Encryption method for address list of mobile terminal, encryption device, and computer readable storage medium
A mobile terminal and encryption method technology, applied in the field of data processing, can solve the problems of economic loss and damage of mobile terminal holders, and achieve the effects of improving user experience, protecting privacy, and preventing leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
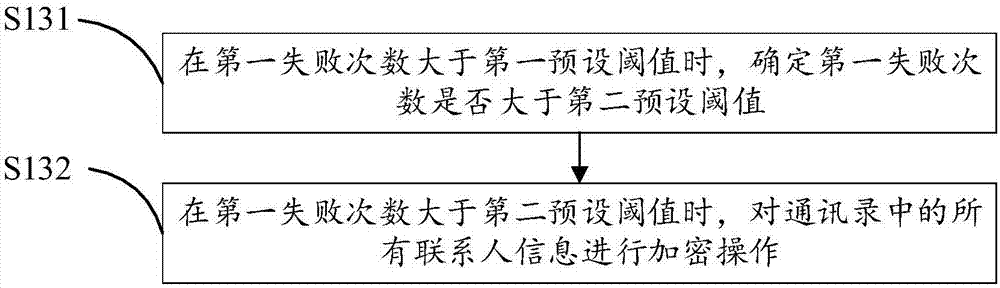
[0091] Based on the first embodiment, the second embodiment of the encryption method of the mobile terminal address book of the present invention is proposed, referring to image 3 , in this embodiment, step S130 includes:
[0092] S131. When the first number of failures is greater than a first preset threshold, determine whether the first number of failures is greater than a second preset threshold, wherein the first preset threshold is smaller than the second preset threshold;
[0093] The second preset threshold refers to a preset failure times set by the user that is greater than the first preset threshold, and is set by the user on the second preset threshold setting interface. Since the second preset threshold determines whether the user of the mobile terminal can see the limit of the number of failures of the contact information, the preset contact is not included, so the size of the second preset threshold can also affect the security of the screen unlock key, The sma...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com