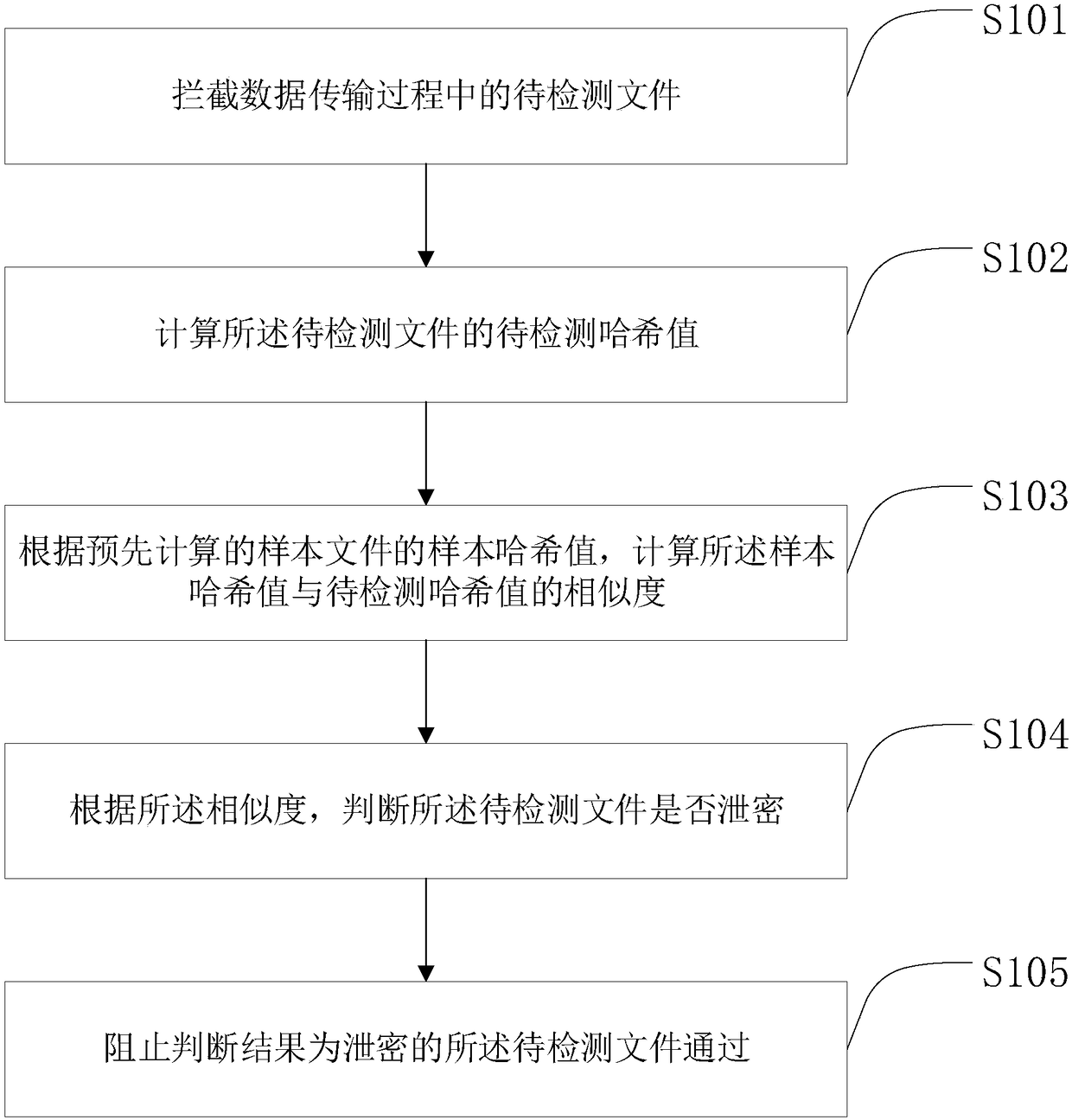
[0037] Please refer to figure 1 , figure 1 It is a flow chart of the information protection process in a hash algorithm-based file information leakage prevention method provided in the first embodiment of the present invention. The hash algorithm-based file information leakage prevention method provided in this embodiment includes information Protection process:
[0038] Step S101: Intercepting files to be detected during data transmission.
[0039] Step S102: Calculating the fuzzy hash value of the file to be detected;
[0040] Step S103: According to the pre-calculated sample fuzzy hash value of the sample file, calculate the similarity between the sample fuzzy hash value and the fuzzy hash value to be detected.
[0041] Step S104: According to the similarity, determine whether the file to be detected is leaked.
[0042] Step S105: preventing the file to be detected that is determined to be leaked from passing through.
[0043] Calculate the fuzzy hash value of the file...
no. 2 example
[0146] In the above-mentioned first embodiment, a file information leakage prevention method based on a hash algorithm is provided. In combination with the above-mentioned first embodiment, the second embodiment of the present invention provides a computer-readable storage medium on which is stored A computer program, when the program is executed by a processor, implements the method for redirecting an access request provided in the first embodiment above.
[0147] It can be seen from the above technical solution that the computer-readable storage medium provided by this embodiment can intercept the file to be detected in the data transmission process under the control of the processor, calculate the fuzzy hash value to be detected of the file to be detected, according to the pre-calculated The sample fuzzy hash value of the sample file, calculate the similarity between the sample fuzzy hash value and the fuzzy hash value to be detected, and then judge whether the file to be de...
no. 3 example
[0149] In combination with the hash algorithm-based file information leakage prevention method provided in the first embodiment, the present invention also provides a computer device, including: a memory, a processor, and a computer program stored in the memory and operable on the processor When the processor executes the program, the method for preventing leakage of file information based on a hash algorithm provided in the above-mentioned first embodiment is implemented.
[0150] It can be seen from the above technical solution that the computer device provided in this embodiment can intercept the file to be detected during the data transmission process, calculate the fuzzy hash value to be detected of the file to be detected, and according to the pre-calculated sample fuzzy hash value of the sample file, Calculate the similarity between the fuzzy hash value of the sample and the fuzzy hash value to be detected, and then judge whether the file to be detected is leaked accordi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com