Secure boot protection method, device, and computer-readable storage medium
A technology for secure startup and terminal security, applied in automatic switching offices, unauthorized/fraudulent call prevention, digital data authentication, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0030] It should be understood that the specific embodiments described here are only used to explain the present invention, not to limit the present invention.
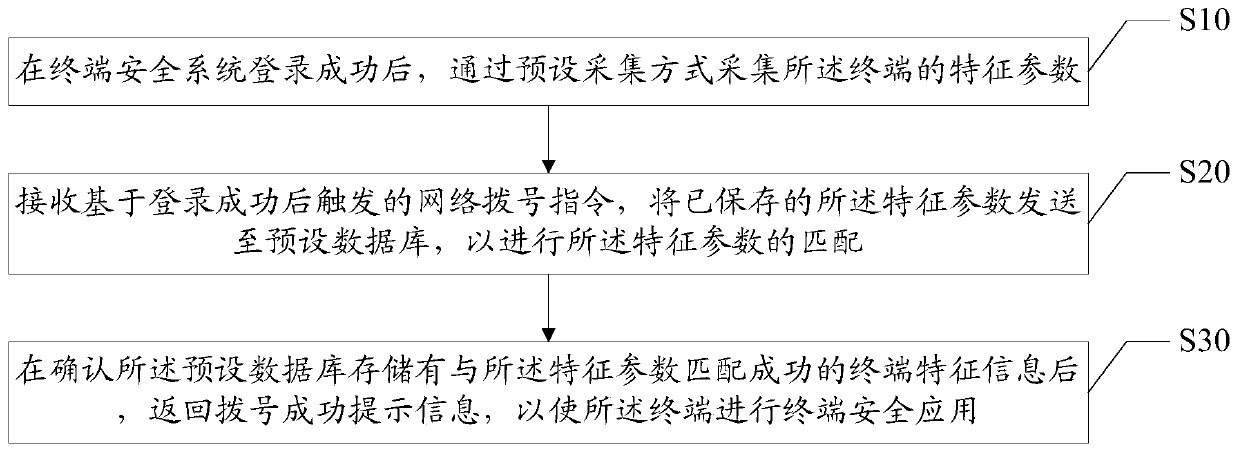
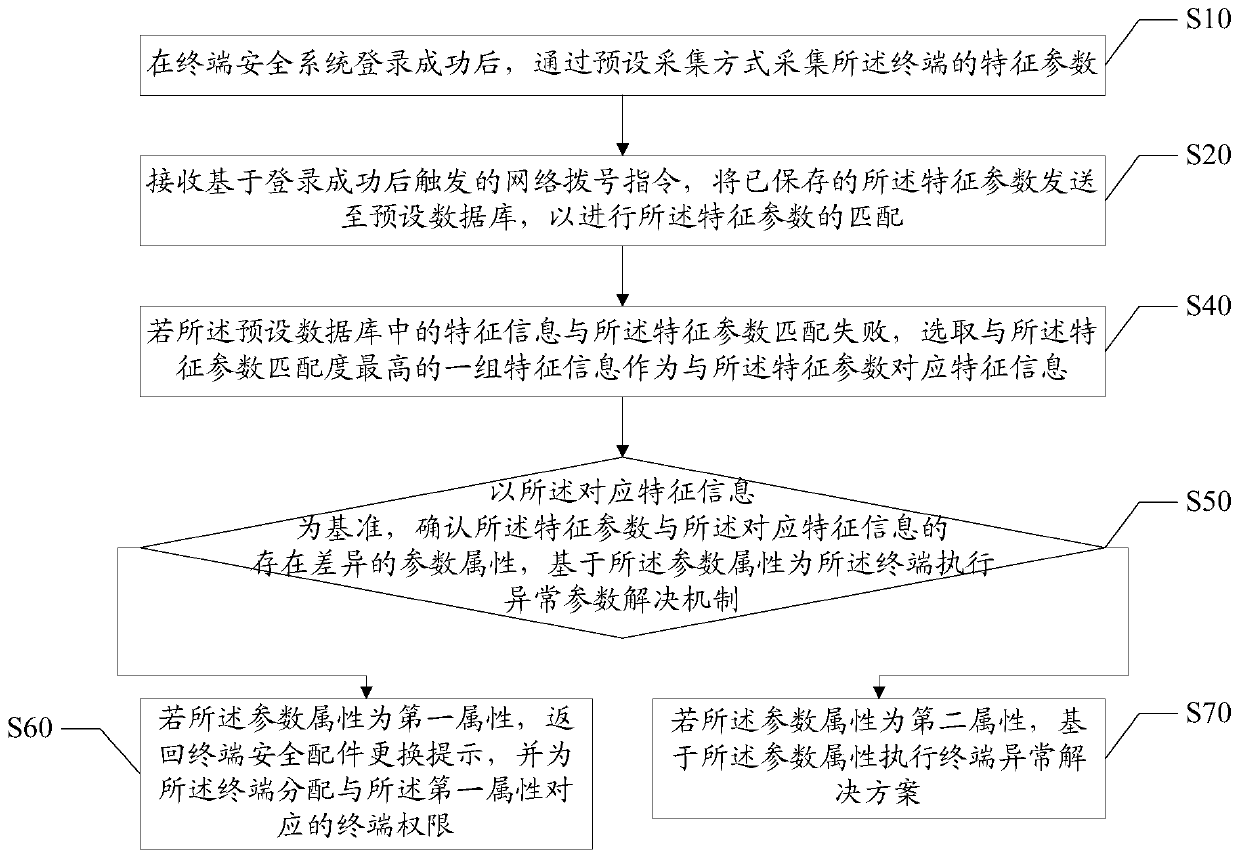
[0031] The main solution of the embodiment of the present invention is: after the terminal security system logs in successfully, collect the characteristic parameters of the terminal through a preset collection method; sending to a preset database to match the feature parameters; after confirming that the preset database stores terminal feature information that successfully matches the feature parameters, return a prompt message of successful dialing, so that the terminal can perform terminal security application.
[0032] Due to the prior art mobile police office terminal, there is no registration security mechanism and configuration related terminal security mechanism, because the police office needs to connect to the network, it is easy to be attacked by the network and used by outsiders, causing security informati...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com