Code static auditing device and method
A code and static technology, applied to code static review devices and fields, to achieve efficient solution, efficient discovery, and efficient code problems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
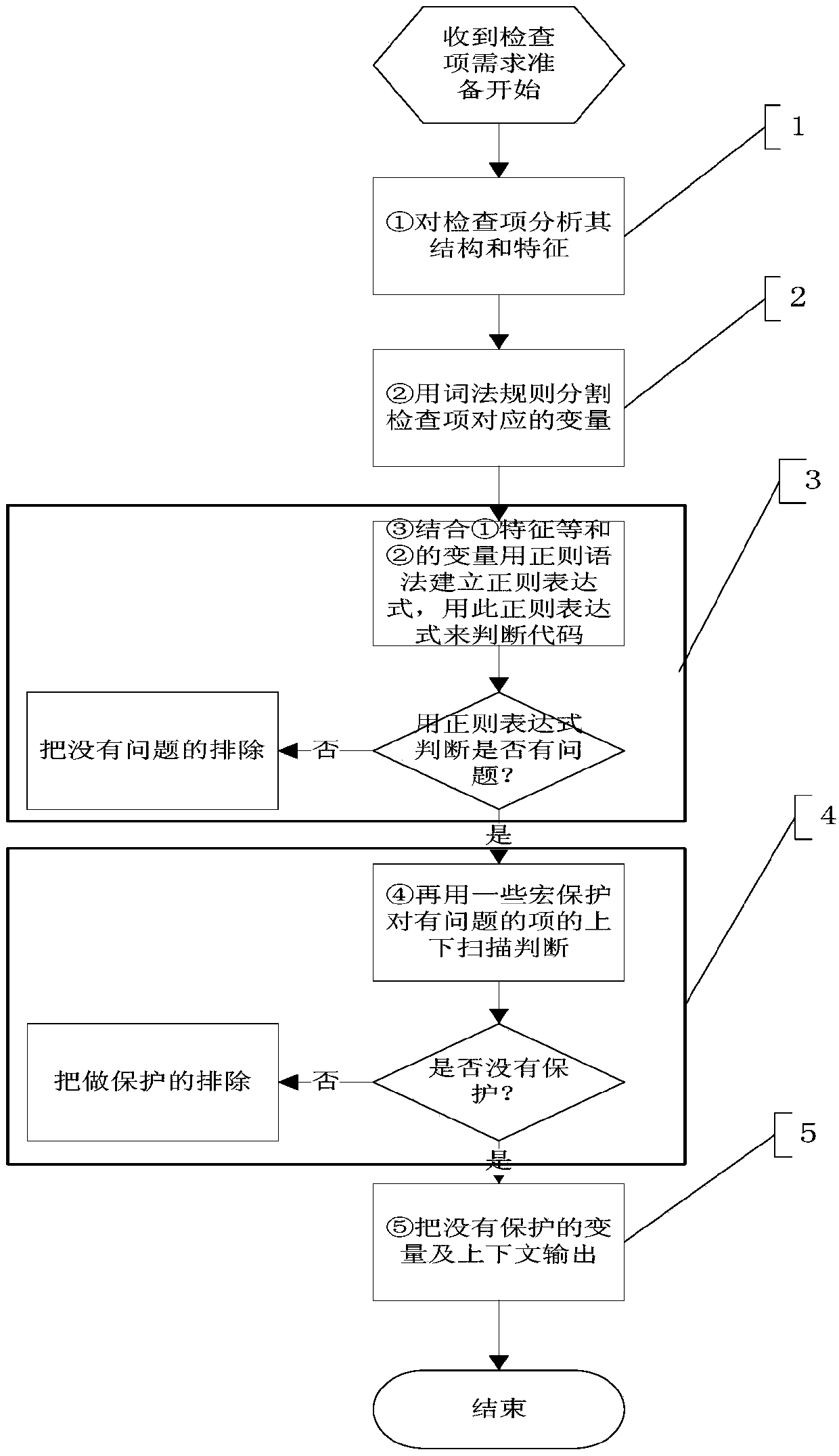
[0033] As an example for the [pointer not protected] check item, the audit method is as follows:
[0034] Step 1: Analyze and check items: According to the actual situation, the definition structure of the pointer is generally in the format of [type * pointer variable name], and there are common characteristics when there is a null pointer, that is, this [pointer variable] before use No protection was done.
[0035] Step 2: We need to check which are pointer variable names. According to the lexical rules, the first one to appear is the * symbol, followed by a string (starting with letters or underscores and starting with letters, underscores, numbers, etc.) String, this string is the required pointer variable name. For example, if such int*pXXX code statement is scanned, according to the above lexical description, after scanning *, the first one will be recorded, and a series of strings will appear after scanning *. The lexical rule that the two digits start to consist of le...
Embodiment 2
[0040] Take the [divisor protection] check item as an example, and the audit method is as follows:
[0041] Step 1: Analyze and check items: According to the actual situation, the definition structure of the divisor is generally in the format of [ / divisor variable name], and the problem of divisor protection has a common feature, that is, this [divisor variable] has no Make a judgment whether it is 0.
[0042] Step 2: We need to check which are the divisors. According to the lexical rules, the first occurrence of the / symbol is followed by a string (starting with letters or underscores and starting with letters, underscores, numbers, etc.) , this string is the desired divisor variable. Such as scanning to such a temp=nMax / nCount code statement, according to the above lexical description, after scanning to / , the first one will be recorded, and a series of character strings will appear after the scan / . The second digit at the beginning begins to consist of letters, undersco...
Embodiment 3
[0047] Take an example of the [Array subscript out-of-bounds protection] check item, and the audit method is as follows:
[0048] Step 1: Analysis and inspection items: According to the actual situation, the definition structure of the subscript is generally in the format of [[subscript variable name]]. The problem of subscript out-of-bounds protection has a common feature, that is, this [subscript variable] There is no value range judgment before use.
[0049]Step 2: We need to check which are subscript variables. According to the lexical rules, the first occurrence of the [ symbol is followed by a string (starting with letters or underscores and starting with letters, underscores, numbers, etc.) String, plus a ] symbol at the end, this string is the required subscript variable name. For example, after scanning such a vEveryKom[index] code statement, according to the above description, after scanning the [ symbol, start to record the first one, and scan a series of strings t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com